CVE-2022-39952: Pre-authentication Code-execution Vulnerability
CVE-2022-39952: Fortinet FortiNAC Pre-authentication Code-execution Vulnerability
Fortinet has discovered a vulnerability in the FortiNAC web server which allows unauthenticated arbitrary file access. A patch to address the vulnerability which was assigned CVE-2022-39952 is available. The recommended action is to update to a patched version as soon as possible, as the arbitrary file access also directly allows unauthenticated remote code execution.
Fortinet FortiNAC is a network access control (NAC) solution that employs a policy-based approach to control which devices and users are allowed to connect to the network and how they can interact with resources. It has further features that include automated network discovery, device profiling, and integration with other security products.
Fortinet confirmed in their PSIRT advisory that the following versions are affected:
- FortiNAC version 9.4.0
- FortiNAC version 9.2.0 through 9.2.5
- FortiNAC version 9.1.0 through 9.1.7
- FortiNAC versions 8.3 through 8.8
The vulnerability is mitigated in versions 9.1.8, 9.2.6, 9.4.1, or above.
An investigation by horizon3.ai revealed that the attack vector is unsecured directory traversal during unpacking of a user-supplied zip file: A module of the FortiNAC web server allows the upload of a key file, which is subsequently unzipped. Any contained file with an absolute path is placed on the same path on the target system. A proof of concept uses this to add a malicious cron job by adding a file to /etc/cron.d. Additionally, any file already present on the system will be overwritten. In theory, an attacker could use this to overwrite ssh’s authorized_key files to get full ssh access while simultaneously locking out any existing accounts.
First reports from compromised systems suggests that at least in some cases, attackers place the files fortii.jsp or shell.jsp in the /bsc/campusMgr/ui/ROOT/ directory. No other indicators of compromise are known so far. Since the patched versions removed the file /bsc/campusMgr/ui/ROOT/configWizard/keyUpload.jsp, its presence indicates that a system is still vulnerable.
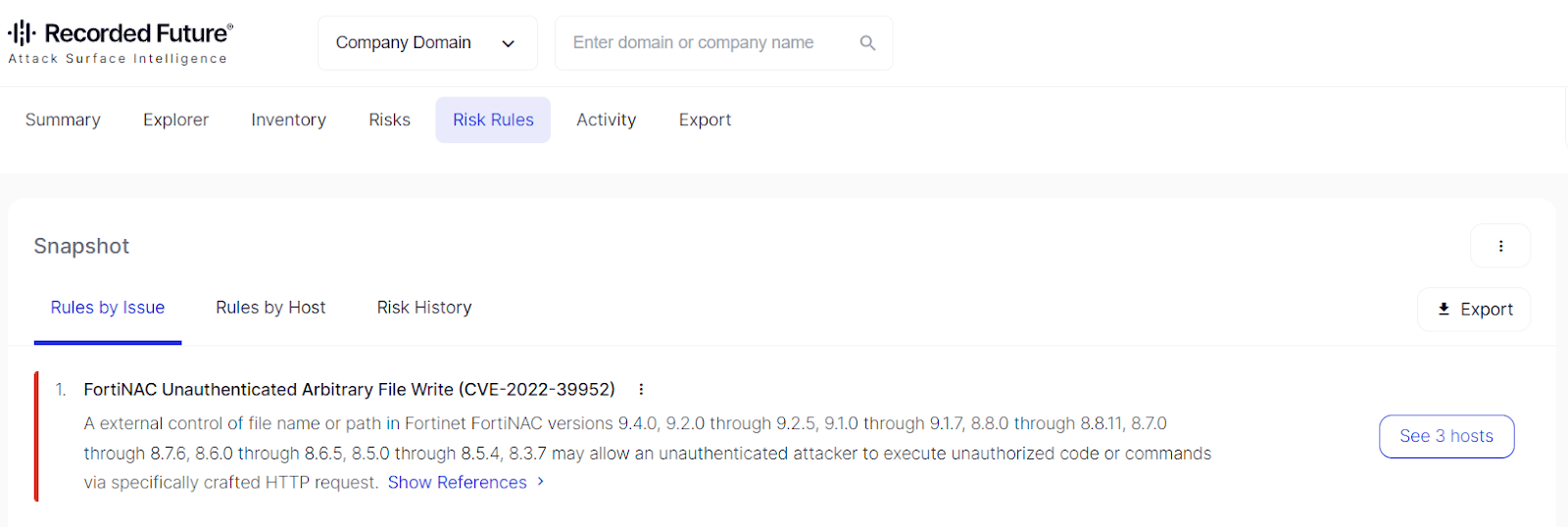
The Recorded Future Attack Surface Intelligence platform detects vulnerable versions, and a risk rule alert will show up if a host in your project is affected.
If you're concerned about your organization's attack surface security posture, don't hesitate to book a demo today. Our team of experts can walk you through how the platform works, show you how to use it for effective asset discovery and monitoring, inventory management, risk detection, and answer any questions you might have.
Related