Cyber Threat Landscape: Forecast

This is the third post in our blog series that aims to provide a basic overview of the contemporary cyber threat landscape.
According to United Nations Office on Drugs and Crime’s (UNODC) Comprehensive Report on Cyber Crime (2013), in 2011, at least 2.3 billion people, the equivalent of more than one third of the world’s total population, had access to the internet. Over 60% of all internet users are in developing countries, with 45% of all internet users below the age of 25 years. (Full report here.)
By the year 2017, it is estimated mobile broadband subscriptions will approach 70% of the world’s total population. By the year 2020, the number of networked devices (the “internet of things”) will outnumber people by six to one, transforming current conceptions of the internet. In the hyper-connected world of tomorrow, it will become hard to imagine a “computer crime,” and perhaps any crime, that does not involve electronic evidence linked with internet protocol (IP) connectivity.
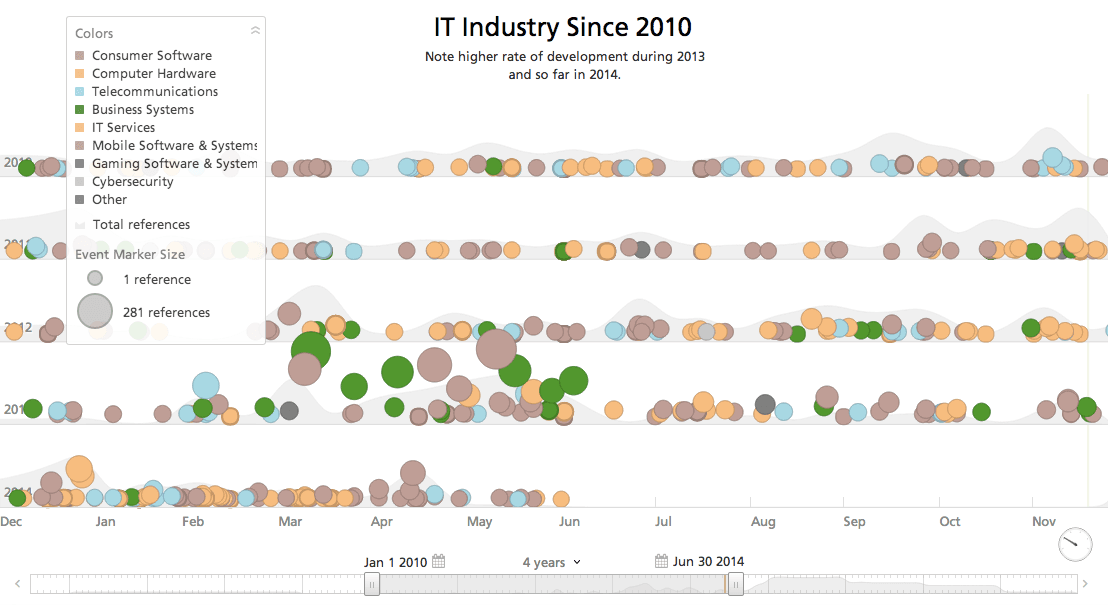
Therefore, it is imperative to assess developments within the global IT industry in order to make sense of its possible correlation with the global cyber theatre. Using Recorded Future, I ran a search for events related to the IT industry from January 2010 to March 2014. You’ll notice an unprecedented increase in the last two quarters of 2013, and the first quarter of 2014. The majority of events appearing in the following timeline are related to consumer software which perhaps reflects the rapid increase of cyber attacks the past few years.
