How Analysts Can Deep Dive Into CVE Vulnerabilities
Patch management is a crucial part of information security, but the volume of patches can be difficult to manage. Many vulnerability managers need to oversee hundreds or even thousands of devices and ensure there are no weak spots that can be exploited.
The key to avoiding information overload is prioritization. But how can vulnerability managers keep the most critical threats top of mind?
Generally speaking, vulnerability management teams prioritize patching efforts based on CVSS scoring which incorporates many factors, including:
- The severity of the threat (the likelihood of it impacting your company and to what degree).
- The level of vulnerability (e.g., is the threat local or remote?).
- The cost of mitigation and/or recovery.
These three steps are imperative, but can be time consuming and resource intensive.
To make the process simpler, vulnerability managers can use tools, such as Recorded Future’s Cyber Daily email, to quickly and easily discover trending vulnerabilities and exploits.
The Cyber Daily identifies specific technical indicators published recently that are currently trending in noteworthy ways. These IT security trends are culled from over 750,000 sources from the entire web.
The Cyber Daily provides vulnerability managers and other threat intelligence analysts an awareness of emerging threats without hours of manual searching or alert review.
Building Awareness
As a subscriber to the Cyber Daily, a vulnerability manager can open his or her email and see the top identified vulnerabilities reported during the past 24 hours with language indicating malcode activity. These language indicators range from security research (“reverse engineering,” “proof of concept”) to malicious exploitation (“exploited in the wild,” “weaponized”).
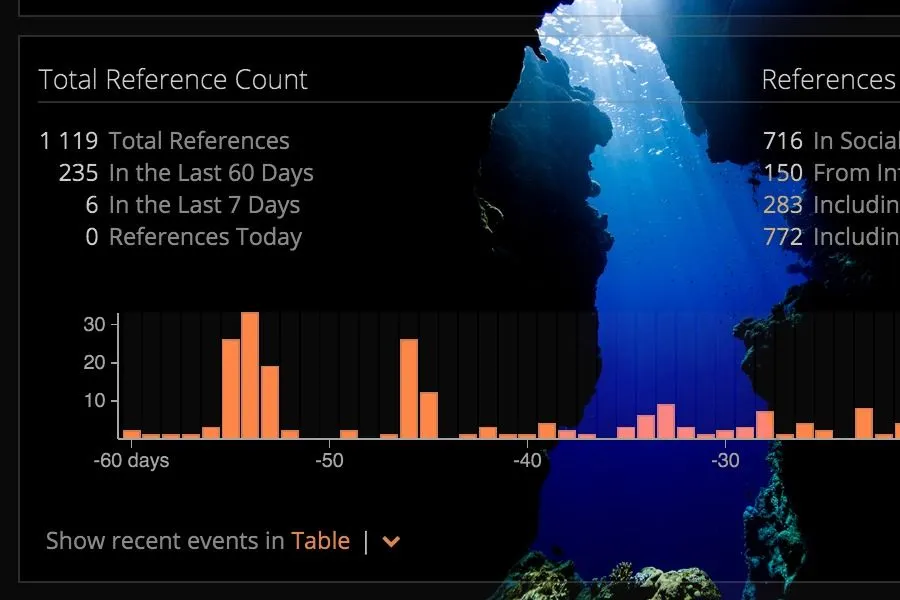
In the example below, a quick look at Adobe vulnerability CVE-2015-8651 reveals ties to an exploit kit with multiple references. These values are counts of how often the CVE is mentioned in documents from the covered time period.
