Exploring Exploitation of Medium and Low CVSS Score Vulnerabilities
Vulnerability management can pose a significant challenge for organizations of any size. Wrestling with the constant onslaught of new vulnerability disclosures, identifying which ones actually impact your environment, and then verifying that a patch won’t break something in your network can quickly turn into a full-time job. The scale of the problem results in an ugly truth: it is typically infeasible to patch everything in a timely manner. Because of this, teams must be deliberate and selective in how they approach patching.
As teams weigh a variety of factors, it’s important for them to understand that threat intelligence is an integral part of a risk-centric vulnerability management program. There is, of course, the technical risk of a vulnerability. This is the inherent potential loss of confidentiality, integrity, or availability as a result of exploitation of a vulnerability. This is typically reflected as a high or critical Common Vulnerability Scoring System (CVSS) score.
However, the actual risks posed by vulnerabilities have an environmental aspect, as well. Active exploitation by malware, for example, can greatly elevate the risk of a seemingly low-priority vulnerability. With this in mind, I was curious as to what the data in Recorded Future showed regarding exploitation of vulnerabilities with medium and low CVSS scores.
Vulnerability Risk Score Trends
Looking at approximately a week’s worth of Recorded Future Vulnerability Risk Lists to examine the breakdown of what we consider high-risk vulnerabilities, the following interesting trends emerged. The immediately apparent trend is the distribution among vulnerabilities based on their NVD severity.
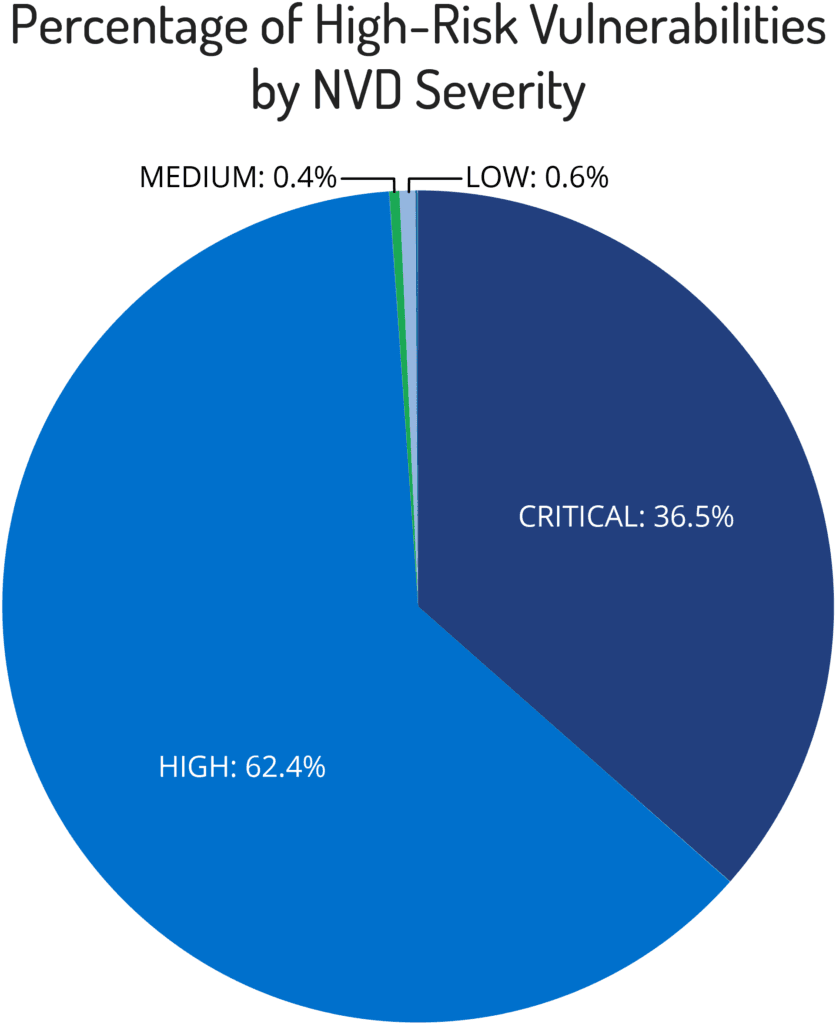
We find that vulnerabilities with high CVSS scores make up the bulk of the Risk Lists, with an average of 62.4 percent of the total vulnerabilities. This is followed by critical CVSS scores at 36.5 percent, low CVSS scores at 0.6 percent, medium CVSS scores at 0.4 percent, and no CVSS scores at 0.06 percent (“no CVSS score” is often an indication of vulnerabilities that have been disclosed by a vendor but have not yet been assigned a CVSS score in the National Vulnerability Database).
Judging by the trends, vulnerabilities with a CVSS score of medium or lower account for just over one percent of the vulnerabilities in our risk lists. In actual numbers, this is an average of 421 vulnerabilities out of 38,036 total vulnerabilities.
Perhaps more interesting than looking at total counts, though, is an examination of the Recorded Future average risk scores by NVD severity.
| NVD Severity | Recorded Future Mean Risk Score | Recorded Future Median Risk Score |
|---|---|---|
| Critical | 80.52 | 80 |
| High | 65.38 | 65 |
| Medium | 85.64 | 86.5 |
| Low | 85.85 | 89 |
| None | 80.54 | 78.75 |
What we observe now is that vulnerabilities with low CVSS scores actually have the highest average risk score with 85.85 severity, while vulnerabilities with high CVSS scores have the lowest, with a score of 65.38. This is not particularly surprising, given the nature of Recorded Future risk scoring and Risk Lists. Vulnerabilities will make the list by virtue of having a high CVSS score alone, as that rule will increase a vulnerability’s risk score to a minimum of 65, while vulnerabilities with low or no CVSS score will have risk scores based entirely on other evidence, such as active exploitation.