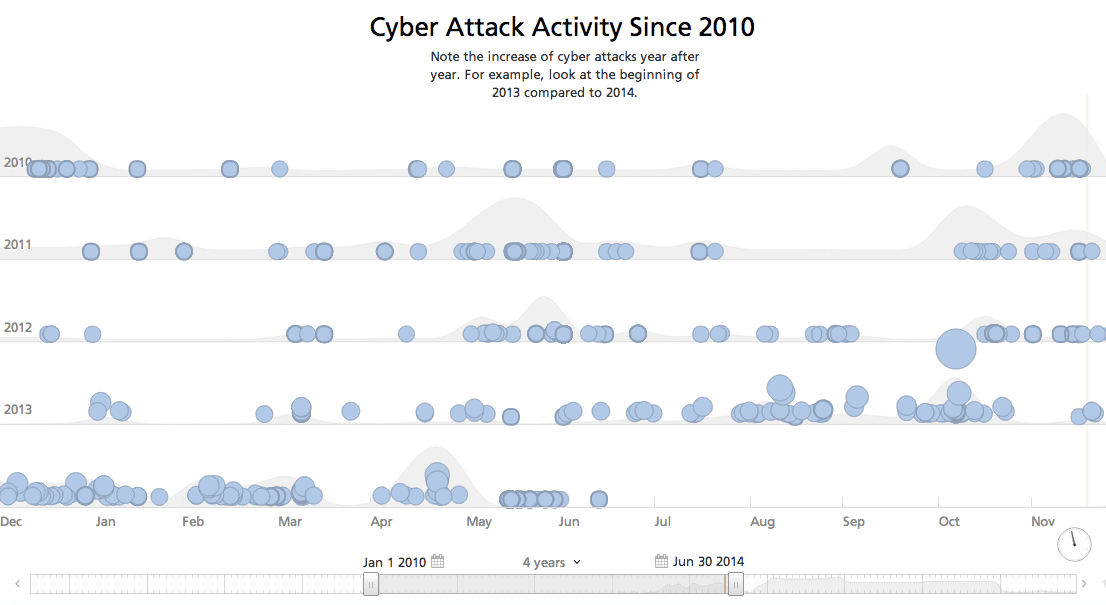
The next timeline shows the overall global cyber activity since 2010. Year after year the number of events goes up. It’s clear businesses, state institutions, and individuals continue to be victimized and besieged by sophisticated cyber attacks at an increasing rate.
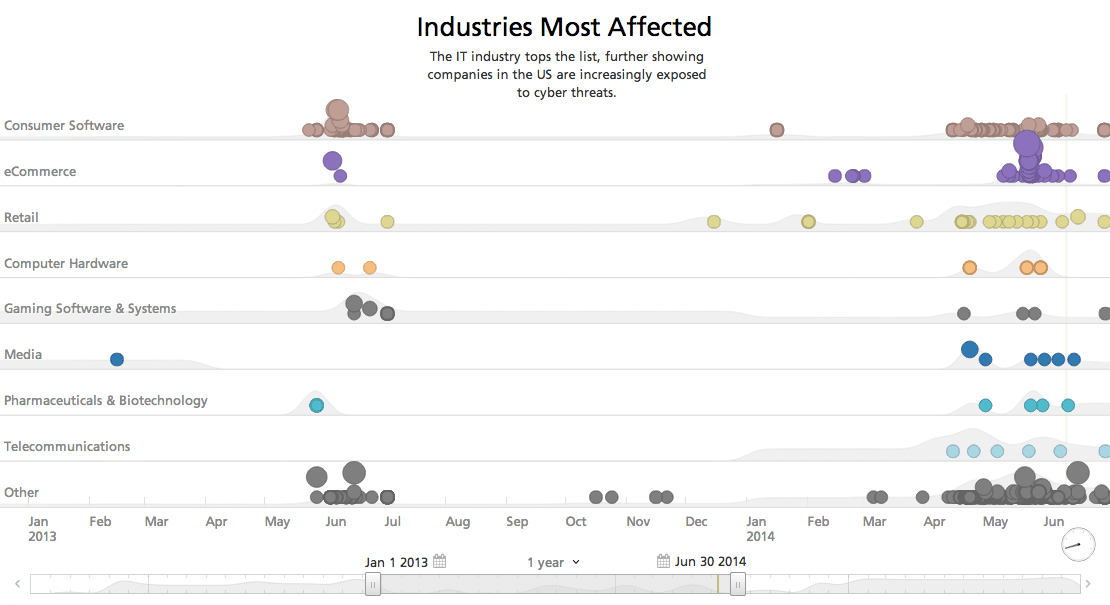
Costs Associated With Cyber Threats
With organizations from both public and private sectors increasing their reliance on technology, it’s hardly a surprise the implications of cyber attacks are impacting economic costs.
A McAfee-sponsored report produced by Centre for Strategic and International Studies (CSIS) called, “The Economic Costs of Cyber Attacks and Cyber Espionage” reveals the cost of cyber crime and espionage racks up between $300 billion – $1 trillion. These costs are likely to increase with the greater internet penetration, and as organizations continue digitalizing their products to compete in ever more competitive markets. The report also indicates no less than 508,000 US jobs alone are potentially lost each year due to cyber espionage.
Another report by Ernst & Young called, “The Global Information Security Survey 2013” highlights the incapability of more than half (52%) of the organizations in the UK to assess the impact of emerging technologies to their information security, making them the second prime targets only after US.
