Attack Surface Intelligence: A Vital Piece of the Critical Infrastructure Protection Puzzle

Cyberattacks on critical infrastructure (CI) can have devastating consequences, ranging from the loss of business continuity to the loss of life.
With cases like the recent attack on Qulliq Energy Corporation continuing to make the headlines, threat actors know that targeting public services can cause significant disruption and damage. These attacks can have far-reaching consequences for organizations, communities, and individuals relying on these services.
In this post, we'll explore the remarkable contribution of Attack Surface Intelligence in curbing the rise of cybercrime and the role of specific threats on CI, such as ransomware or phishing attacks, in adding inspirited new challenges to the discussion. Encouraged by our success in helping organizations take action against these and similar threats, we hope to inspire you to look closer at their significance and impact.
What are the top threats affecting Critical Infrastructure?
Several compelling threats can affect CI, but some of the most common and significant ones include the following:
Ransomware
Rising well above the upper echelons of cybercrime, Ransomware continues to pose an existential threat to an untold number of organizations. This year alone, reports conclude that organized crime has doubled down efforts to make this exceedingly prominent form of cyberattack more damaging than ever. Below-average targets, such as lower education institutions, have become equally vulnerable, with additional indicators suggesting that new extortion mechanisms are underway.
Although ransomware is primarily considered a human-centric problem—given the overarching influence and impact of user behavior leading to victimization—the importance of the expanding attack surface cannot be overstated, and miscreants certainly know it.
ICS attacks
Industrial Control Systems (ICS) refers to the analog and digital architecture used to control industrial processes and other CI—this includes infrastructure critical to the proper functioning of entire societies and economies, such as power grids, water systems, and telecommunication networks. It predominantly consists of computer hardware, software, and industrial middleware used to control and monitor various functions and equipment in an industrial or manufacturing environment.
The oil and gas production conglomerates are exceptionally vulnerable to this behavior due to their dependence on intricate systems. In turn, the consequences of a successful cyber attack on these industries can be severe, including disruptions to production, the loss of sensitive data and property, and even environmental disasters.
As the industry becomes increasingly digitized, companies must proactively protect themselves against cyber threats and ensure continuity. One essential risk to this process is the scope and complexity of the ever-shifting attack surface, which boils down to the total number of vulnerabilities attackers could exploit. In this context, Attack Surface Intelligence can be leveraged to identify vulnerabilities, prioritize remediation, and implement suitable measures to reduce the overall risk of an attack.
Insider threats
Insider threats pose a significant risk to CI and similar operations. These threats can come from individuals with authorized access to the system, such as employees, contractors, or business partners. They may have a malicious intent component, such as sabotage or theft of sensitive information, or they may accidentally introduce vulnerabilities through poor security practices.
Insider threats are usually challenging to detect because the perpetrators typically have legitimate access to the system. They may also have detailed knowledge of the architecture and processes, making it easier for them to evade detection and carry out attacks.
Attack Surface Intelligence can help organizations identify and mitigate insider threats by providing visibility into potential vulnerabilities and areas of exposure—this includes:
- Employee monitoring: By monitoring employee activity, organizations can identify any unusual or suspicious behavior that may indicate an insider threat.
- Access controls: Implementing strict access controls can prevent unauthorized access to vital systems and data.
- Network segmentation: Segmenting networks can limit the potential impact of an insider attack by restricting access to certain areas or procedures.
- Regular security assessments: Regular security assessments can identify the organization's vulnerabilities and help mitigate them before an insider can exploit them.
- Training and awareness programs: Providing employees with training and awareness programs can educate them on the risks of insider threats and encourage them to report any suspicious activity.
Physical attacks
Physical attacks on CI refer to any form of sabotage or destruction that occurs on a physical level, such as vandalism or tampering with equipment. These attacks can have severe consequences, including power outages, disruption of essential services, and financial damage.
Using Attack Surface Intelligence, organizations can proactively identify and mitigate potential threats before they occur. For example, if an organization knows that a specific component is prone to tampering, it can take steps to secure it or replace it with a more secure alternative.
How does Attack Surface Intelligence help protect Critical Infrastructure?