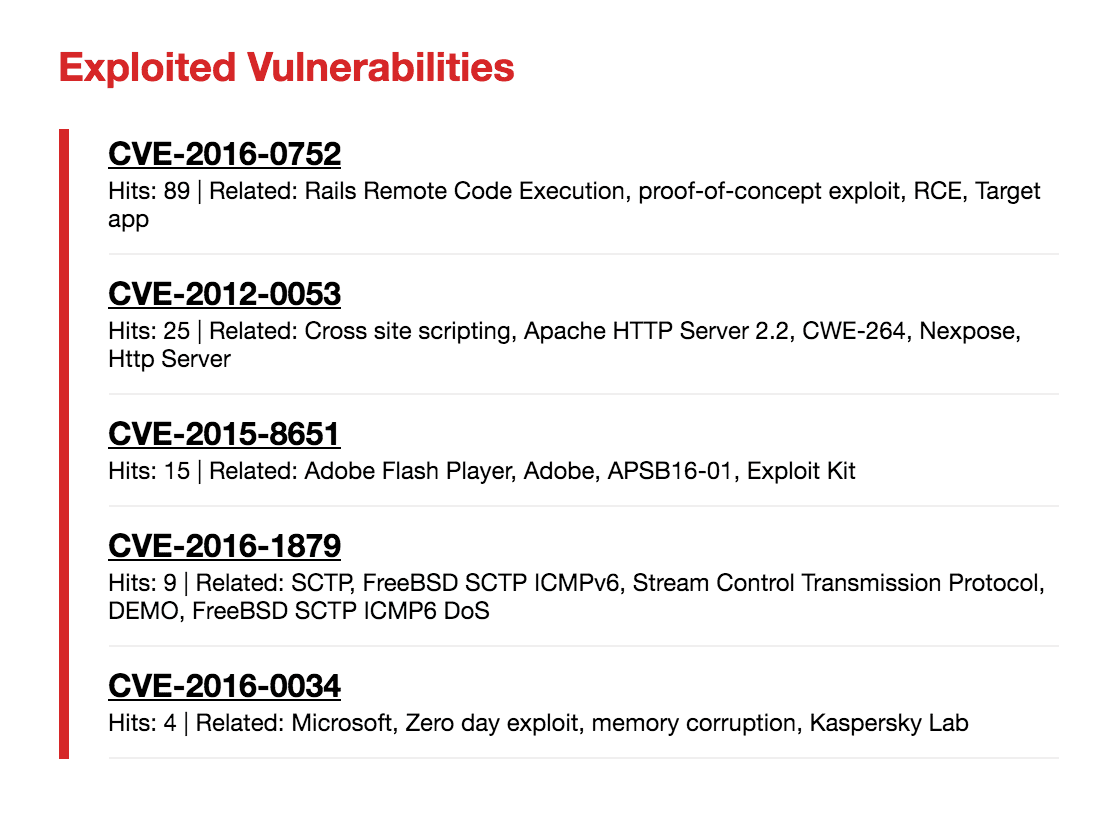
Recorded Future's unique ability to highlight the exploitation of vulnerabilities can help a vulnerability management team prioritize threats. For example, with the knowledge in the example above, the team can investigate whether this vulnerability has affected his or her strategic assets and begin planning for patch scheduling (if a patch is available) before the vulnerability becomes a larger threat.
However, it’s in the vulnerability manager’s best interest to perform full due diligence. The Cyber Daily allows readers to click on the exploited vulnerability to glean more insight.