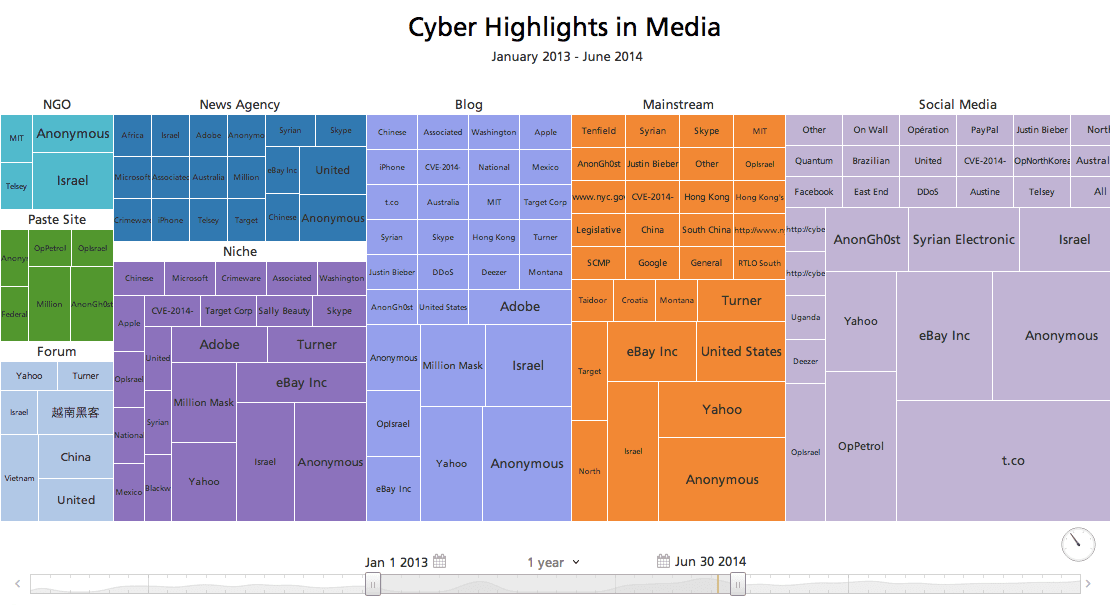
Global Cyber Theatre
As highlighted in the slide below, US and European countries remain prime targets for the world’s cumulative cyber attacks. It is also noteworthy for the first time they can no longer be referred to as the hub from where these attacks originate for reasons that will be explained ahead.
By opening up the data displayed in the form of heatmaps, it is easy to observe the number of attacks against US and European businesses, firms, and institutions far outnumber the attacks that originate from within these regions, but are directed elsewhere. This makes the cyber infrastructure within these regions shift into a defensive posture.
It’s also interesting to observe most of these attacks are consistent in their details and references, with a high number of offensives originating from countries in Asia and Eastern Europe. I’ll also infer it’s no coincidence the majority of the offensives being reported within these regions also happen to be targeting the international operations, offshoots, and subsidiaries of US and European countries.
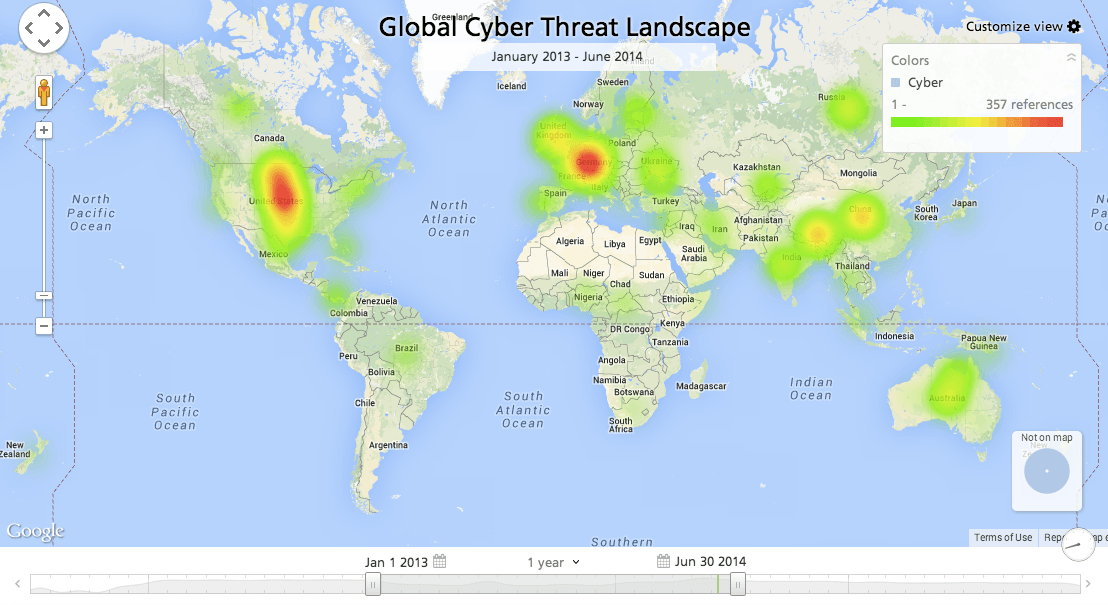
Click image for larger view
In order words, western corporations and their operations are being increasingly targeted across various regions of the globe by entities which have positioned themselves well within countries like China, Indonesia, South Korea, Russia, Indonesia, Poland, Ukraine, India, Taiwan, Hong-Kong, Brazil, Syria, and Pakistan. This shift may well mean the axis of cyber offensives has shifted towards the east.