As mentioned, Attack Surface Intelligence applied to CI refers to the understanding and knowledge of vulnerabilities and potential weaknesses that attackers could exploit. Sparking a revolution in the threat detection landscape, this type of actionable intelligence is essential because it allows organizations to identify and prioritize the most urgent vulnerabilities and assets while implementing appropriate countermeasures to reduce the overall risk of an attack.
Ever since the Colonial Pipeline Incident in 2021, the focus has shifted to improving cybersecurity measures to protect ICS (and equivalent systems) and prevent similar incidents; this includes an in-depth look at the attack surface as a precursor to identifying vulnerabilities to protect against external threats. Also paramount to this effort is the need to employ passive asset discovery and detection mechanisms to avoid negatively impacting highly-sensitive equipment, among similar concerns.
Our Attack Surface Intelligence platform helps prevent CI attacks by providing organizations with near real-time visibility and analysis of their attack surface, including identifying and tracking potential vulnerabilities, monitoring suspicious activity, and providing insights on mitigating threats.
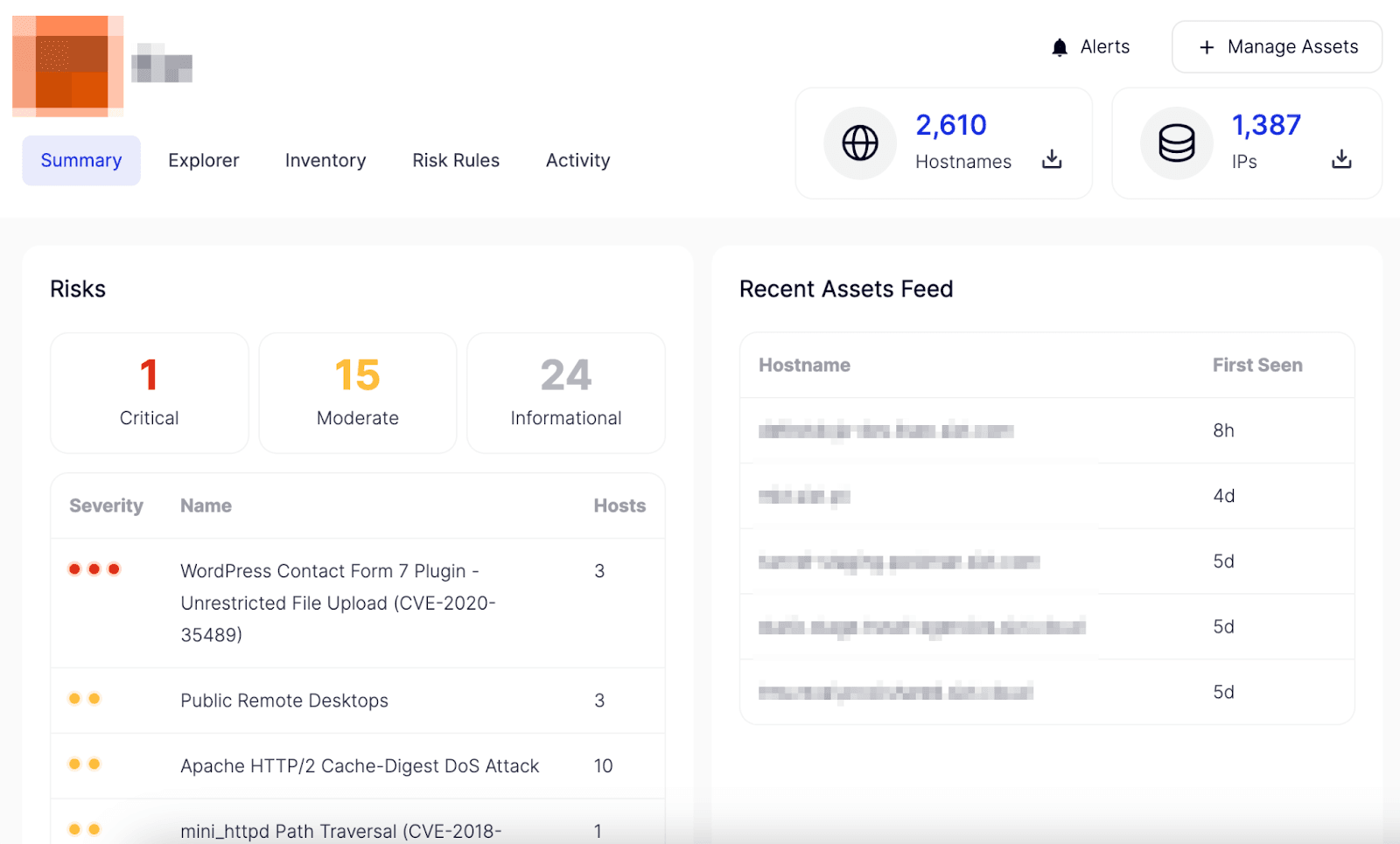
Lastly, Attack Surface Intelligence’s ability to protect CI extends to the complete knowledge of any misconfigured hosts, system vulnerabilities, and emerging threats related to the larger IT-OT environment, namely the integration of traditional IT infrastructure and its ICS counterparts. Consequently, analysts can swiftly evaluate the risk level before cybercriminals can access more valuable targets.