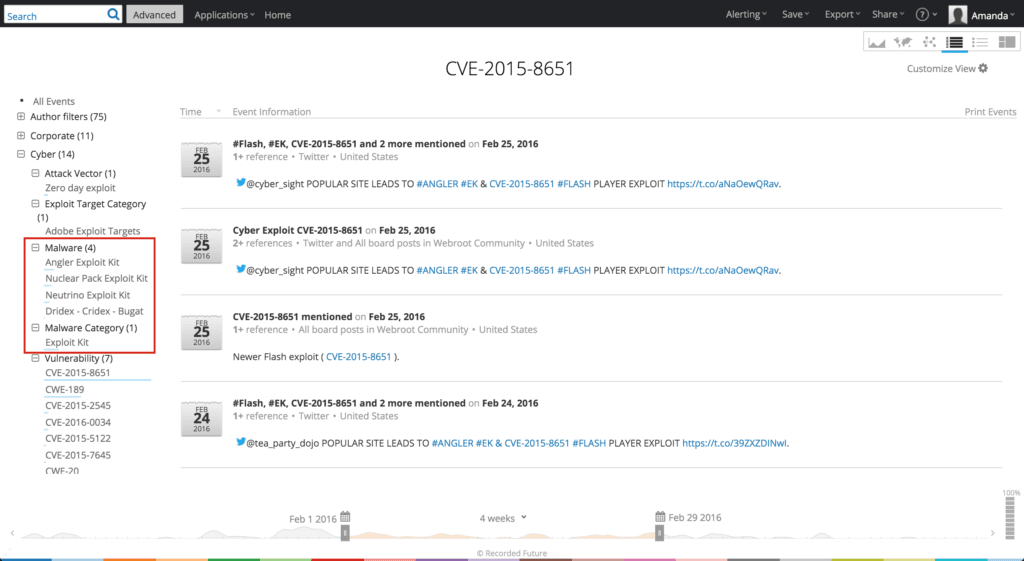
Upon clicking into the Recorded Future web application, information is presented in a table view (figure below), allowing a user to quickly cull key associations with malware, payloads, and other technical information. Additionally, the left-hand column provides further drill down into information such as author filters, malware information, indicators and observables, and more.
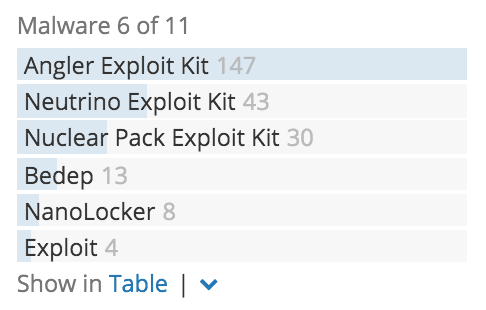
The quick takeaway here is the vulnerability in question, CVE-2015-8651, is leveraged by two prominent exploit kits: Angler and Neutrino.
All of this information provides an overall awareness of exploited vulnerabilities and other trending threat intelligence information. And while this awareness is critical for vulnerability managers to do their jobs effectively, it is best to go a step further and analyze what this information actually means.
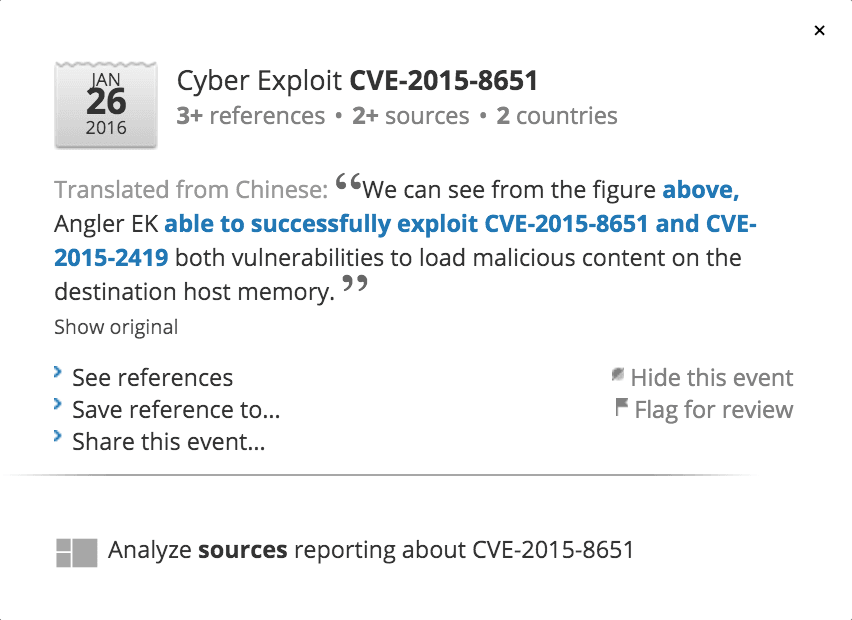
Let’s drill down deeper into CVE-2015-8651.
