Asset Discovery in the ICS/OT domains: Challenges and Opportunities
Driving significant change in the digital transformation era is no easy feat. Apart from the exigencies placed by first-to-market conditions and similar drivers, aspiring leaders in this arena must contend with a hodgepodge of disparate technologies just to keep pace with the growing demands. In doing so, however, entities are often saddled with a host of asset discovery and management woes that threaten the very fabric of any modern cyber defense program, and legacy implementations and systems are particularly susceptible to this reality.
But even if competitive advantage isn’t one of the desired outcomes—as in the case of industry verticals supported by Operational Technology (OT) and Industrial Control System (ICS in its plural form) collectives—asset reconciliation in these fixed-inventory ecosystems is still considered a top priority. This rationale takes an even deeper meaning if we also examine the buoying IT-OT convergence: A phenomenon marked by a shift from a motley of monitoring and control mechanisms to a cohesive IoT (Internet of Things)-based model signaling improved networking, storage, and instrumentation capabilities. Further complicating this picture is an ever-present menagerie of specialized communication protocols, with identification challenges arising partly from a small subset of these outside the aegis of the TCP/IP stack.
Owing to ICS’ dominant role in the operation and security of critical infrastructure, we premise this post on the idea that obtaining an accurate asset inventory within such environments is riddled with inherent technical and safety hurdles. Under the guidance of NIST’s Special Publication 800-82, we’ll attempt to provide a decent margin for understanding such historical constraints and some awareness of the road ahead.
Framing the challenges: A primer of ICS terminology and protocols
ICS are the digital and physical control lifeblood of the modern industrial complex. From oil and natural gas operations to food and beverage business conglomerates, ICS are vital to the proper functioning of highly-sensitive components. Hitherto, they’ve acquired a high degree of autonomy and isolation from traditional IT networks, and for good measure: an overriding human safety factor precedes any other underlying implication. For instance, a recent path traversal vulnerability discovered in flow computers—a special-purpose digital device accounting for the fiscal transfer of hydrocarbons—is believed to pose the same risks as those which led to the now-infamous Colonial Pipeline incident.
So, if restricting physical and logical access to these environments is critical to prevent disruptions, it is relatively common to find ICS employing some form of air gap scenario—when properly implemented and supervised, this kind of segmentation between the more prominent IT and ICS/OT topologies can provide reasonable assurance. Embedded in the latter is where we’d find the likes of programmable logic controllers (PLCs) or remote terminal units (RTUs); these represent low-level control systems with the ability to send equipment telemetry and data from field instruments either wirelessly or via standard communication cables.
Predictably, all these data retrieval and update functions call for centralized administration, and that’s where Supervisory Control and Data Acquisition (SCADA) systems come in; in turn, SCADA implementations are capable of handling a multitude of geographically dispersed assets in near real-time, automating any resulting tasks under a single visualization dashboard known as a Human-Machine Interface, or HMI.
Setting ICS/OT and IT even further apart is an entire proprietary and legacy array of dedicated protocols—these include:
DNP3: An early fixture of the utility sector, this TCP/IP-based protocol provides the messaging scaffold and rules used in substation local area networks (LANs) linking remote equipment with their corresponding control centers. Originally designed with interoperability and optimization in mind, the DNP3 international standard is still widely popular, with electrical and water industries leading the way in its implementation.
Modbus: Introduced in 1979, Modbus also encapsulates and sends commands and data over TCP/IP. Born a serial, point-to-point, and response-request protocol, Modbus quickly outgrew any proprietary messaging structures in favor of an Ethernet-based variant to accommodate the growing demand for concurrent, long-lived connections.
ICCP: ICCP, or the TASE.2 protocol, is the de facto standard that transmits process control data between utility control centers and similar energy-accounting infrastructure. This real-time data exchange takes place in client-server fashion, with secure extensions relying on transport layer security mechanisms for encryption and authentication purposes. Unlike Modbus, ICCP consists of a multi-layered stack of protocols specifically designed to work over LANs, although its ability to cross organizational boundaries is well established.
RS-232 and RS-485: Despite early distance limitations and similar drawbacks, these serial (or parallel) communication interfaces are still commonplace due to their reliability and simplicity. Introduced in the late 1990s—apropos of the evolving computer peripheral industry—the RS-485 standard embodies the latest in rugged physical design destined for harsh industrial environments where large amounts of electrical noise immunity and other special safety features are typically required.
Of course, the list above is by no means exhaustive. There are additional protocols like BACnet or Profibus, whose open-standard nature has ensured continuous growth in the automation sector, specifically in the centralized management of measuring equipment and RTUs.
Securing ICS: Asset management challenges and beyond
As it stands, the siloed ecosystem that was once ICS/OT has seen a steady increase in the adoption of corporate-like IT solutions and technologies ranging from low-cost physical layer devices and transmission media to operating system considerations that resemble mainstream client-server solutions. Citing enhanced remote connectivity and better data collection capabilities, the groundwork is also being laid for older, proprietary equipment and protocols to be replaced by a new wave of Industrial Internet of Things (IIoT) applications.