Asia and Eastern Europe: Axis of Cyber Offensives?
This is due to the following reasons:
1. Improving IT Infrastructure
Countries with fast developing economies such as China, Hong-Kong, South Korea, and India have huge incentive in strengthening their IT infrastructure to support their booming economies. With the growing services and manufacturing sector of their economies, government and educational institutions are putting great emphasis upon producing human as well as economic capital that is necessary to support the growing sectors.
Exploitation of this advanced IT infrastructure, originally meant to support economic growth, by organized cyber crime groups, hacktivist, and other entities is most likely to remain as a foreseeable but unavoidable challenge.
2. Expanding Tech and Telecommunication Sector
With high tech companies like Apple, Google, and Samsung shifting their operations into Asian countries, the development must also be balanced with the technical structure which could support the increasing IT sector.
For example, the next generation of IT infrastructure such as the 4G internet network could support advanced persistent threat attacks. Or the increased number of server farms or call centers within a country are ideal to host Command and Control (CnC) centers for receiving call backs. This is the traffic that flows from compromised devices to CnC servers, or act as botnets for cyber threats that involve sophisticated malware, phishing, socially engineered attacks, and distributed denial-of-service (DDoS) attacks.
Please refer to this live feed from to review the recorded development within the IT sector of most of these countries over the last four years. Notice how Recorded Future’s new feature in the Table view (on the left corner) is listing all the relevant developments within, or related to, more than 200 tech, or tech-dependent firms, operating within Asia; further strengthening above mentioned points.
3. Institutional Support
With countries like China behaving aggressively to pursue its economic goals, a number of their institutions are alleged to be acting complacent in making the Unit 61398, an alleged APT unit of People’s Liberation Army (PLA) targeting US, Germany, and France for the exfiltration of trade secrets, take over of critical national infrastructure, and to conduct corporate and intelligence espionage.
Though, it is also interesting to note that China, despite having one of the most sophisticated filtering systems in the world, was unable to defend itself from a DDoS attack against Chinese (.cn) website registries in late August 2013.
4. Weak Legislation and State Control
The greatest incentive, particularly in the case of Eastern European countries like Ukraine, lies in the fact the majority of these countries have weak (if any) legislation on cyber crime. Moreover, the implementation of these laws is further balked by technological limitations of state institutions (bureaucratic and legal loopholes) providing excellent cover to cyber criminals. These actors also happen to derive their motivation from supportive social structure, as well as readily available economic and professional incentives that are becoming increasingly conditional to cyber attacks.
