Applying Threat Intelligence to the Diamond Model of Intrusion Analysis
As an analyst, you may have come across various threat models in your career. In the cybersecurity and threat intelligence industries, the cyber threat intelligence cycle plays a crucial role alongside several approaches used to analyze and track the characteristics of cyber intrusions by advanced threat actors. One popular approach is the Diamond Model of Intrusion Analysis.
What is the Diamond Model of Intrusion Analysis?
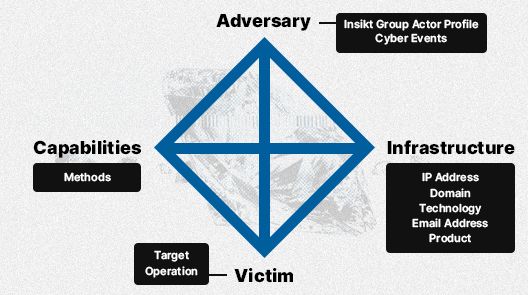
The "Diamond Model of Intrusion Analysis" was initially introduced by Sergio Caltagirone, Andrew Pendergast, and Christopher Betz in a technical report for the U.S. Department of Defense in 2013. In their own words: “The model establishes the basic atomic element of any intrusion activity, the event, composed of four core features: adversary, infrastructure, capability, and victim”.
This model emphasizes the relationships and characteristics of four basic components: the adversary, capabilities, infrastructure, and victims. The main axiom of this models states, “For every intrusion event, there exists an adversary taking a step toward an intended goal by using a capability over infrastructure against a victim to produce a result.” This means that an intrusion event is defined as how the attacker demonstrates and uses certain capabilities and techniques over infrastructure against a target.
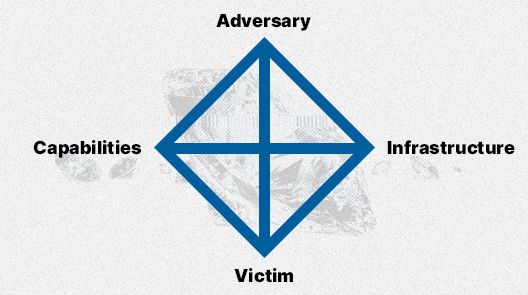
Adversary
Understanding the adversary is pivotal in decoding the threat landscape in the model of intrusion analysis. It dives into the who and why behind cyber attacks, illuminating the motivations and entities involved. This understanding enables security teams to better predict and prepare for cyber threats. The following points elaborate on this aspect:
- Origin: What is the geographical or organizational origin of the attack organizations?
- Identity: Who are the individuals or activity groups behind the attacks?
- Sponsorship: Are there any entities sponsoring or endorsing the attackers?
- Motivation: What drives the attackers to initiate the attack?
- Timeline: What is the timeline of the attackers' activities, including planning and execution?
Infrastructure
Unveiling the infrastructure employed by attackers exposes the technical backbone of malicious operations. This encompasses the compromised systems, command and control servers, and data management tactics, acting as the logical communication structures for the operations. The details are as follows:
- Compromised Systems: Identify the computers or networks that have been compromised.
- Command & Control (C2) Domains: What domain names are being used for command and control?
- C2 Server Locations: Where are the command and control servers situated?
- C2 Server Types: What types of servers are employed for command and control?
- C2 Mechanism and Structure: Detail the structure and mechanism of the command and control setup.
- Data Management and Control: How is the incoming data being managed and controlled?
- Data Leakage Paths: Identify the paths through which data leakage occurs.
Capability
Evaluating the capability of attackers provides insight into their skill set and sophistication. This assessment is crucial for security analysts to develop proactive countermeasures against potential threats. The specifics are highlighted below:
- Reconnaissance Skills: What capabilities do the attackers possess to conduct reconnaissance?
- Attack Delivery: How proficient are the attackers in delivering their attacks?
- Exploit and Vulnerability Utilization: How adept are they at exploiting vulnerabilities?
- Malware and Backdoor Deployment: What skills do they have in deploying remote-controlled malware and backdoors?
- Tool Development: How capable are they in developing and refining their tools for attack?
