DD4BC, Armada Collective, and the Rise of Cyber Extortion
DD4BC, a group that named itself after its extortion method of choice — DDoS “4” Bitcoin — has attacked over 140 companies since its emergence in 2014. Other groups, inspired by their success, are jumping on the bandwagon. Is this form of extortion here to stay?
Analysis Summary
- DD4BC’s success has attracted copycats.
- Some forms of cyber extortion have very low barriers of entry.
- Armada Collective initially focused its attacks on secure email providers.
- Additional groups may attack when a company publicly discloses that it’s being hit by a DDoS extortion attack.
- Other groups may be using the Armada Collective name.
Beginning in the second half of 2014, a group named DD4BC emerged, and attempted to extort a wide variety of companies largely in the financial services sector. The group would first send an email to the victim warning of a distributed denial-of-service (DDoS) attack capable of 400–500 Gbps unless a certain amount of bitcoins were received by a predetermined deadline. A “warning” attack was often simultaneously initiated, typically 10–15 Gbps and thought to test defenses.
Although the group is not historically capable of producing a 400–500 Gbps attack, the threat is real. According to Akamai, as of July there have been 141 confirmed attacks by the group, but only with an average peak bandwidth of 13.34 Gbps.
However, shortly after the Akamai case study was published and the resulting DD4BC publicity in September, reported attacks seemed to decrease sharply.
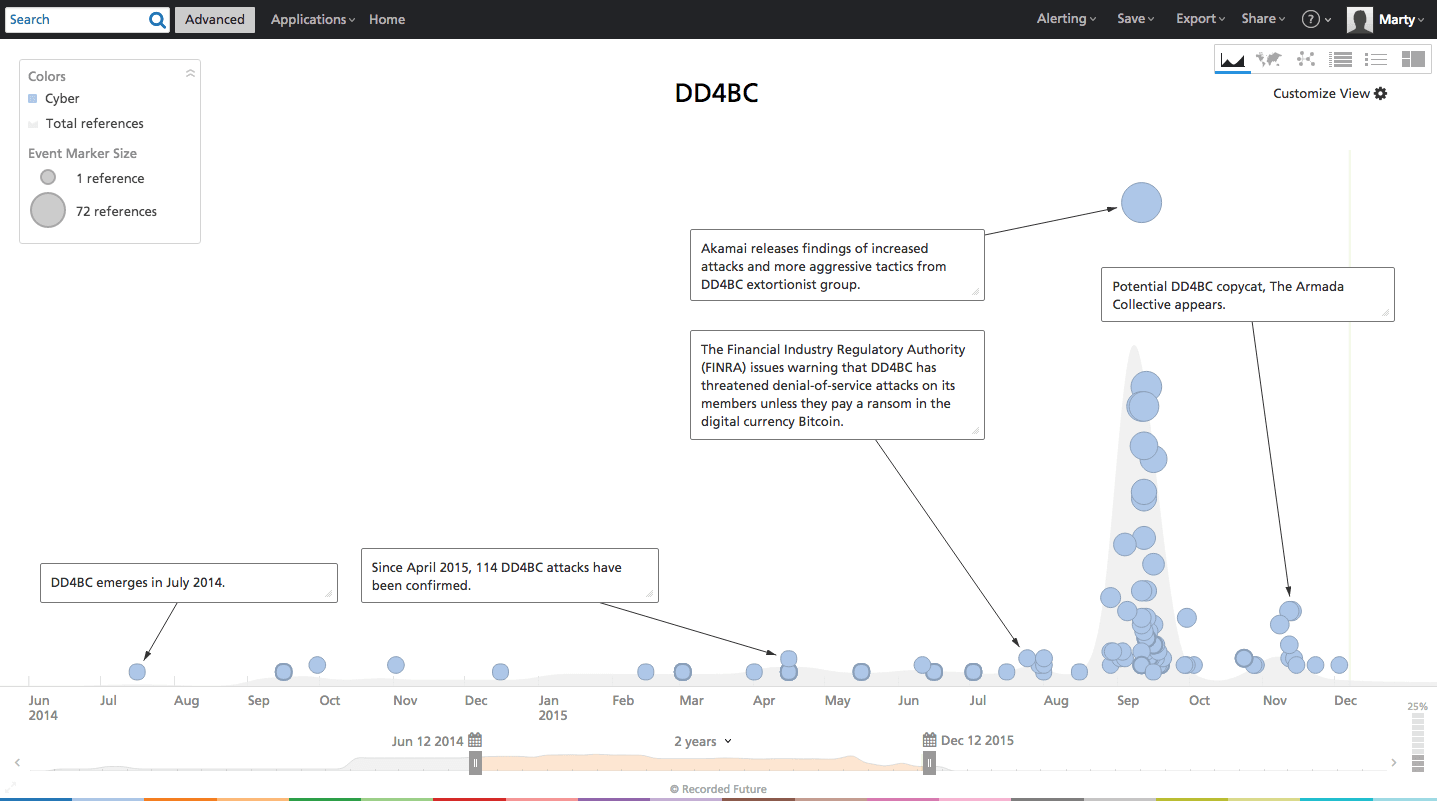
Shortly after, a new group calling themselves the “Armada Collective” appeared. The tactics used by the Armada Collective are almost identical to DD4BC — threatening victims via email with a DDoS attack unless a bitcoin ransom is paid. In fact, initial speculation led many to believe that this was the DD4BC group performing under a new name. However, it appears more likely that the publicity surrounding DD4BC has done two things: (1) potentially cause DD4BC to scale back attacks in fear of being caught, and (2) prove the model works, attracting copycats.
