The 4th in the 5th: Temporal Aspects of Cyber Operations

Summary
Time is no one’s friend. In the long run we’re all dead, but let’s narrow the perspective and examine how time impacts cyber operations.
Compromise is inevitable
Before a compromise time is on the attacker’s side. They just need to compromise one system and they’ll have access.
Loss of access is inevitable
After the compromise, time is on the defender’s side. They just need to discover one single IOC and they can roll up the compromise.
This depends on the security posture of the defenders and the capabilities of the attackers. After a compromise, everything done by the attackers can result in discovery by the defenders. Including doing nothing.
Operations are continuous
Finally, the iterative cyclical nature of attack and defence means that once an attacker is discovered and purged, they can attempt to compromise the target again. This cycle results in time being an asset to alternating sides, depending on which one controls the network.
Types of Time
Cyber operations have multiple vectors on which to measure time:
- Time on the compromised system (dwell time)
- Time from compromise to breach to — maybe — discovery
- Time required for exploitation of the compromise
- Time until the criminal liabilities expire
Different attackers and operations are affected to a greater or lesser degree by these times depending on their purpose.
Hacking Shells Is Not a Strategy
Simply compromising a system is usually not an end goal in itself, rather it is simply a step in a process towards the final phase — exploitation — where the attacker benefits from the compromise.
Historically attackers would exploit their illicit access for resources — computers, internet access, bandwidth, etc. This was the old golden age of the curious explorer hackers, now long gone. These days hacker motivation typically falls into a small number of pragmatic purposes:
- Monetisation
- Espionage (political, military, or economic)
- Preparations for future conflict
- Hacktivism
Attackers share the common trait of operating outside the law, however only a subset — non nation state threat actors — face repercussions for their actions (although the US is insanely bringing criminal charges against nation state operators who merely enact their government’s policy).
Criminals hack for cash, spies hack for secrets.
Criminals attempt to exploit a compromise for financial gain. Thus the monetisation strategy controls their operational requirements, such as how long they need to maintain access to compromised systems. Additionally, they have legal considerations. Although an operation might be years old, until the statute of limitations expires they are vulnerable.
Nation states exploit a compromise for intelligence or military purposes. These include:
- Political intelligence (long dwell time means more intel collection).
- Seeding civilian infrastructure for future wars (extremely long dwell times, one hopes!).
- Economic espionage, where rapid ROI is more important than dwell time. Economic spies want to build a better washing machine today, they don’t know what they’ll want next year.
There’s a subset of nation state hackers operating for financial gain. They share operational constraints with criminals, their monetisation strategy dictates their dwell time requirements.
Background
To better analyse cyber operations it is helpful to understand the structure of operations and special operations theory. These two frameworks provide a methodology for analysing cyber operations.
Operations Overview
Operations have an inherent structure, defined confusingly as “pre-operational, operational, and post-operational” … but they’re also more formally divided into stages. This division is, in many ways, a matter of taste. The transitions through the operational cycle are not marked by clear lines. What is important is the concept that operations are cyclical (assuming the group or operator remains active). There are a number of ways to divide operations into phases, but a simple version is enough for our analysis:
- Planning: selecting the target, creating a plan, etc.
- Preparation: gathering the necessary elements, e.g., tools, ppl, intel; rehearsals
- Execution: conducting the operation
- Escape and Evasion: avoiding the response from the defenders
- Exploitation: getting value from the results of the op, e.g., money, propaganda, etc.
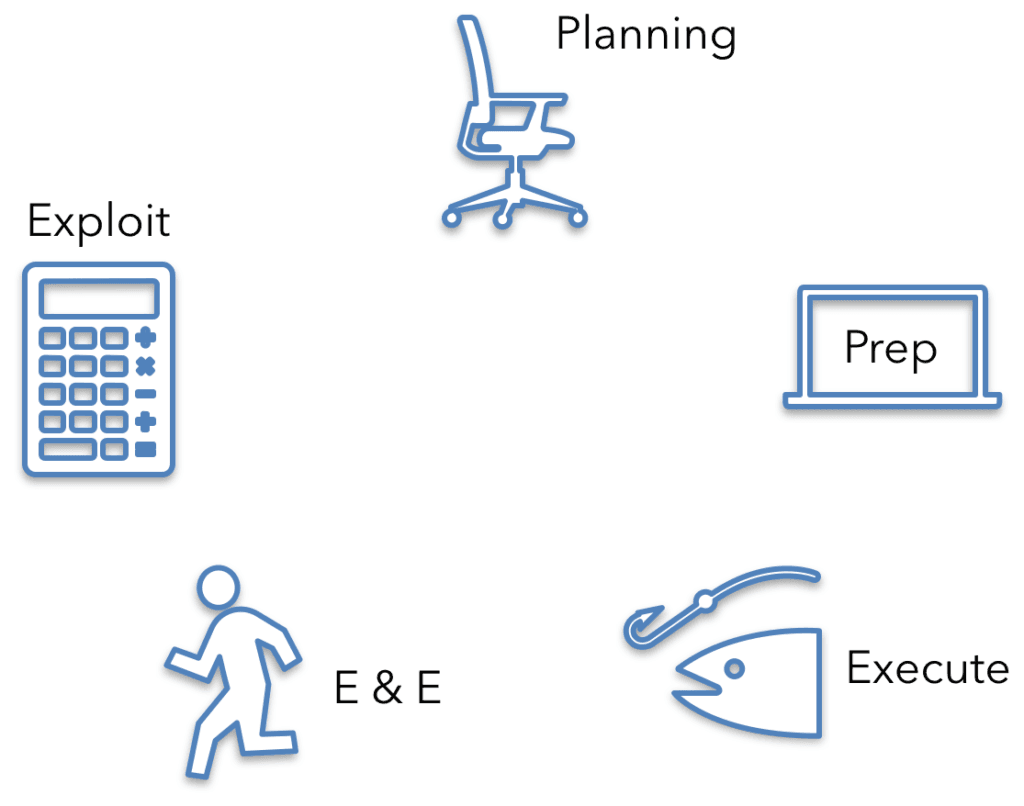
Never forget that all of the phases prior to exploitation are simply there to enable exploitation. For espionage operations exploitation can mean collecting intelligence information, while for cyber criminals it typically means monetisation (some sort of business plan), while hacktivists attempt to promote their agenda, and so on. Operations exists to achieve the exploitation phase.
