Threat Analyst Insights: The Impact of Indicting Foreign Nationals in Cyberespionage Cases
Background
Over the last few years, there have been a number of indictments of foreign nationals by the United States government for charges related to cyberattacks and cyberespionage activity. A few of the most notable examples include the March 2018 indictments of nine Iranians accused of conducting a massive campaign to steal data from universities and private companies on the orders of the Islamic Revolutionary Guard Corps (IRGC); the November 2017 indictments of three Chinese nationals who were working for the internet security firm Boyusec and were charged with espionage activity ranging from 2011 to 2017, targeting at least three corporate entities in the United States; and even more recently, the indictment of 12 Russian military officers suspected of participating in interference operations targeting the United States presidential election of 2016.
The activities cited in the indictments include targeted attacks against American universities, corporations, government entities, and political organizations. Based on the accusations, the motivation for these activities likely ranges from simply attempting to gather information that would grant economic or technological advantage, to gathering and distributing information to impact the outcome of elections. There is no consensus within the security industry and the media about the efficacy of these indictments as far as mitigating cyberespionage. Although these indictments seem to have a limited effect in many cases, they do have some utility — both practical and theoretical — in battling cyberespionage, which will be explored further below.
Limitations and Costs of Indictments
The media criticism and downplay of the effect of cyberespionage indictments is understandable. In most cases, those being accused are citizens of foreign nations that do not want them to be extradited to the United States to face prosecution. While the United States has extradition treaties with more than a hundred other countries, these are subject to a number of conditions in many cases. There are also potentially negative consequences to indictments, such as the public being given an unflattering impression of a nation’s ability to defend its own systems, rising diplomatic tensions, and the possibility of retaliatory cyber actions.
Problems With Extradition
In terms of the potential for actually bringing the targets of indictments to trial, there are dozens of countries that have no extradition agreement with the United States or have no diplomatic relations with the United States at all, making the retrieval of accused criminals from those nations nearly impossible through official channels. This list contains virtually all nations that are considered significant and primary cyber adversaries of the United States, such as Russia, China, Iran, and North Korea, raising the question of whether it is worthwhile to file indictments when there is little to no chance of an actual prosecutorial result.
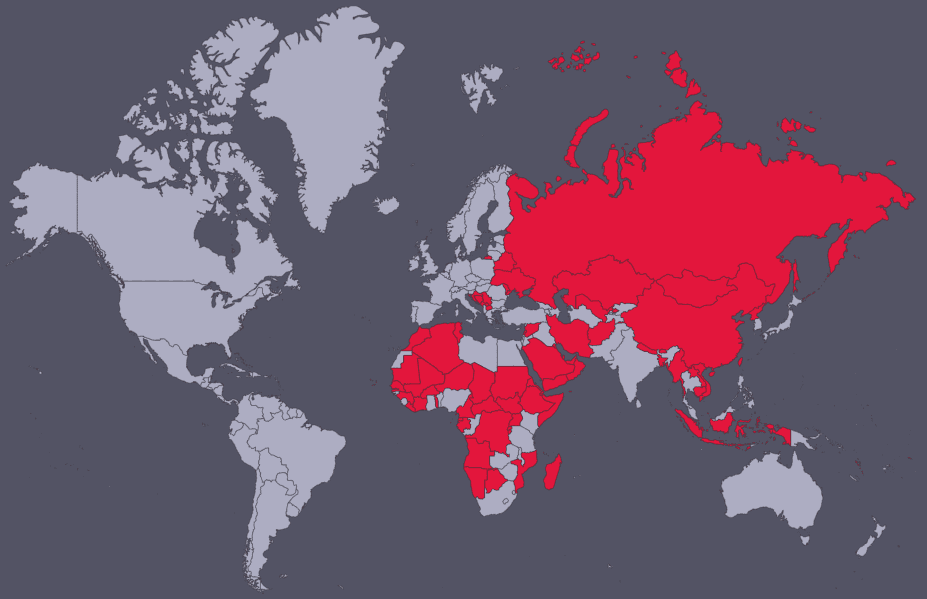
Nations with no extradition agreements with the United States illustrated in red.
Issues With Optics
Another concern is the foreign relations optics of acknowledging that a foreign power or criminal organization successfully targeted critical systems, including government networks. Whether or not it is a fair conclusion, detailed indictments could make government entities appear vulnerable on the world stage and among the targeted government’s own people.
Diplomatic Blowback
Another potential negative impact of leveling indictments against foreign nations could come in the form of diplomatic setbacks, and there is precedent for aggressive reactions to indictments in the past. In 2014, China reacted strongly to the indictments of Chinese nationals for cyberespionage by openly accusing the United States of hypocrisy and launching a formal complaint against the ambassador of the United States to China. China also withdrew from an anti-cybercrime committee in Washington, D.C.
