Threat Actors Remember the Vulnerabilities We Forget

Key Takeaways
- Threat actors continue to exploit older vulnerabilities because they are left unpatched and can represent easy targets.
- Threat intelligence gathered from Recorded Future reveals that around 19 percent of exploited vulnerabilities mentioned on the dark web in the last six months were more than a year old.
- With the growing use of smart devices like mobile phones and the various products making up the internet of things, expect old vulnerabilities to continue to be exploited. Many of these products are insecure and run old and outdated software.
In an industry so concerned with prognostication, it’s common practice to treat the newest vulnerabilities, exploits, and other threats as the ones most urgently needing attention. We talk about zero-day exploits in raised voices and rush to develop expertise in new technologies. Consequently, the result of this future bias is that older vulnerabilities in our systems are often ignored and left unpatched.
Many threat actors have no problem with taking an atavistic approach, however. Always looking for any opportunity to leverage a weakness, hackers will frequently target old vulnerabilities in new ways — or the same old ways, as long as they keep producing results.
The motivations for threat actors to continue exploiting old vulnerabilities are largely economic — these individuals and organizations are restricted by limited time and resources just the same as anyone else, and older exploits are often better understood and easier to target.
A recent assessment conducted by Recorded Future found that around one in five exploited vulnerabilities being discussed on various dark web forums in the last six months were over a year old. To take one example, CVE-2004-0113 was a little-known vulnerability in Apache web servers, but in June 2018, it was targeted by an exploit that would install a crypto miner for Monero — a distinctively contemporary application of a vulnerability that is positively ancient by cybersecurity standards.
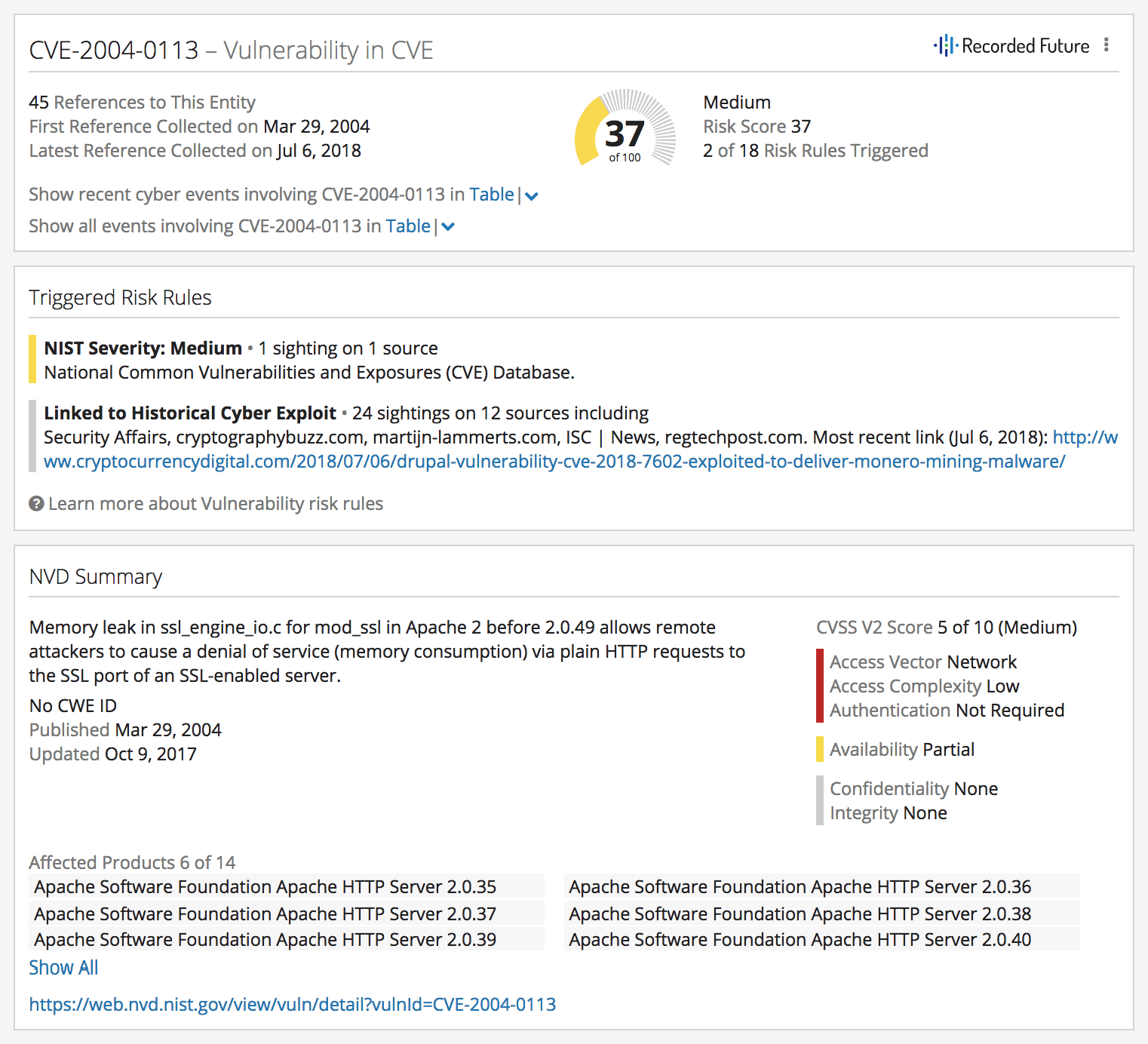
The CVSS score for the targeted vulnerability above was just five out of 10, suggesting only a medium risk (a recent analysis provides a deeper look at how the number of actually exploited vulnerabilities among those that are ranked medium and low is surprisingly high). Proofs of concept for older vulnerabilities like these regularly appear on code-sharing websites.