Takeaways:
- Operations have phases
- Operations are conducted to achieve the exploitation phase
- Exploitation is the principle phase for an attacker, without it the operation is a waste of resources
Special Operations Theory
Special forces are able to achieve mission success against a larger adversary by successfully applying the principles of Spec Ops theory. The principles that help determine Spec Ops success are in many ways similar to the principles that govern success in cyber. Spec Ops theory only goes as far as the execution phase, but that generally includes escape and evasion.
- Planning: simplicity
- Preparation: security (aka, secrecy), repetition (aka, automatic tasks)
- Execution: speed, surprise, purpose
Special operations work when the plan is simple, because too many components cause the chance of failure to increase as problems cascade. The plan must be kept secret to maintain the element of surprise. The operatives rehearse and train for it specifically, so the actual operation is essentially done with “muscle memory.” Alternately, the plan can be comprised of only rote tasks with which the operators are already intimately familiar. The operation must be conducted with speed, surprise, and purpose.
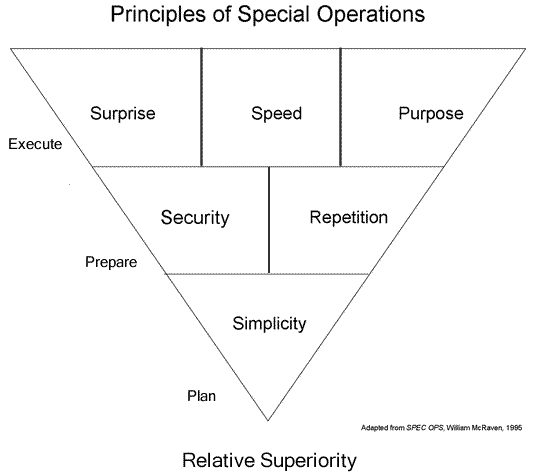
These six principles are very similar to how successful cyber operations are conducted. The attacker maintains secrecy about the central elements of their plan (e.g., the target, the vulnerability, etc.). Typical attackers operate in familiar environments using tools, techniques, and procedures they know well. If the target has a novel system, a sophisticated attacker will become familiar with it before the operation (c.f. Phineas Phisher’s penetration of Hacking Team.) Frequently, advanced attackers will go so far as to replicate the target environment in a lab and script their attack (c.f. TAO clickscripts). Completely scripted attacks, honed against a duplicate target environment, are extremely fast, rehearsed, and present minimal opportunities for human error.