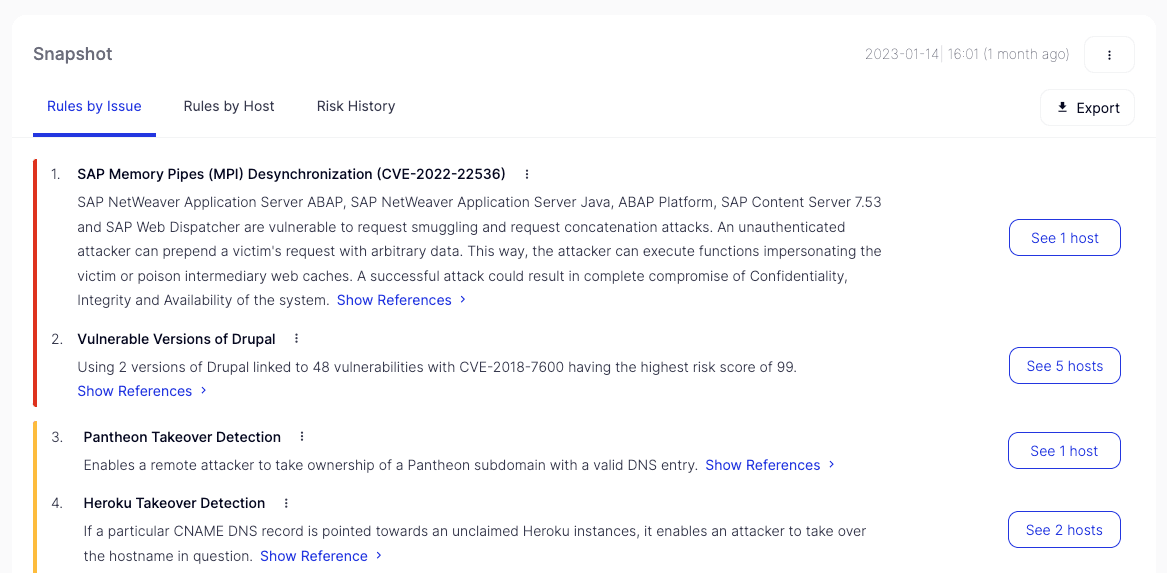
Summing up
Cybercrime targeting CI can take many forms. From ransomware episodes to insider attacks, these events can disrupt services, cause financial losses, and even physical damage or destruction.
Improved risk assessments, reduced downtimes, cost savings, and an enhanced security posture: These are some of the benefits associated with Attack Surface Intelligence, and they can all be yours in the daily struggle for resiliency against cyber threats, whether targeted or not.
Finally, improving cyber resiliency for critical infrastructure requires a combination of technical measures and robust security practices. It is also essential to have a well-defined incident response plan to address any attacks that do occur.
Recorded Future’s Attack Surface Intelligence helps Critical Infrastructure organizations improve asset visibility, minimize attack surface complexity, and reduce detection time. Book a demo today to learn more from our experts.
Related