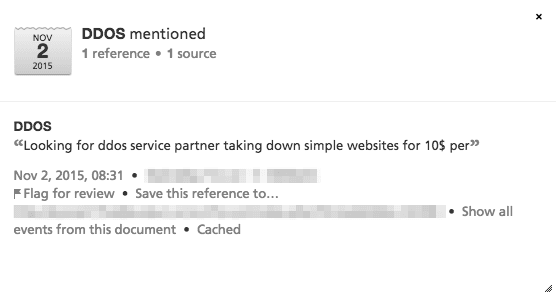
The ability to perform DDoS attacks through “stressers” and “booters” — essentially paid access to botnets – has been around for quite some time, and are easy to use. But with the maturation of bitcoin — an unregulated, anonymous, online-only currency — actors now have an easy way to demand payment, with little fear of it being traced back to them. The ability to perform these relatively simple attacks for ransom is now getting the attention of “script kiddies.”
In fact, Recorded Future analysis found several requests on the dark Web for instructions on how to perform DDoS attacks and set up bitcoin wallets, primarily appearing since the recent DD4BC publicity.
Several script kiddies are also working the extortion angle in other methods of attack as well. In the recent TalkTalk breach, we documented a history of security issues revolving around cross-site scripting vulnerabilities (a favorite of script kiddies). Whether or not the hack was directly related to the vulnerabilities or not is to be determined; however the CEO stated that after the hack, the attacker demanded a ransom. All four suspects that were arrested (and bailed) were very young — 20, 16, 16, and 15 years old.
What is curious about recent attacks by the group that refers to themselves as the “Armada Collective” is not only their initial targets of choice — private email providers — but also what happened when one provider paid the ransom.
ProtonMail, an encrypted email service founded at CERN in response to the public disclosure of the NSA’s widespread email interception, was one of several providers hit by DDoS attacks by Armada Collective. Due to the nature of their business, a public statement was made that they were under a DDoS extortion attack, and thus functionality was affected. After pressure from other companies sharing the same data center, ProtonMail paid the ransom requested.
However, the attacks continued — and at a much more sophisticated level. ProtonMail claimed this second attack was a “coordinated assault on our ISP exceeded 100Gbps and attacked not only the datacenter, but also routers in Zurich, Frankfurt, and other locations where our ISP has nodes.” In fact, ProtonMail has stated that the second attack appears to be nation-state sponsored.
The Armada Collective vehemently denied involvement in this second attack, despite their own warnings of a larger attack. They even refunded bitcoins to ProtonMail in order to send messages such as:
“Somebody with great power, who wants ProtonMail dead, jumped in after our initial attack!” and, “WE DO NOT HAVE THAT POWER! NOT EVEN CLOSE.”
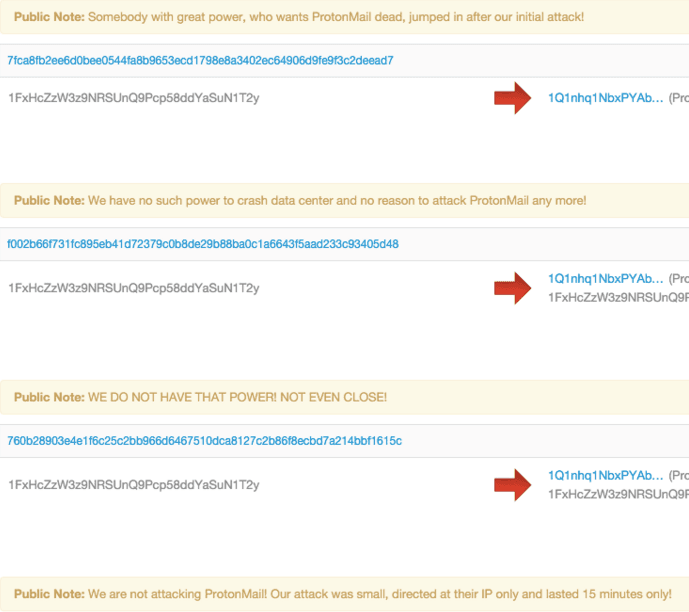
This fits in line with most analysis of both DD4BC and Armada Collective — the groups do not possess the ability to perform the level of DDoS attacks they claim to be able to. The frantic messages Armada Collective sent back to ProtonMail seem to indicate they fear getting caught, perhaps sending the group into hiding just as DD4BC before it.
It has long been known that DDoS attacks are often distractions for a more sinister attack. By choosing companies that disclose when service is disrupted, such as email providers, the Armada Collective is — knowingly or not — allowing other attackers to ride in on their coattails while disclaiming responsibility.
However, something interesting happened recently — three banks in Greece were targeted by a group that called themselves the Armada Collective. But one thing was very out of the ordinary — the ransom. Typically, a ransom from either DD4BC or the Armada Collective has been around 10–200 BTC (roughly $3,600 to $70,000 USD). The idea behind this relatively low extortion is thought to pressure more companies to simply pay the ransom, rather than deal with potential downtime.
But the ransom for these banks was much higher — 20,000 BTC — about $7.2 Million. This extremely high ransom, in combination with the messages sent back to ProtonMail, strongly suggests that somebody may be using the Armada Collective name in order to appear more legitimate. In this particular case, no bank paid the ransom, and DDoS protections were put in place — negating future attempts to bring down the sites.
Nevertheless, the DDoS threat landscape continues to evolve. While cyber extortion has been around for quite some time, the adoption of bitcoin as a method of ransom will continue to attract new miscreants into the DDoS space.
Related