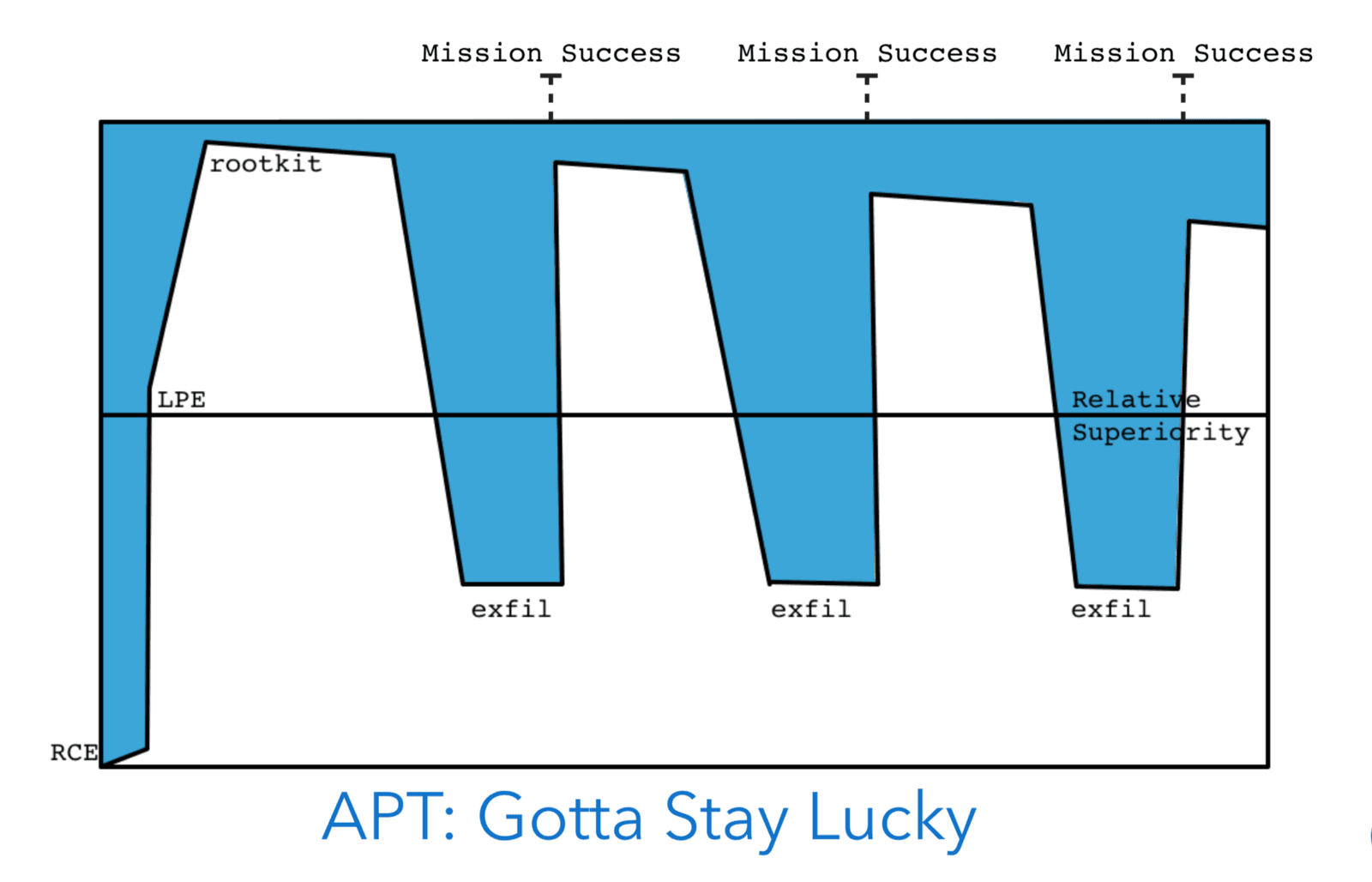
Successful cyber attacks share many of the same principles that enable successful special operations. But there is another useful framework that spec ops theory provides: a graph model for visualising the probability of mission success and operator risk, measured as “area of vulnerability.” This visual model is a simple graph of operational activities over time. The key factor to mission success is to reduce the area of vulnerability, where the attacker can be thwarted by the defence before achieving mission success. The critical point of the model is when the attacker achieves “relative superiority.” Where they become dominant over the defenders and thus relatively immune to their capabilities.
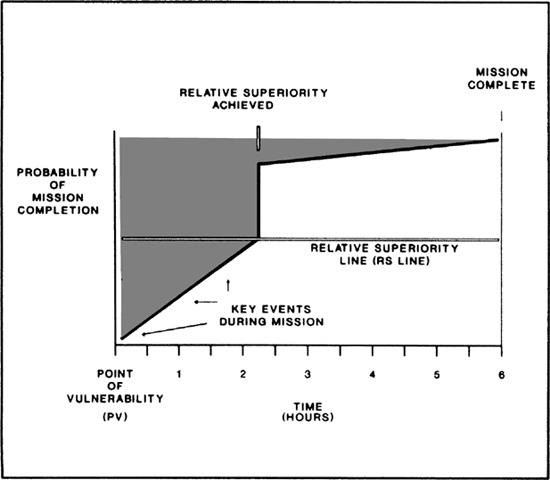
This visual model of an attack provides a simplified way to examine different types of cyber operations. The fluid nature of cybersecurity means that “relative superiority” cannot be precisely defined, however an example might be: “gaining system level privileges and installs an implant.” Mission success is also dependent on operational requirements and the type of operator (hacker, criminal, nation state threat actor, etc.) A non-state operative has at least two criteria for mission success — firstly, achieving their purpose (exploitation), and secondly, not being caught and punished. State operatives also need to reach exploitation, and they typically don’t want to get caught (as it can retroactively negate exploitation of the operation), however they typically don’t face punishment. This distinction is important when it comes to plotting time.
In all cases the point of vulnerability begins when an attacker first compromises a system, as it is from this when they become signal rather than noise. In the illustrative diagrams consider the “exfil” operational activity as essentially a stand in for any operational activity, such as lateral traversal, downloading additional tools, exfiltration, anything.
Analysis
With that background out of the way it is now possible to model and visualise the effect that time has on cyber operations.
Note: This analysis is restricted to purely cyber operations and doesn’t include human assisted cyber or “blended” ops. Human assisted cyber operations are far more complex to model because the attacker’s vulnerabilities can cover the duration of the person’s life. This analysis is just going to pretend blended ops don’t exist and examine only pure cyber operations.