Analysis Made Simple
To discover more information about CVE-2015-8651, the user can simply click on the vulnerability and a window will appear with action items.
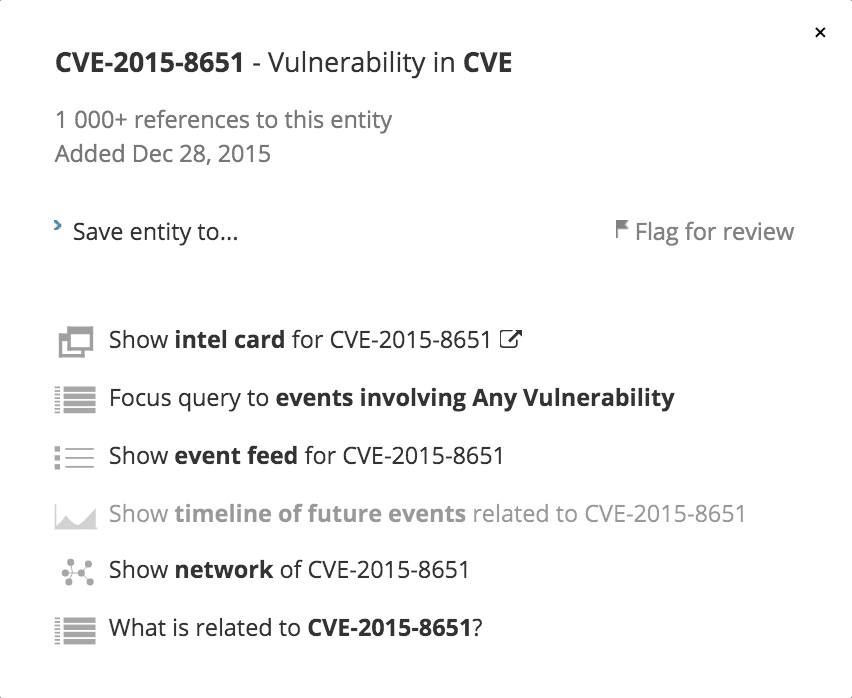
For example, vulnerability managers can leverage Intelligence Cards™ (from the option shown in the above figure), which bundle essential information related to a technical indicator of interest. Recorded Future provides several types of Intelligence Cards™ including:
- IP address Intelligence Cards™ provide an evidence-based, dynamic risk score. Reported associations with domains, malware, and other IOCs are also highlighted.
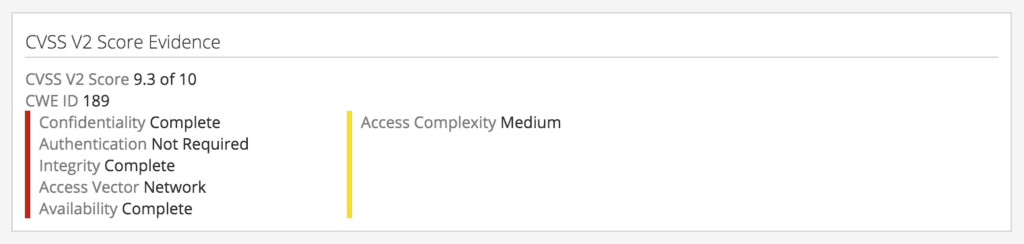
- Vulnerability Intelligence Cards™ pull relevant information together from primary sources including the National Vulnerability Database and web forums to identify exploits. Affected products, associated exploit kits, and IOCs are highlighted, as well as threat actors selling exploits and researchers sharing proof concepts (POCs).