Forecasting the Cyber Threat Landscape
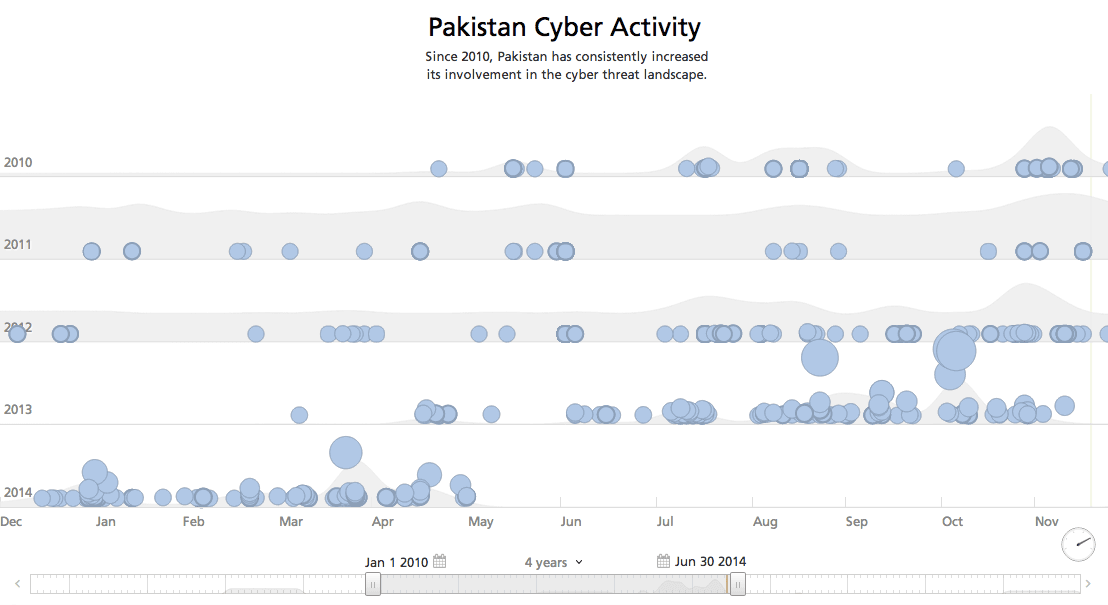
A suitable combination of aforementioned factors, in the context of global geo-political and economic framework, would determine the future hotbeds for cyber attacks. Countries like Pakistan, with a thriving IT sector, 4G network introduction in the offing, no legislation on cyber crime, and a formidable existing body of hackers is likely to become a future point of origin for cyber activity.
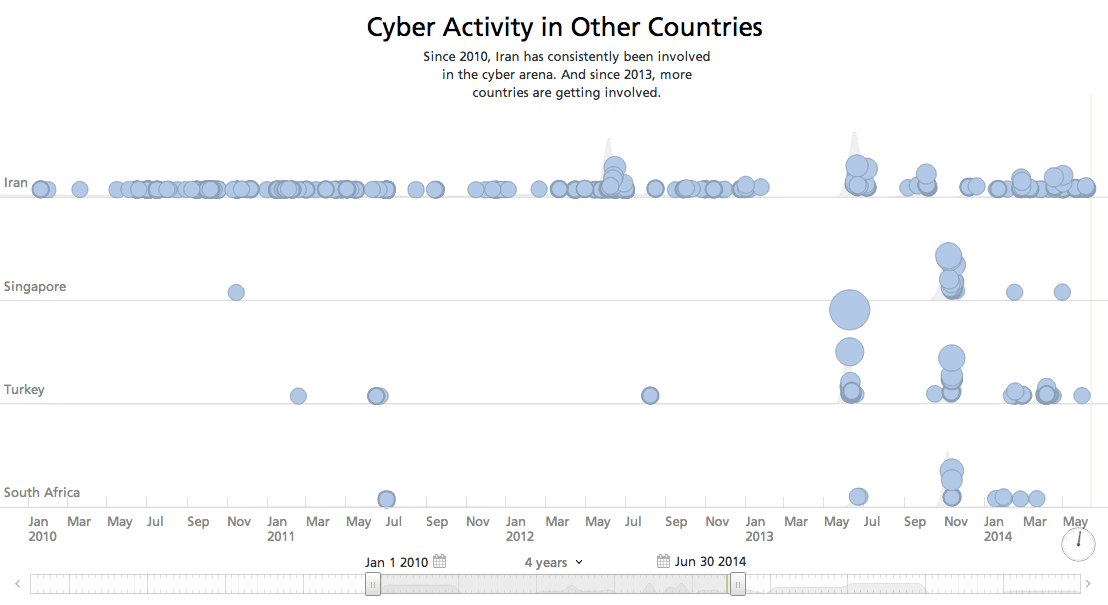
On similar lines, increased activity could also be recorded in countries like Kazakhastan, Iran, Turkey, Singapore, South Africa, and numerous North African countries.
Conclusion
From the analysis in this three-part series, it’s fairly easy to conclude cyber attack frequency is on the rise. Now the scope, rate, and nature of cyber attacks depends largely on an organization’s industry, size, and location, but it’s clear EVERY organization MUST reconsider its cyber security strategy.
The conventional remedies are unlikely to suffice in the face of fast-evolving threat complexities in the cyber milieu, and today’s cyber security policy must ideally switch its posture from defensive to preventive. By making use of Recorded Future’s web and cyber analytics, you can take a more realistic look at the threats your organization is, or likely to, face.
Related