Non Nation State Threat Actors
Many hackers are not operating under direction of a nation state, but instead for themselves (or their team.) Typically they are motivated by monetisation, so there strategy there controls their access time requirements. Additionally, without the protection of a nation state, they face criminal liability for their actions. In the case of a pure CFAA violation in the US, this has a 5 year statute of limitations. Therefore, a non-state threat actor has to conduct their operation and then remain unidentified (and free) for at least 5 years.
Platonic Ideal
The ideal hack would therefore be one that started with the attacker in a position of dominance, exposed them only briefly while conducting their monetisation operation, and then they would clean up and vanish. Many limited nation state cyber operations actually follow this pattern as it creates minimal exposure to risk.
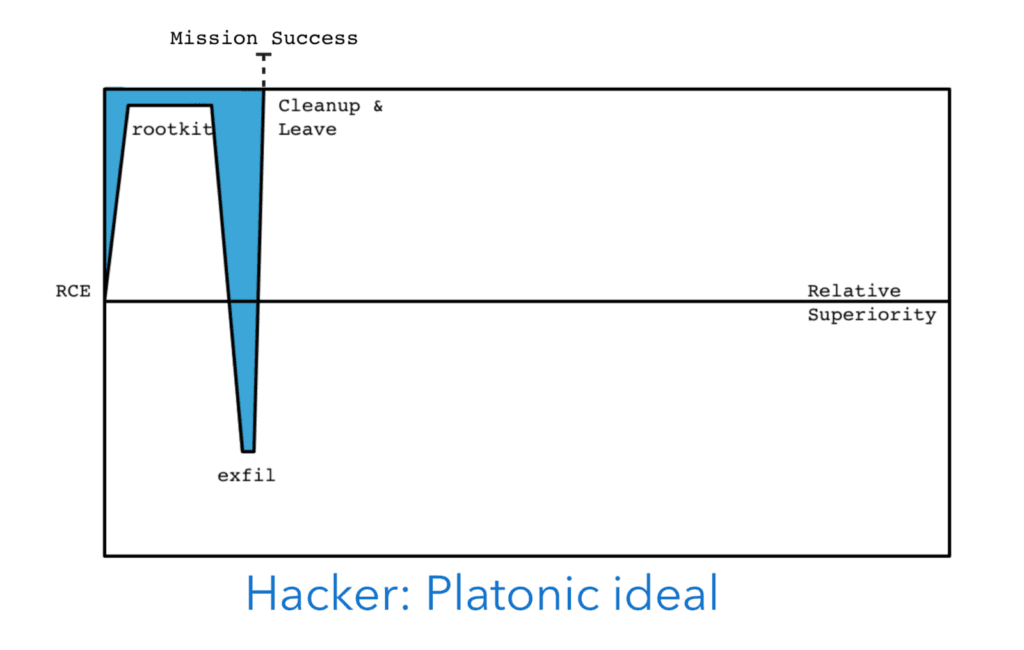
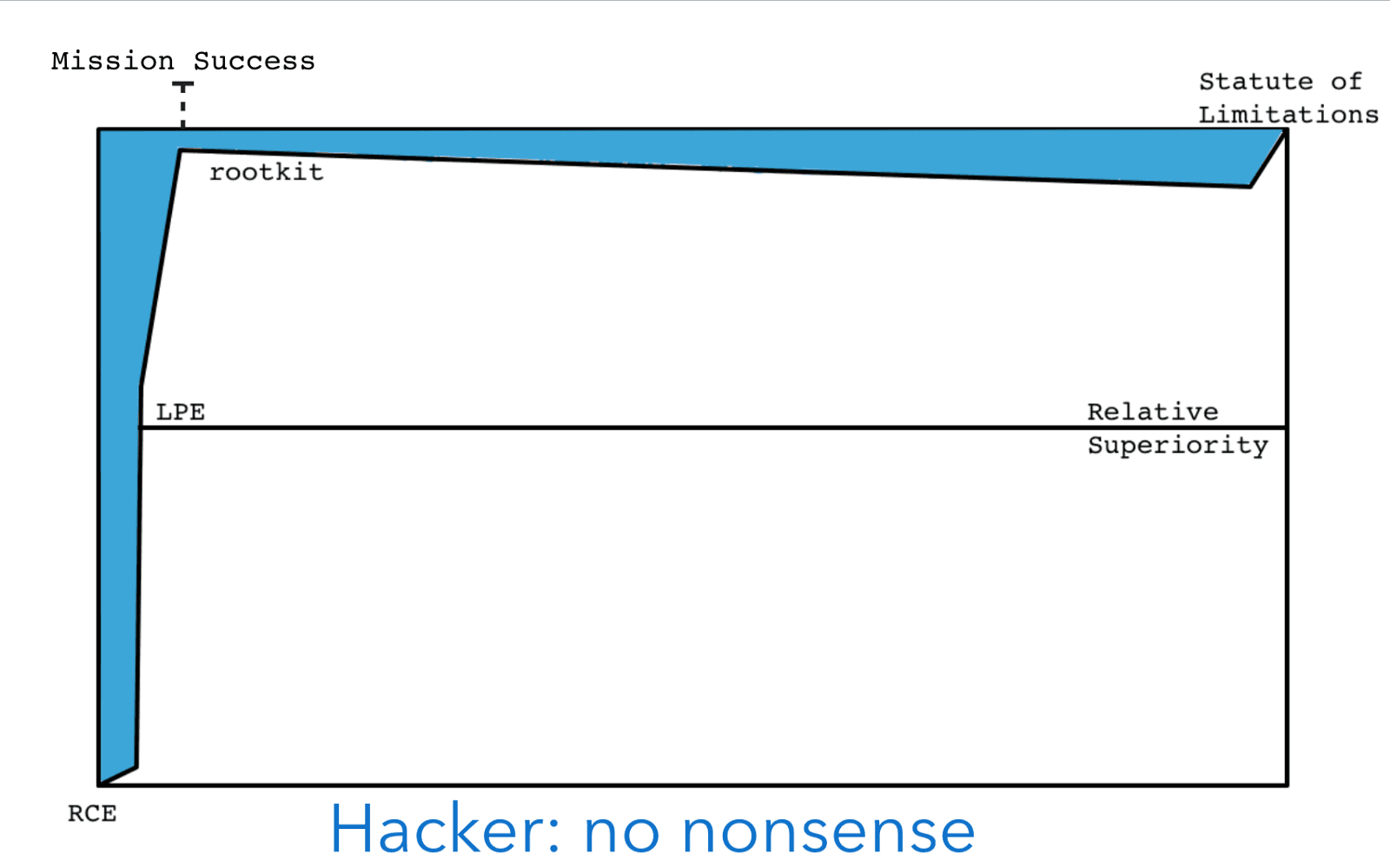
Pointless Hack