When we remove vulnerabilities from the dataset with no evidence of recent exploitation, we observe the following distribution by CVSS score:
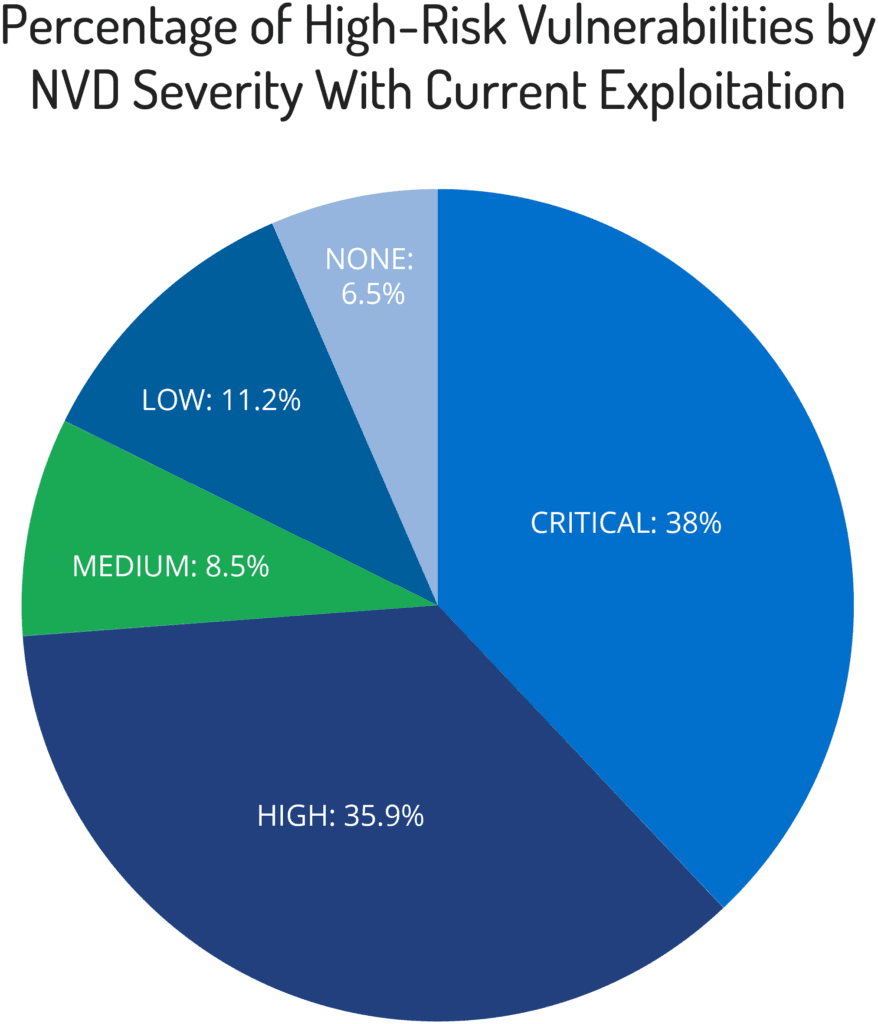
In this context, the percentage of vulnerabilities with medium or lower CVSS scores in the Risk List increases significantly to a little over a quarter of vulnerabilities, with recent evidence of exploitation.
We also see the following breakdown of risk scores:
| NVD Severity | Recorded Future Mean Risk Score | Recorded Future Median Risk Score |
|---|---|---|
| Critical | 87.73 | 87.5 |
| High | 75.74 | 74.83 |
| Medium | 85.98 | 89 |
| Low | 85.29 | 89 |
| None | 80.54 | 78.75 |
Unsurprisingly, this places critical CVSS vulnerabilities on top, with an average risk score of 87.73. Interestingly, high CVSS vulnerabilities maintain the lowest risk score average at 75.74, while vulnerabilities with medium and low CVSS scores have very close averages of 85.98 and 85.29, respectively. Vulnerabilities with no CVSS scores are unchanged in this view, perhaps indicating that there is a high likelihood of evidence of exploitation for those vulnerabilities.
Given this data, it is clear that vulnerabilities with medium, low, or no CVSS scores present a small, but potentially high-risk, subset of all vulnerabilities. The higher average risk scores for vulnerabilities with medium and low CVSS scores, in this case, indicate a higher risk of exploitation for those vulnerabilities when they appear in Recorded Future Risk Lists, as compared to vulnerabilities with high CVSS scores in the same list. The pattern of risk score averages could point to adversaries explicitly selecting vulnerabilities with lower CVSS scores for exploitation in order to take advantage of longer patch cycles. Organizations that focus solely on CVSS scores to prioritize patching may be leaving themselves exposed to active threats.
Exposing Blind Spots With Threat Intelligence
As can be seen in this analysis, the inclusion of threat intelligence is crucial for accurately understanding risks posed to organizations, such as the real-world exploitation landscape and how that adversary activity impacts your organization. Pairing this type of external intelligence with internal vulnerability scans may expose blind spots in an organization’s attack surface and allow for better preparation against potential threats.
If you’re still unsure about how applying threat intelligence to vulnerability management can make a difference in your security every day, download our free white paper, "Vulnerability Intelligence From the Dark Web: The Disclosure to Exploit Risk Race."
Dan Bearl Dan Bearl is a threat intelligence consultant at Recorded Future.
Related
