Effective DarkComet RAT Analysis in 10 Minutes and 3 Clicks
Key Takeaways
DarkComet RAT controller identified via a Recorded Future and Shodan alert.
10 minutes and three Recorded Future Intelligence Cards™ (including embedded Farsight Security and ReversingLabs insight) produced a substantial lead toward probable cause and a successful criminal investigation.
IP Address: 73.77.225.59:1604 (Comcast Cable, Texas)
Associated Domain: shadows.sytes[.]net (No-IP Dynamic DNS)
Malware: b5462c4312a587171c400953f8fd79f0 (MD5)
In 2015 we released a report on identifying known RAT (remote access trojan) controllers. Malicious IP addresses are continuously identified through proactive internet scanning (via Shodan) for known family signatures, like Poison Ivy and BlackShades. This year we created Recorded Future Intelligence Cards™ for common indicators that make analysis a breeze, and RAT controllers are a perfect example.
Threat actors use RATs to remotely record audio and video from a victim’s web camera and/or microphone — suspects often attempt extortion of vulnerable women after the RAT is installed on the victim’s computer. Also, many RATs are capable of keystroke logging and file exfiltration.
The computer located at 73.77.225.59 (Comcast Cable) is hosting a DarkComet RAT controller (in RAT nomenclature the malware on a victim’s system is referred to as the “server” and the suspect’s control panel is referred to as the “client”). Legal process for subscriber records sent to Comcast and No-IP will provide further information toward probable cause.
Additionally, a pen register for 73.77.225.59 may assist with identifying victims that are infected with this particular instance of DarkComet.
Analysis
On September 6, 2016, Recorded Future and Shodan produced an alert for a new DarkComet trojan (malware) controller located at 73.77.225.59.
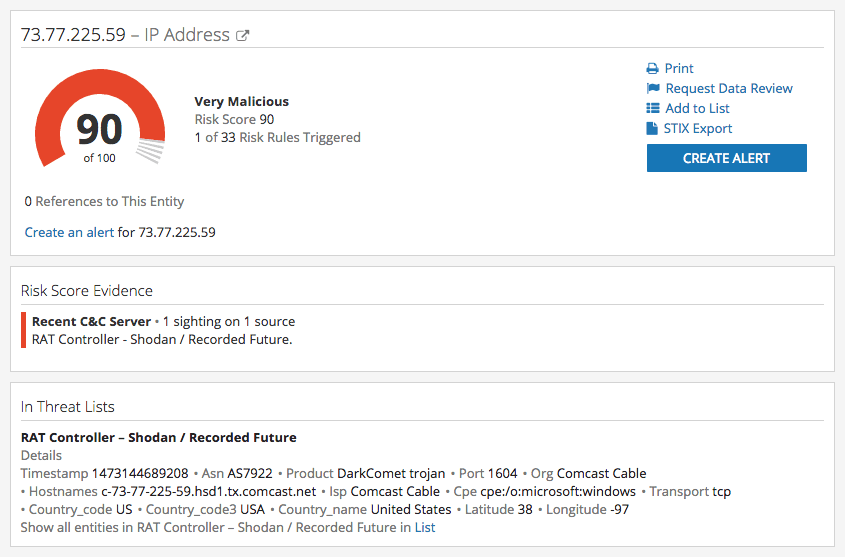
Intelligence Cards™ provide an on-demand summary of essential information related to a specific IP address or CIDR.
The Recorded Future Intelligence Card™ for 73.77.225.59 revealed (via FarSight Security’s passive DNS data integrated into Recorded Future’s Intelligence Card™) three historical DNS A records, the most recent of which (shadows.sytes[.]net) was observed between September 15 and September 20, 2016.
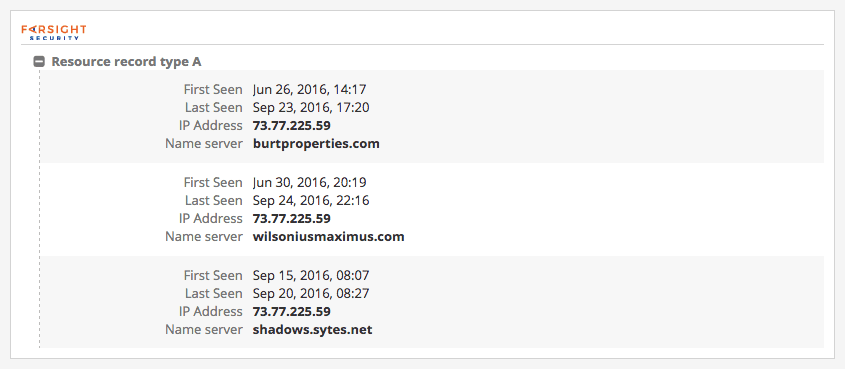
Enrich any IP address with our Farsight Security extension.