The older style hacks where there was no monetisation goal had this sort of risk exposure. While the attacker is in a strong position to remain safe against discovery, exposure, and potentially arrest, the length of time (5 years, at least) means that defenders constantly accrue advantage. Over time the risk of exposure increases as defenders have the opportunity to get lucky, their defensive tools become more aware of older known hacker tools, etc. This is a risky move for hackers, one of the reasons that the old style exploratory hacking has gone out of fashion. Long term risk and no reward? Bad deal.
Luck Is Not Neutral
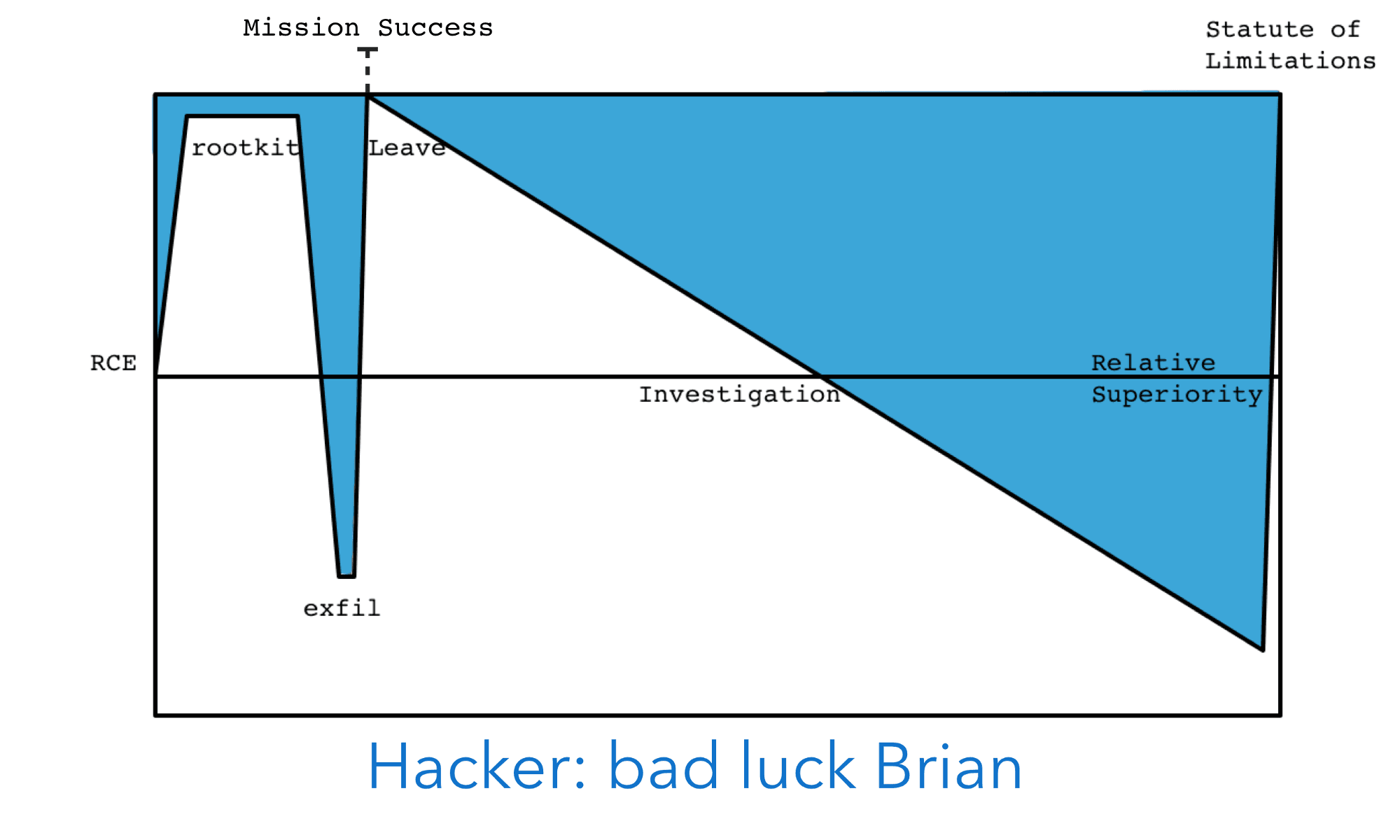
A monetisation strategy might involve a one time exfiltration of data (such as a credit card database), and the attacker leaving after completing their operation. However, a chance discovery, or a functioning defence tool, or relevant threat intelligence data, could all lead to a relatively swift discovery of the breach. Once this has happened, it is a contest between how well the hacker operated (did they make mistakes, clean up properly, leave anything behind?) and how many resources are invested into the investigation. The attacker may lose their dominant position early, but the investigators might hit impediments to further progress (jurisdiction, resources, time, etc.)