New Devices, Old Threats
Because of the proliferation of mobile devices and the motley assortment of devices that represent the internet of things, there’s good reason to bet that the targeting of older vulnerabilities will continue and even grow. Smart devices with WiFi access are appearing in just about every conceivable application and environment, from our cars to our kitchens, and there’s little in the way of consistent standards or security protocols for these devices. Many run on basic versions of Linux without any endpoint protection or access the internet through public networks.
The expected application of many IoT devices is at odds with the typical three-to-five-year lifecycle of other hardware running Linux, like servers and laptops. Updating your hardware will also update your software, of course, but in the meantime, patching is generally done on regular cycles to mitigate the cost of downtime and the risk of disrupting reliability. No matter what, seeking out vulnerabilities and patching them is a process that takes a lot of time and effort and comes with its own risks — and it isn’t a process that scales easily. Introducing tens or hundreds of new internet-connected devices into a network, each representing a point of access to that network that will require its own maintenance, represents a huge new risk that cannot be safely managed with the same methods.
The same goes for mobile phones, especially those running Android. The most popular operating system for mobile devices in the world with over two billion monthly users, Android is a modified version of Linux, and its open source nature means countless devices are running versions that are themselves modified or outdated. Most of these devices are being managed by individuals, not institutions. Even a perfectly managed network can be placed at risk by employees who connect their unsecured phones to the company’s WiFi, opening the door to the theft of corporate data, emails, and bank accounts.
The risks represented by these devices are not hypothetical — the group of vulnerabilities that constitute the Stagefright bug, which affects older Android devices, remains a hot topic in dark web forums. Threat actors recognize the opportunity that a high number of unpatched devices presents. The CVEs of Stagefright are considered critical by the National Vulnerability Database (NVD), but again, older mobile devices are frequently left unpatched because they are usually managed by individuals, not organizations undergoing a regular evaluation of their vulnerabilities and prioritizing the critical ones.
Using Threat Intelligence to Catalog Threats More Effectively
These old vulnerabilities are like outdated library books sitting dusty on the shelf. Forgotten by most and outshone by the new bestsellers, they can nevertheless be potent portals to hidden knowledge that can be exploited by anyone who’s willing to do the research.
There just isn’t enough time to patch every vulnerability that shows up in your network, and there’s no need to do that, either. A small number of vulnerabilities make up an outsized share of the ones that are actually exploited. This means that many vulnerabilities can safely be left unpatched for an indeterminate length of time, even if they represent a high technical risk of exploitability.
Environmental factors — like whether a vulnerability is being actively exploited by malware — have an enormous effect on risk, and these factors are difficult or impossible to identify without threat intelligence. A threat intelligence solution that draws on sources like chatter on dark web forums or monitors code repositories for examples of code that target a specific vulnerability will help alert you to whether a vulnerability you’ve left unpatched because it was previously a low priority is becoming a bigger risk. Supplementing your security program with threat intelligence can enable you to move beyond a regular schedule of patching to one that keeps you more up to date without taking more time and effort.
To learn more about how real-time threat intelligence can bring you invaluable insight into vulnerabilities that are being actively exploited, download our free white paper, “Vulnerability Intelligence From the Dark Web: The Disclosure to Exploit Risk Race.”
Related