The base domain name sytes.net is owned by No-IP, a free dynamic DNS (DDNS) service. DDNS gives the account owner(s) the ability to rapidly create subdomain names and quickly alter the IP address(es) resolving to each sub-domain, which is useful when administering a RAT that is configured to connect to a domain (instead of an IP address being hard coded into the RAT) for command and control (C2).
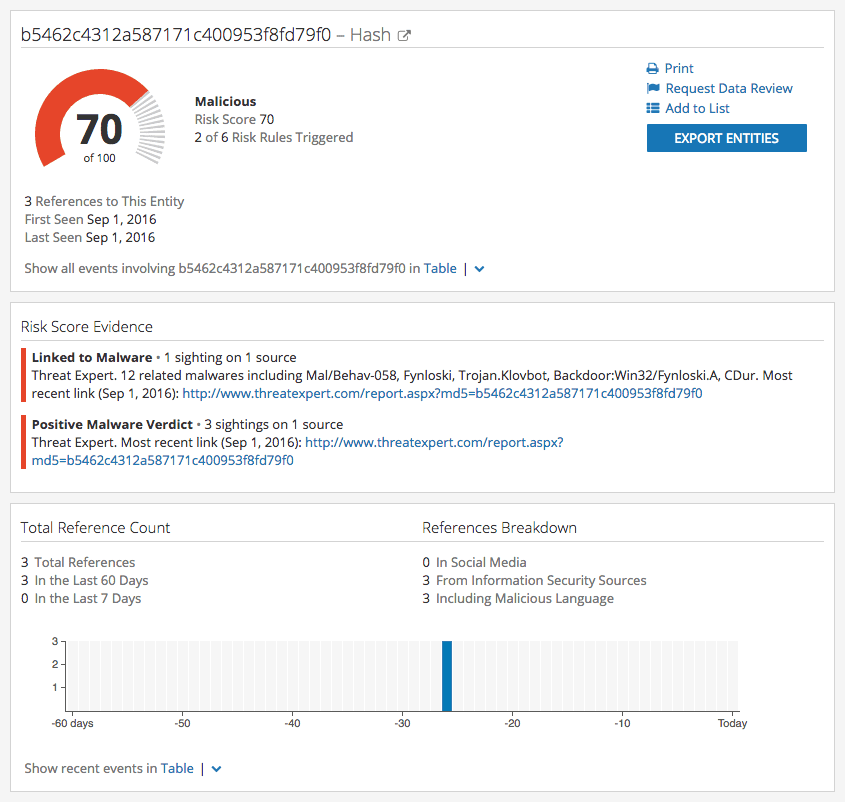
The Intelligence Card™ for shadows.sytes[.]net showed a Threat Expert malware report containing recorded network traffic to 73.77.225.59. A run-time analysis of the malicious binary produced MD5 hash B5462C4312A587171C400953F8FD79F0.