Typical Sob Story
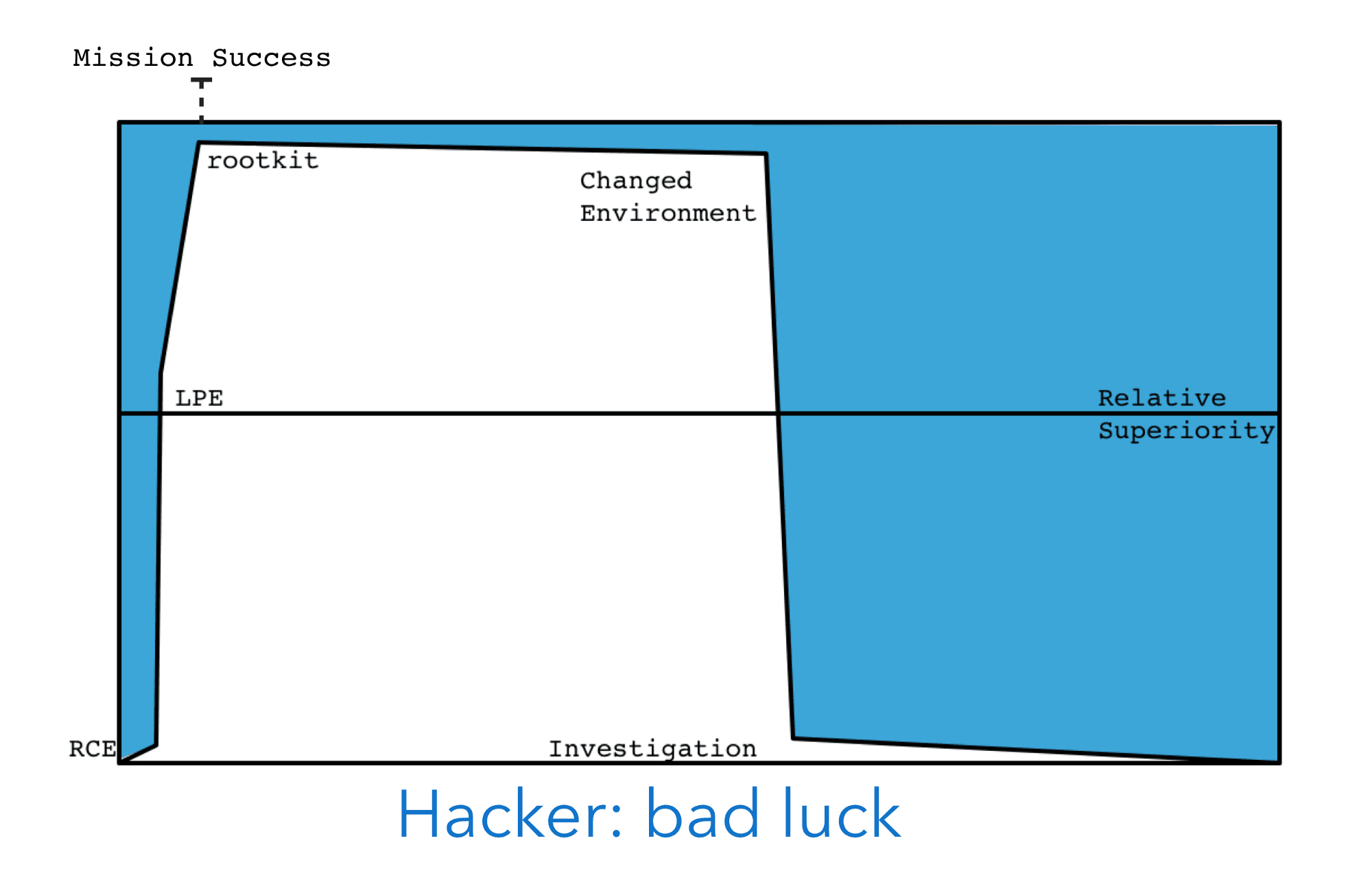
The bane of an attacker’s persistence is seldom defender tools but rather evolving and changing environments. Since the attacker is seldom consulted or informed of planned alterations to the network, their systems designed and deployed for a specific target environment are made obsolete almost immediately. For example, an implant installed and deployed on a host is typically not copied over and installed on the new system. Or a network without telemetry and monitoring suddenly has new monitoring tools installed. Attackers may dig in to a lax operational environment and then months later the environment changes drastically altering their risk exposure. Since the time duration here can cover years, this sort of change is a frequent occurrence.