Target
Identifying the target underscores the attackers' ultimate objective. It covers the geographical, industrial, individual, and data spheres in the crosshairs of malicious activities. Knowledge management and threat data gathered here can be shared via threat intelligence exchange protocols to bridge intelligence gaps. The following elements shed light on this aspect:
- Target Geography: What specific countries or regions are targeted?
- Industry Sector: Are there particular industry sectors in the crosshairs?
- Individual Targets: Are certain individuals or profiles being specifically targeted?
- Data Targeting: What types of data are the attackers after?
Across these facets, the Diamond Model intersects with other planning frameworks like the linear Cyber Kill Chain Model to extend a multidimensional view. By integrating meta features and contextual indicators into the analysis, security professionals can establish clear linkages between the different components of a cyber attack, from initial reconnaissance to eventual data exfiltration.
The process also entails devising mitigation strategies based on the analysis of activity threads and diamond events, which in turn refines the external attack surface management. Central to this model is the focus on centered approaches that enhance the incident response through better detection mechanisms and threat information sharing. This comprehensive approach not only addresses the immediate threats but cultivates a culture of continuous improvement and adaptation in the face of evolving attack surface threat landscapes.
Exploring Real-World Applications of the Diamond Model of Intrusion Analysis
Analyzing FIN8's Attack on Financial Institutions: A prime example of the Diamond Model in action is its application in unraveling the strategies of the FIN8 hacking group. Investigations uncovered that FIN8 leveraged PowerShell scripts as their attack infrastructure, deploying a sophisticated "Sardonic Backdoor" as their primary capability. This targeted attack on financial institutions highlights a critical 'diamond event' in the model, fitting neatly into the Execution/Persistence phase of a cyberattack's lifecycle.
Dissecting LAPSUS$ Ransomware by Meghan Jacquot and Kate Esprit: In a significant case, cybersecurity analysts Meghan Jacquot and Kate Esprit utilized the Diamond Model to decode the operations of the LAPSUS$ ransomware and hacking group. They identified key components of LAPSUS$'s strategy: using open-source hacking tools, Telegram, and underground forums as their infrastructure; skills in social engineering, DDoS attacks, and credential theft among their capabilities; with victims predominantly in telecommunications, software, technology, and gaming industries.
Carnegie Mellon University's Honeynet Project: The study “Using Honeynets and the Diamond Model for ICS Threat Analysis'' by John Kotheimer, Kyle O’Meara, and Deana Shick at Carnegie Mellon University offers another insightful application. Their focus was on how adversaries interact with honeynets in industrial control systems. By applying the Diamond Model, they successfully mapped these interactions, providing a comprehensive view of the attack strategies used in these specialized environments.
These examples underscore the versatility and efficacy of the Diamond Model in providing a structured approach to analyzing and understanding diverse cyber threats, a crucial tool in the arsenal of today's cybersecurity professionals.
Why does it matter for security teams?
Understanding the Diamond Model of Intrusion Analysis is crucial for security teams as it provides an analytical framework to dissect cybersecurity incidents. By delving into the adversary's infrastructure and understanding the general class of attackers, including malicious insiders, it offers a cognitive model that enriches the analytical workflow. The model's core features provide a lens to scrutinize various aspects of cyber threats, enabling a more strategic mitigation approach.
It also identifies specific elements like e-mail addresses used in attacks, shedding light on the technology enabling these threats. This analytical process is a valuable tool for developing a tailored mitigation strategy, transitioning teams from reactive measures to a more proactive stance in combating cyber threats. Hence, the Diamond Model becomes an integral part of the security protocol, providing a structured method to analyze and respond to threats in a more informed manner.
How can organizations stay protected using the Diamond Model of Intrusion Analysis?
Using Recorded Future, it is possible to uncover additional details about the adversary, infrastructure, capabilities, and victims in order to piece together a more cohesive picture of the threat and how that threat operates. These additional data points can complement internal data and other intelligence in correlating and attributing malicious activity to an adversary.
By looking at a threat actor Intelligence Card™ in Recorded Future, we can see that this entity qualifies as the adversary component of the Diamond Model quite nicely. For example, the Dark Caracal Intelligence Card™ (below) shows us information about this adversary, including name, any nation-state affiliations, and analytical notes added in by the Insikt Group.