The Threat of Retaliation
In addition to diplomatic blowback for raising indictments targeting foreign nationals, there exists a risk of retaliatory action on the cyber front. In a worst-case scenario, the indictment of a foreign national — especially one employed by the government — could prompt targeted attacks against United States government entities or American companies. This could take the form of state-sponsored activity or cybercriminal responses. It is easy to speculate that nations like China or Russia could respond with retaliation through state-sponsored entities, but it would be more reasonable to assess that while they have the resources and foresight to launch such operations, they are not likely to be so reactionary.
However, cybercriminal or hacktivist responses could be an issue if indictments are issued against nationals of countries where some pro-regime groups may take them as an affront against the national agenda. In this case, the activity would likely be lower-level attacks like website defacements or distributed denial-of-service attacks against infrastructure lacking protection, as seen in politically motivated attacks carried out by hacktivist groups such as Anonymous affiliates. While we have not observed direct evidence of retaliatory cyberattacks prompted by indictments, political motives among various attackers are common.
Positive Outcomes and Benefits of Indictments
Regardless of the sometimes disappointing prosecutorial reality of international cyberespionage cases, the resulting indictments do have utility aside from facilitating arrests and convictions. These can take the form of enhanced network security posture, geopolitical leverage, or other degradations of adversarial capabilities.
Increasing Public Awareness of Adversaries and Their Methods
Because indictments allow the government to publicly declare the results of investigations, one potentially positive result is the simple public exposure of the activity. This alone serves a few purposes, such as creating awareness about various threats and giving security professionals and executives information they might not otherwise have easily acquired about the activity of advanced threats.
Geopolitical Leverage
In addition to public awareness, indictments can be used as leverage on the geopolitical stage. Higher-profile indictments tend to deal with individuals in countries with which the United States has very complicated diplomatic relationships. The pressure created by public exposure of evidence that threat actors within such a country are targeting American organizations with cyberattacks can be leveraged to force public statements or denials, especially if the actors in question have ties to the governments of those countries, as was the case with the recent indictments of Russian intelligence officers. Russia dismissed those indictments as an attempt to disrupt an upcoming summit between Russia and the United States, continuing their denial of having interfered with the 2016 election in the United States.
While the impact of these political moves may be subtle, they are part of the diplomatic landscape and may affect public perception among citizens and at intergovernmental organizations. There also exist more practical uses for indictments. Going on the record with evidence sufficient to indict could also be used to justify or support geopolitical actions such as sanctions.
Mitigating Threat Actor Capability
Lastly, the unmasking of individuals involved in cybercrimes may decrease the ability of threat actors to carry out future activities. This could be done directly by more publicly exposing indicators and attack infrastructure in the form of evidence to enable organizations to better protect themselves, or indirectly by making it difficult for the accused to travel internationally. A formal charge against a foreign national restricts their ability to move throughout the world to nations that do have extradition agreements with the United States. Their names and personal details can be marked in customs databases, and if the accused passes through customs checks in cooperative nations, American authorities can apprehend them directly or in partnership with local authorities.
There are also financial implications, in that pressing charges against individuals ensures that they can’t move money into banks in friendly countries, let alone American banks. While these penalties may not be viewed as meaningful punishment when dealing with low-level threat actors, should higher-ups — especially government officials — be implicated in cyberespionage charges, the impact could be magnified greatly.
Wider-Reaching Implications
These indictments have implications for cyber threat intelligence professionals, security operations personnel, and leadership at various organizations. High-profile indictments, in some cases, only catch the attention of cyber news outlets and security company reporting, but there have been incidents that were covered nationally by mainstream news outlets. Either way, they are likely to prompt discussion internally at organizations among cybersecurity teams and senior leadership. This may cause shifts in current priorities with regard to threat tracking. Professionals can examine the details of a case and assess their organization’s vulnerability to targeting based on any vectors or methods disclosed in indictments or the targeting patterns of the accused threat actors.
Recorded Future can be used to easily construct queries that aid in the tracking of indicted malicious persons, their associated groups, and indicators of compromise tied to their malicious activities. One example can be taken from a Recorded Future query built to track Lazarus Group activity. An indictment was submitted on June 8, 2018 against alleged members of the group for illegally accessing computer systems in the United States.