Nation State Threat Actors
As we know, not all attackers are criminals attempting to make a profit. Some are nation state threat actors engaged in specific missions, such as espionage, or sabotage, and so on. It should be noted that an additional factor that gets added to this risk evaluation is just how bad the result of blowback would be. Many threat actors have figured out that the correct answer is usually “not that bad,” although some continue to prize covertness beyond the point of reason.
A Simple Job
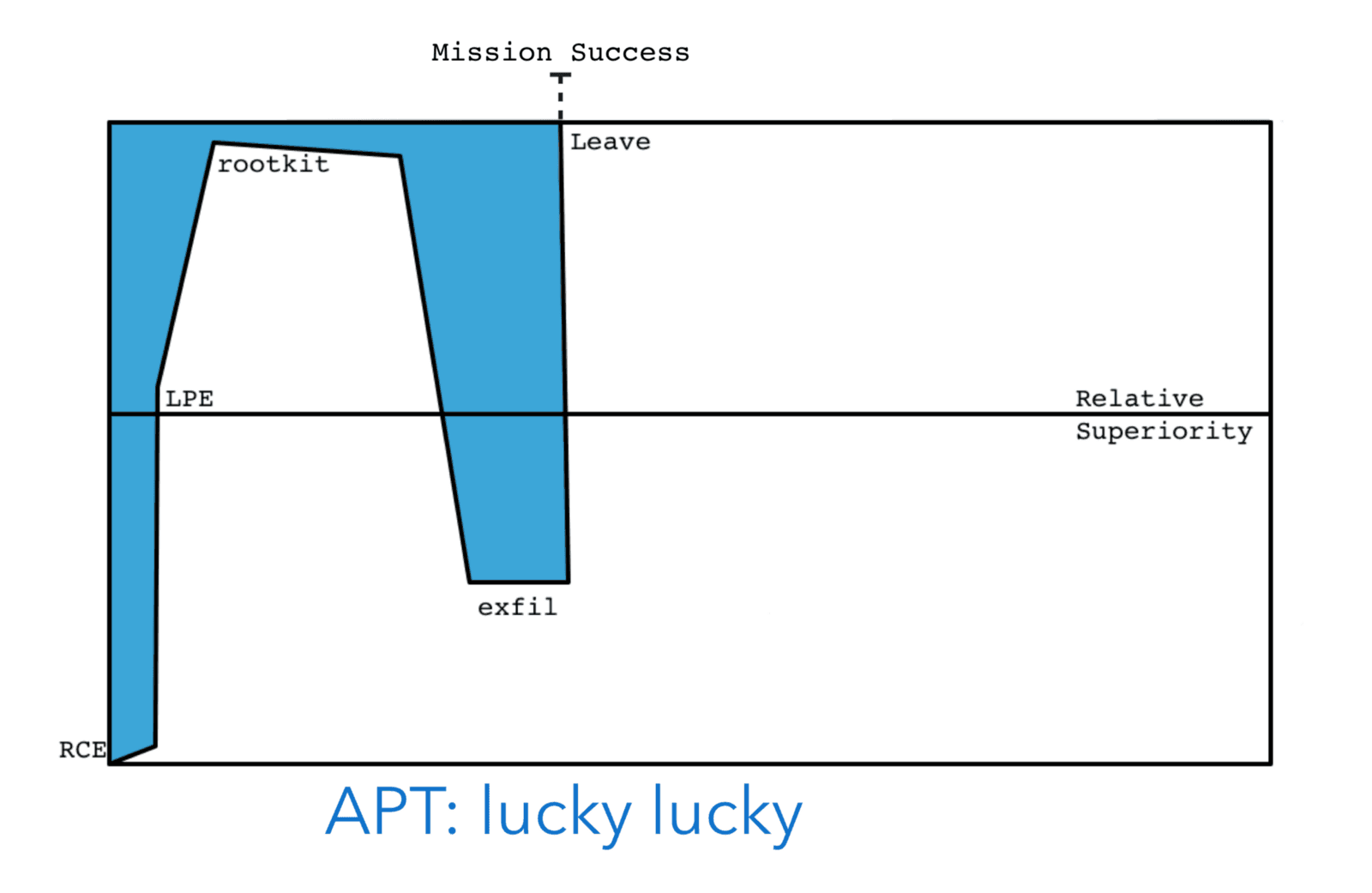
The ideal scenario for a simple nation state operation is to compromise the target, conduct their operational activity (e.g., exfiltrate the relevant database), and then cleanup and leave. This sort of attack plan has a low risk profile as the success of the mission marks the end of the period of vulnerability. Although this is the ideal approach, a one shot hack with only a single operational activity, it is not always appropriate given the operational requirements of the mission.