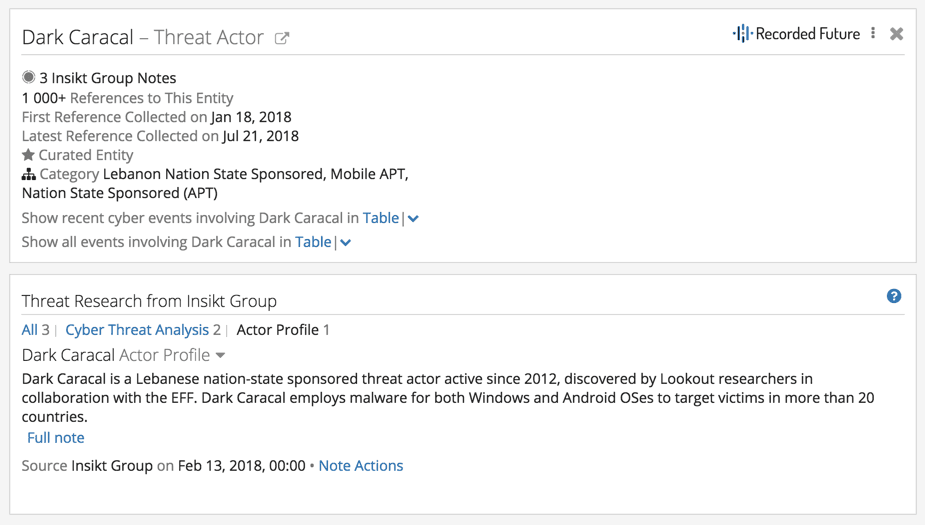
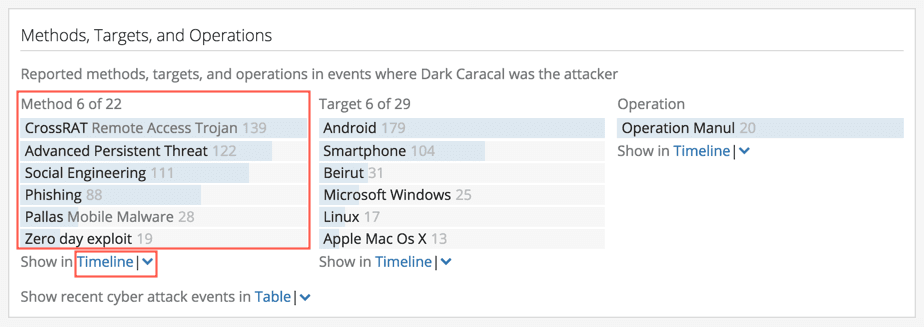
The Diamond Model threads adversaries with developing capabilities and techniques that are unique to that group. In Recorded Future, the Methods context directly translates to the Capabilities edge of that model. As shown below, it’s obvious that this adversary uses distinct malware and attack vectors as part of its capabilities and TTPs (tactics, techniques, and procedures). We can study additional capabilities by clicking the Timeline link below the Methods list to get a temporal visualization of the capabilities leveraged.
Adversaries also operate within an infrastructure to conduct their intrusions. This infrastructure can be composed of IP addresses, domains, botnets, and technologies in general. In our example, we can see that Dark Caracal is associated with a combination of indicators. As a starting point, these entities represent possible infrastructure and should be immediately correlated with internal network data to qualify intrusion investigations. A scenario would be seeing compromised Android devices connected to the corporate network communicating with command-and-control (C2) servers. The Technology, IP Address, Domain, Product, and Email Address sections of the Context in the Dark Caracal Intelligence Card™ can be used to describe part of that infrastructure, as shown below.
