How to Fight Fraud With Security Intelligence
Editor’s Note: Over the next several weeks, we’re sharing excerpts from the second edition of our popular book, “The Threat Intelligence Handbook: Moving Toward a Security Intelligence Program.” Here, we’re looking at chapter eight, “Threat Intelligence for Fraud Prevention.” To read the entire chapter, download your free copy of the handbook today.
A quick Google search of “top breaches in 2019” reminds us that no person or company is safe from — or immune to — risks in today’s digitally connected world. It also underscores the importance of contextualized security intelligence in helping individuals and organizations better understand who’s stealing data, how they’re doing it, what motivates them, and whether or not they have been exposed.
Think of a typical day in your life. Perhaps you wake up to the sound of your Alexa alarm, then — like 80% of people out there — you check your smartphone before even brushing your teeth. You wander into your kitchen to make breakfast, realize you’re out of milk and tell your smart fridge to add it to your grocery list. While sipping your coffee, you skim the day’s news on your tablet. After dashing out the door, you let your autonomous car navigate its way down the highway while you tap on your phone to turn off your house lights, lock your front door, and set the thermostat in your living room from afar. And that’s all before you even get to work!
All of these digital touch-points present opportunities for threat actors to steal your data and personal information. Consider that last year, in the first six months alone, there were 816 disclosed data breaches (up 54% from the first half of 2018), resulting in 4.1 billion records being compromised (up 52% from the first half of 2018). And those numbers will continue to surge, as one visit to the website “Have I Been Pwned?” reveals. Simply enter your email address to check against thousands of breaches over the past few years and see if yours was in one of the leaks.
While it’s impossible to shield yourself and your organization completely, digital risk can be managed by leveraging actionable intelligence to enhance your visibility into potential threats so you can limit exposure.
We explore how in the following excerpt from “The Threat Intelligence Handbook: Moving Toward a Security Intelligence Program,” which has been edited and condensed for clarity. Discover how cybercriminals organize themselves to execute fraud and extortion, how conversations in criminal communities present opportunities to gather valuable threat intelligence, and which types of cyber fraud you can combat by applying relevant intelligence.
Much like overpriced movie tickets and the ubiquity of high-fructose corn syrup in processed food, regular data breaches have become another disappointingly common aspect of life in the modern world. On December 3, 2018, the popular question-and-answer website Quora announced a data breach that may have resulted in the exposure of the personal information of as many as 100 million users. That breach is coming just days after hotel chain Marriott revealed that the personal information of up to 500 million guests had been stolen in data breaches that had gone undetected for years.
500 million people feels like an almost unfathomably large number. The world’s population right now is around 7.7 billion — that means that just in raw numbers, about one in 15 people were affected. When we consider how many people around the world wouldn’t have their data in Marriott’s databases — children, people who don’t travel or live in countries where Marriott doesn’t operate — we’re getting down to numbers where you could probably throw a rock in a crowded room with a good chance that you’ll hit someone affected by this one hack, making their day even worse than it already was.
And those statistics will keep rising, as one look at the website “Have I Been Pwned?” reveals. Simply enter in your email address to check against thousands of breaches over the past few years and see if yours was in one of the leaks. Try to scroll through the list of breaches included in the site’s database, and your finger will get tired before you get halfway through the bottom.
There doesn’t seem to be a way to opt out of this exposure, either, at least not unless you’re ready to take a vow of silence and commit yourself to a life of penitence at a mountaintop monastery. Some level of digital risk must now be accepted in an increasingly hybridized world — and the answer moving forward will not be to build higher walls, but more penetrating spotlights. To make this risk manageable, it’s becoming essential to develop an effective threat intelligence program that gives you advance awareness of who’s stealing data, how they’re doing it, what motivates them, and whether you and your organization have been exposed.
To that end, this chapter from our new book, “The Threat Intelligence Handbook,” focuses on how threat intelligence can be used to prevent fraud, looking at the context it provides and how it can give insights into the tactics, techniques, and procedures of criminal organizations.
The following chapter has been edited and condensed for clarity.
Stand and Deliver!
Since the birth of commerce, criminals have looked for ways to make an easy profit from those in possession of assets and to make the most of technology available at the time. In 17th century England, for example, the growth in coach travel among an affluent merchant class, combined with the invention of the portable flintlock pistol, gave rise to the highwayman.
In our digital age, companies that transact business online find their data targeted by various forms of cyber fraud.
To understand how criminals are looking to profit from your business, you cannot focus solely on detecting and responding to threats already actively exploiting your systems. You need to gather threat intelligence about the cybercriminal gangs targeting you and how they run their operations.
Know Your Enemy
Verizon’s 2018 Data Breach Report attributed more than 60 percent of confirmed breaches to organized crime.
This data aligns with intelligence gathered by Recorded Future from dark web communities showing that organized criminal groups (OCGs) are employing freelance hackers to defraud businesses and individuals. These groups operate just like legitimate businesses in many ways, with a hierarchy of members working as a team to create, operate, and maintain fraud schemes.