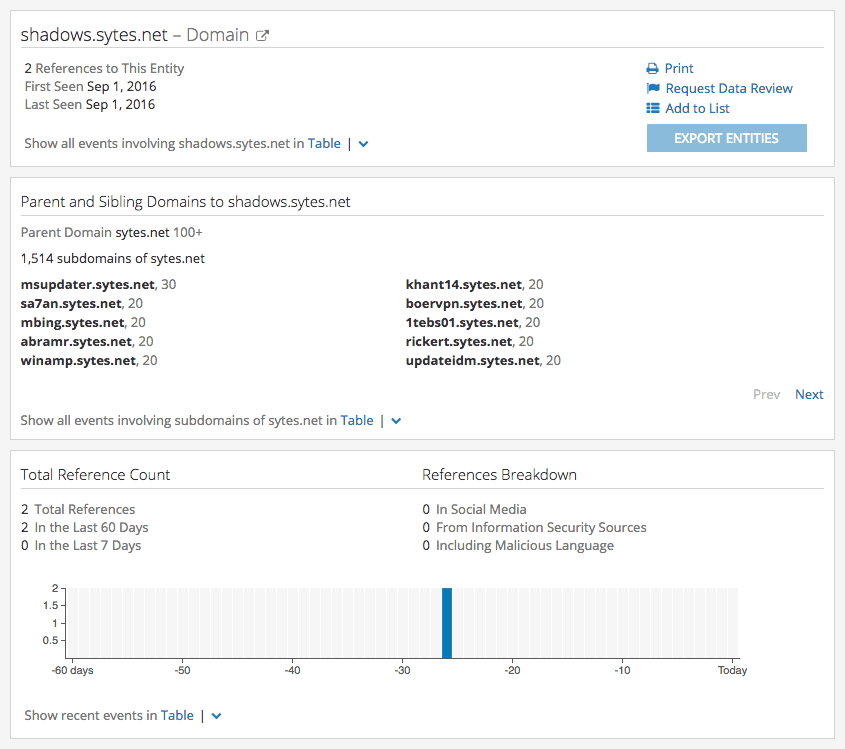
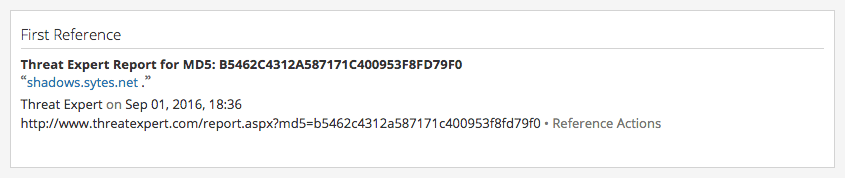
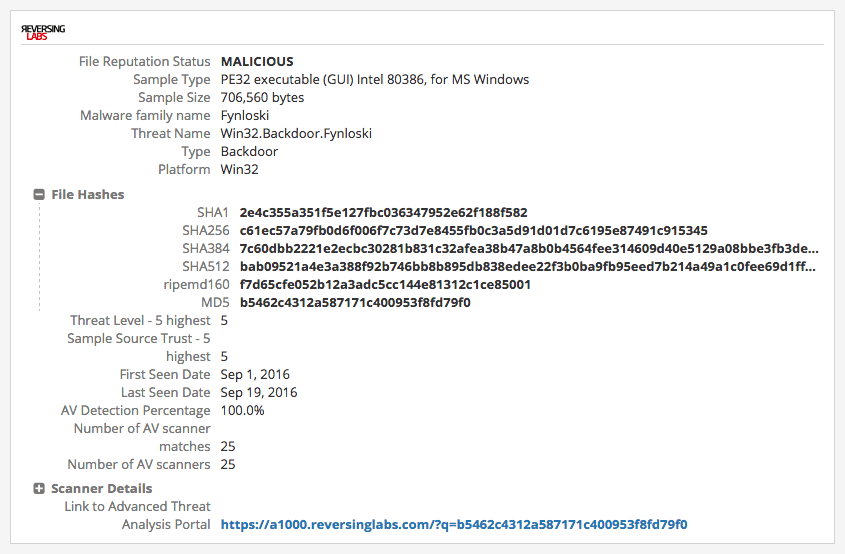
The Intelligence Card™ for MD5 hash B5462C4312A587171C400953F8FD79F0 uncovered (via ReversingLabs malware insight) additional metadata confirming this artifact is a DarkComet RAT.
Enrich any IP address with our ReversingLabs extension.
Additional available information includes a VirusTotal URL verdict from Kaspersky for shadows.sytes[.]net, and a manual port scan of 73.77.225.59 (on September 22, 2016) revealed that the host’s port 1604 was closed, but open ports included 80, 2050, 4444, and 9000. Port 4444 is the BlackShades trojan default port.
Conclusion
A Recorded Future and Shodan alert for a new RAT controller host leads to a “one-click” lookup of the IP address — 73.77.225.59 (Comcast Cable) — in Recorded Future. The Intelligence Card™ includes corresponding DNS A records (domains) from FarSight Security.
A Recorded Future search of the domain — shadows.sytes[.]net — produces a MD5 hash — B5462C4312A587171C400953F8FD79F0 — from aggregated web data. A subsequent search for the hash presents an Intelligence Card™ that includes additional metadata from ReversingLabs confirming the existence of a malicious DarkComet RAT.
10 minutes and three Recorded Future Intelligence Cards™ — containing aggregated web data, Farsight Security’s passive DNS (pDNS) data, and ReversingLabs malware metadata — produced a potential criminal investigation with little remaining effort toward probable cause and hopefully a future indictment and prosecution of the RAT administrator.
Related