Please note that the free version of the Cyber Daily provides a limited view of Intelligence Cards™ for subscribers. For full access to the Intelligence Cards™, you must be a Recorded Future customer.
For the purpose of this blog post, we’ll focus on the vulnerability Intelligence Cards™.
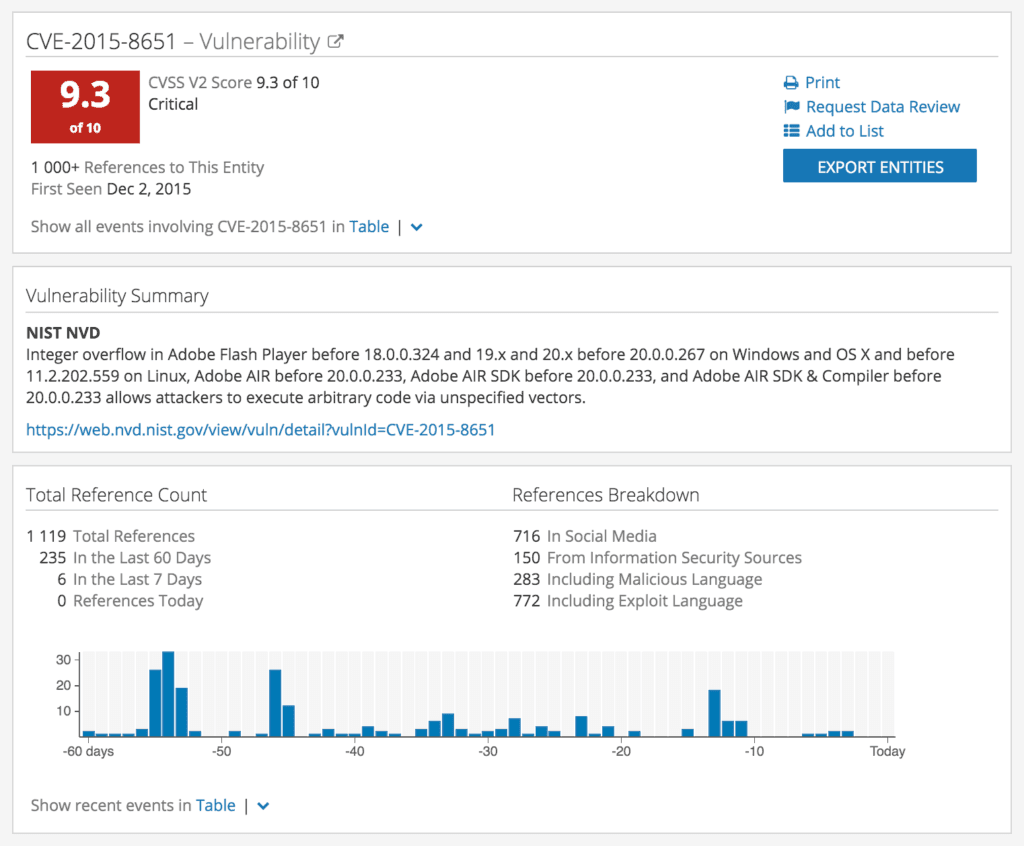
At the top of the Intelligence Card™ you can see the Risk Score — a dynamic, evidence-based score that considers information extracted from web sources (including social media, .onion web forums, and information security repositories) and over 30 threat feeds (including list of Tor nodes, C&C servers, etc.). For vulnerabilities reported by NIST NVD, the vulnerability card presents the CVSS risk score determined by NVD. The higher the number, the more dangerous the threat.
The Vulnerability Summary and Total Reference Count provide additional details that the vulnerability manager can use to determine the importance of the exploited vulnerability.
Next, the Cyber Events section detects reports of exploited vulnerabilities by security researchers — ranging from exploit kits to publicly available information.