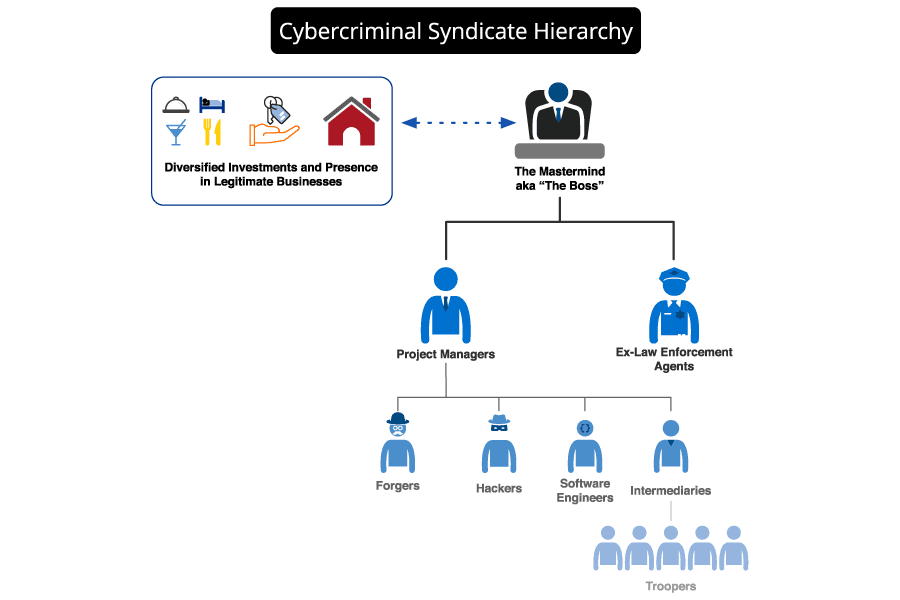
A typical organizational chart for a cybercrime syndicate. (Source: Recorded Future)
A typical OCG is controlled by a single mastermind. The group might include bankers with extensive connections in the financial industry to arrange money laundering, forgers responsible for fake documents and supporting paperwork, professional project managers who oversee the technical aspects of operations, software engineers who write code, and skilled hackers. Some groups include ex-law enforcement agents who gather information and run counterintelligence operations.
The members of these cybercriminal syndicates tend to have strong ties in real life and often are respected members of their social groups. They certainly don’t regard themselves as ordinary street criminals. They rarely cross paths with everyday gangsters, preferring to remain in the shadows and avoid attention from law enforcement and local mafia branches. However, schemes that require large numbers of people, such as those that involve taking cash out of multiple automated teller machines simultaneously, can involve a chain of intermediaries who recruit and manage the “troopers” who do the leg work.
Criminal Communities and the Dark Web
Only rarely can you attribute a cyberattack to a single individual operating in isolation. Advanced attacks typically require a wide range of skills and tools, as well as an infrastructure capable of launching and supporting campaigns that utilize ransomware, phishing, and other technical devices and social engineering techniques.
Today, all those products and services can be purchased or rented for a price in a sophisticated underground economy. Cybercriminals, hackers, and their accomplices exchange information and carry out transactions related to illicit activities on the deep web (areas of the web that cannot be reached by search engines) and the dark web (areas that can only be accessed with special software and tools that mask the identity of visitors).
Gated Communities
Not all cybercriminals operate exclusively in what would technically be referred to as the “dark web.” Some build communities based on a fairly standard discussion board, encrypted behind a login, and use technologies like Jabber and Telegram to conduct their business.
Prospective members of this underground network are vetted by active participants in chat rooms and forums before they are accepted. They may have to pay an entrance fee, ranging from $50 to $2,000, or more. One forum, for example, required prospective members to deposit over $100,000.
A Strength — and a Weakness
The dark web and criminal communities strengthen cybercriminals and OCGs by giving them access to information, tools, infrastructure, and contract services that multiply their power and reach. However, these communities are also a weakness because they can be monitored to provide threat intelligence that can be used to anticipate and defeat fraud schemes.
Connecting the Dots for Fraud Prevention
Threat intelligence gathered from underground criminal communities is a window into the motivations, methods, and tactics of threat actors, especially when this intelligence is correlated with information from the surface web, including technical feeds and indicators.
The power of truly contextualized threat intelligence is shown by how it can draw together data from a wide variety of sources and make connections between disparate pieces of information.
For example, the following contextual information might be used to turn news about a new malware variant into intelligence:
- Evidence that criminal groups are using this malware in the wild
- Reports that exploit kits using the malware are available for sale on the dark web
- Confirmation that vulnerabilities targeted by the exploit kits are present in your enterprise
Get 'The Threat Intelligence Handbook'
The full chapter of the book has much more information, including an extensive use case looking at the various techniques cybercriminals use to commit payment fraud and how threat intelligence can provide early warning of upcoming attacks. Download your free copy of the book now to see this use case and other helpful content.
Related