Normal Operation Structure
It would be ideal if operations required only a simple one off hack, but the reality is that most ops require frequent periodic operational activity. A political or military espionage operation will require long dwell time and frequent collection of the take. This means that, given enough time, exposure is inevitable. Each time there is a collection (requiring operational activity), the attacker is exposed. Additionally, time is on the side of the defence, as the longer the attacker remains on the network the more likely that something goes wrong. Of course, the counter balance to this is that being discovered and evicted just means that they need to hack back in, and so the cycle continues …
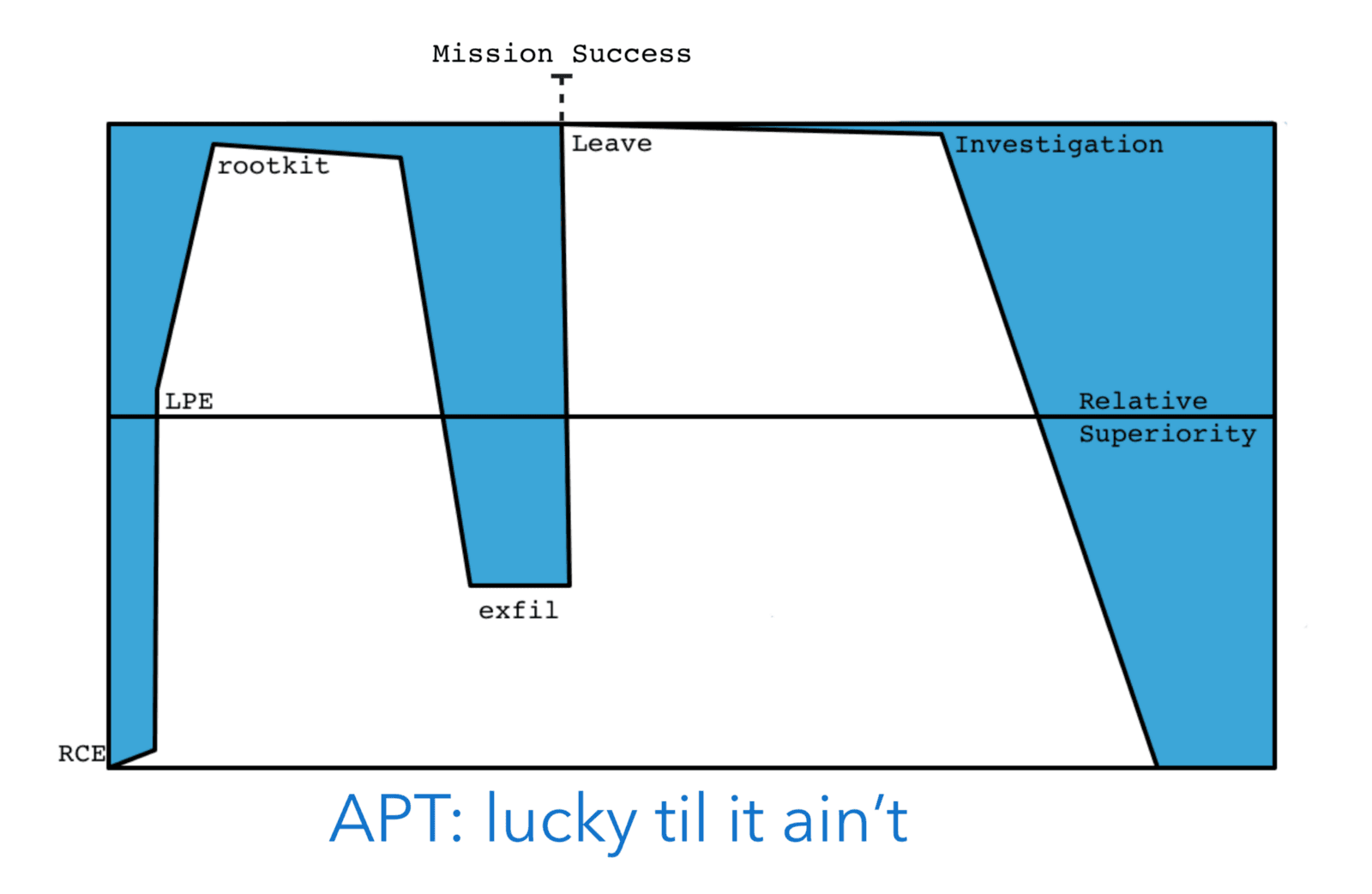
Earning an AV Cryptonym
The modern cybersecurity environment involves a lot of adversarial defensive organisations. These companies, such as threat intelligence or anti virus, discover a nation state hacking campaign and expose it. Once this happens, all instances of attacker technology becomes a liability. What was initially a safe install of an implant is suddenly an Indicator of Compromise, which can retroactively jeopardise a mission. If the target learns that they were compromised, they will know that the information at a certain time is no longer secret, and they can alter their plans accordingly. Luck in cyber is fickle, and the consequences can reach backwards in time to invalidate intelligence. Thats the game …
Conclusion
Time is the enemy of everyone — defenders and attackers. Before a compromise, it is inevitable. After a compromise, loss of access is (essentially) inevitable. Until there is perfect cybersecurity, the cyclical nature of penetrations and breach discovery means that time will forever betray both defenders and attackers.
Related