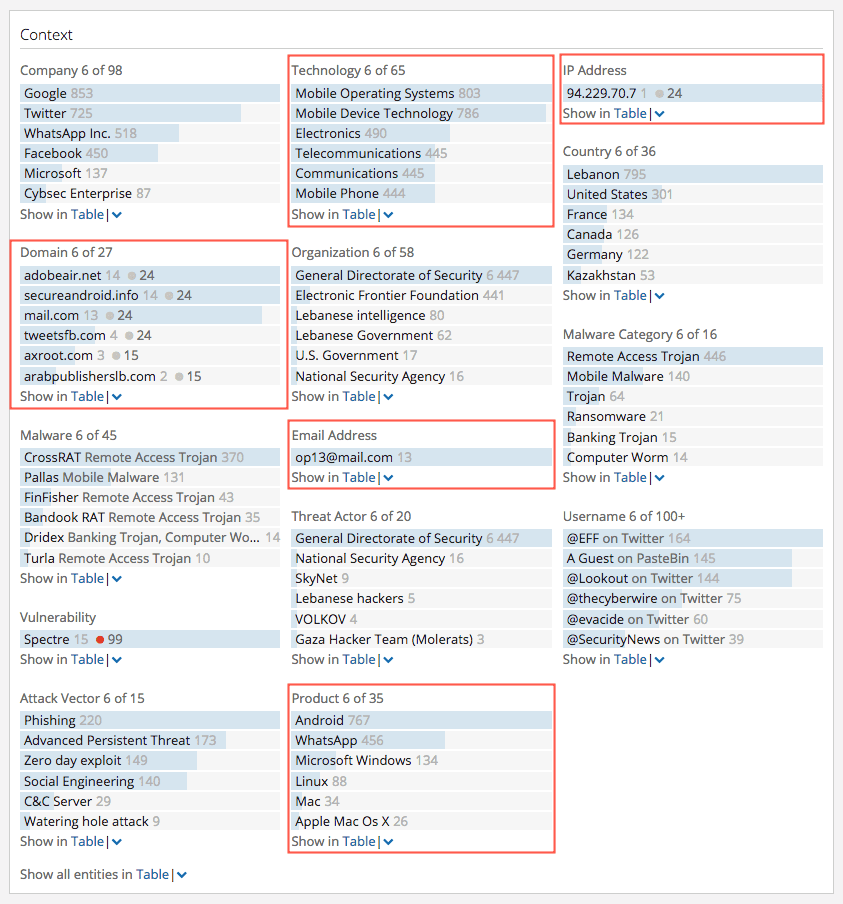
Finally, we can attribute the victims component of the Diamond Model using a combination of the Target list and any associated Operations. Threat actors who are affiliated with nation states often have an objective that is different than those of non nation-state actors. The main differentiator here is that nation-state threat actors display advanced persistence and are not directly motivated by financial gain — rather, they conduct their operations over a long period of time to extract intelligence in support of larger objectives. Therefore, any targets and operations should be looked at more closely to determine who the victim ultimately is. In our example, we see that several targets and one operation are listed in the Methods, Targets, and Operations section of the Intelligence Card™.
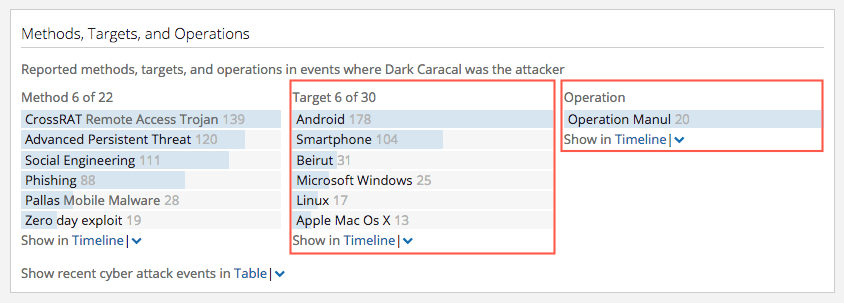
Although some of the targets include technologies and products, a close examination of the operation “Operation Manul” reveals that journalists, lawyers, activists, and government institutions were targeted. Therefore, it makes sense that the threat actor targeted physical devices and products as a means to compromise those victims.
In short, you can use Recorded Future to complement cyberattack analysis frameworks such as the Diamond Model of Intrusion Analysis. By looking at several parts of the threat actor Intelligence Card™, we can leverage open sources to help analysts piece together a more complete view of campaigns and track their evolution in the hopes of avoiding and mitigating potential attacks in a more proactive way.
This article was originally published Jul 25, 2018, and last updated on Feb 5, 2024.
Related