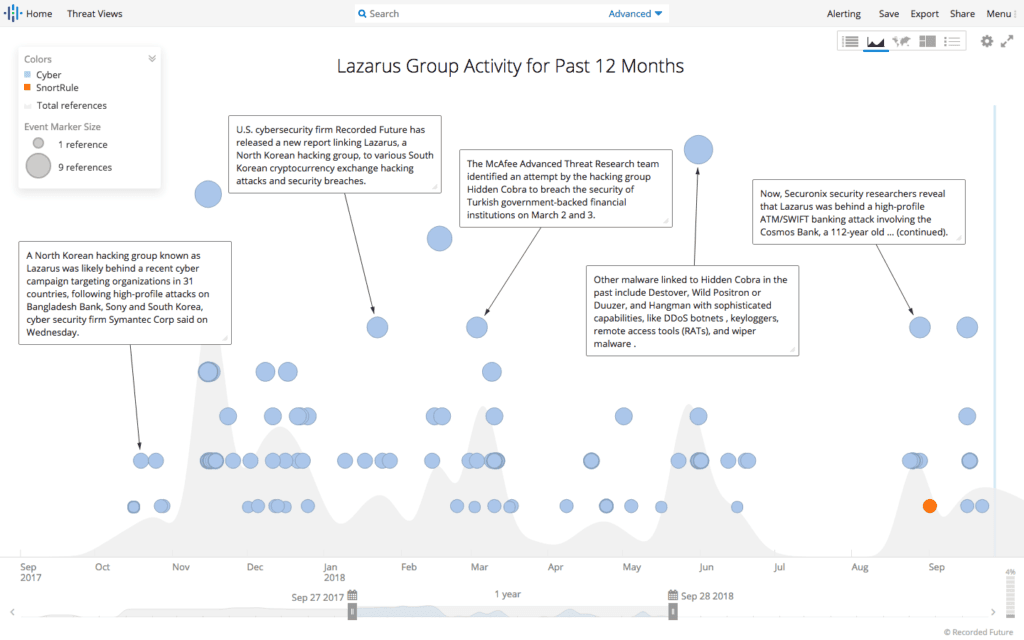
12-month timeline of Lazarus Group references collected by Recorded Future.
Additionally, we built another query to track the recent cyber activity and references regarding suspected Russia-backed groups APT28 and APT29, as well as the Russian Main Intelligence Directorate (GRU), which was as an organization named in the recent indictments related to cyberattacks intended to influence the 2016 presidential election in the U.S.
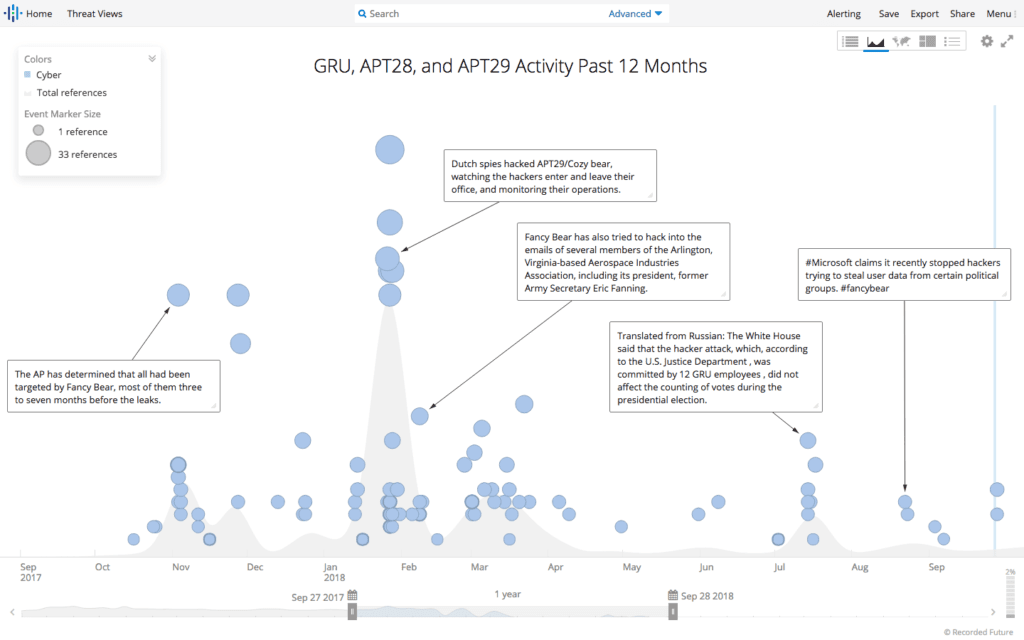
12-month timeline of APT28, APT29, and Main Intelligence Directorate (GRU).
These are just two examples of broad queries that can assist cyber intelligence and information security professionals in keeping tabs on relevant and developing advanced threats.
Related