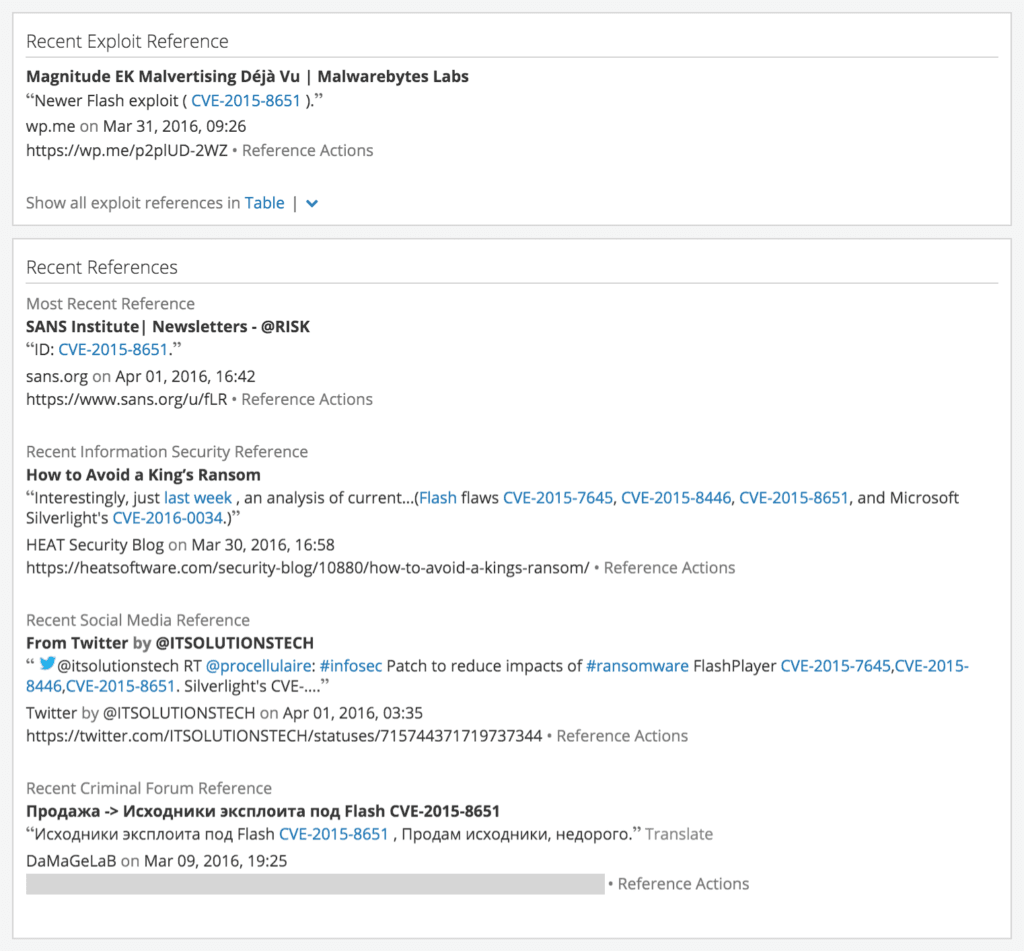
All references to the vulnerability are detected as sources and included on the card. The references are from every part of the Web, including the dark Web.
The Related Entities section (figure below) provides context to the vulnerability, including associated products, vulnerabilities, IP addresses, hashes, and malware. This can include exploit kits and popular payloads (in this case, ransomware known as NanoLocker).
Full Context in Half the Time
Armed with these insights, a vulnerability manager is able to determine the severity of the threat, how likely it is to affect the company, and begin determining the cost of mitigation or recovery. A process that used to take days, can now take hours or even minutes.
Recorded Future’s Cyber Daily provides unique situational awareness to emerging threats. Using the full power of the Recorded Future application, including the new Intelligence Cards™, subscribers can analyze threats quickly, complete with full context — something that, until now, has been very hard to come by.
Related