This so-called convergence, however, has its detractors. Without risking oversimplification, the divide is mainly rooted in the merging of the threat and risk management domains—a cross-functional challenge with unforeseen ripple effects that may threaten ICS’ long-held stance on the protection of critical control systems and assets having a direct impact on human populations. Unmistakably, this involves the role of state-sponsored threat actors and espionage groups historically known to target critical infrastructure, as well as an increase in “living off the land” techniques and run-of-the-mill malware (retrofitted for ICS use) demanding less technical skills yet proving highly effective in rendering entire ICS networks powerless against certain types of attack.
Regardless of complexity level, proper asset inventory and reconciliation at the intersection of such seemingly disparate worlds can become daunting, as most attack surface intelligence platforms aren’t equipped to handle this sort of integration at any significant scale.
Paramount to this effort is (mainly) the utter need to employ passive asset discovery and traffic analysis if one is to preserve the operational integrity of highly-sensitive equipment; in essence, the reaching of a state commonly referred to as a “single source of truth” whereby data-driven decision-making is backed by a centralized, authoritative source of asset information without being overly intrusive to any running operations.
Where does Recorded Future fit?
Since the inception of Recorded Future’s Attack Surface Intelligence platform, we’ve extended coverage for specific ICS/OT areas, including:
- Asset discovery: Attack Surface Intelligence mainly relies on passive historical records for asset discovery—this applies to a specific portion of the ICS and OT inventory space, where asset data (residing at the router/switch/firewall network level) can be easily detected by our asset discovery engine.
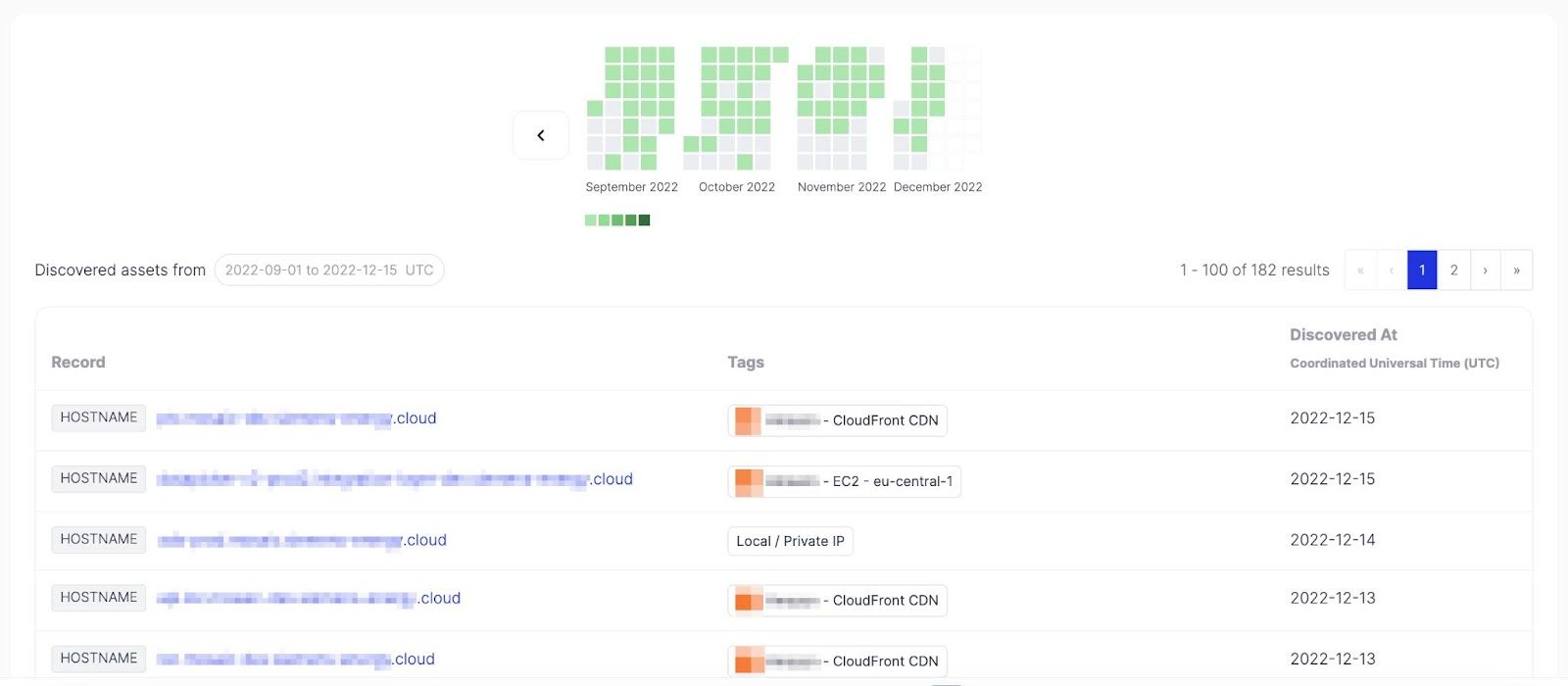 Discovered assets from a worldwide energy company that uses multiple ICS-OT devices
Discovered assets from a worldwide energy company that uses multiple ICS-OT devices
- Exposed ports: Different protocols we scan for, such as:
- 502 (Modbus)
- 20000 (DNP3)
- 4000 (ROC Plus / Terabase)
- 47808 (BACnet/IP)
- 9600 (OMRON FINS)
- 2222 and 44818 (Ethernet/IP)
- And many others
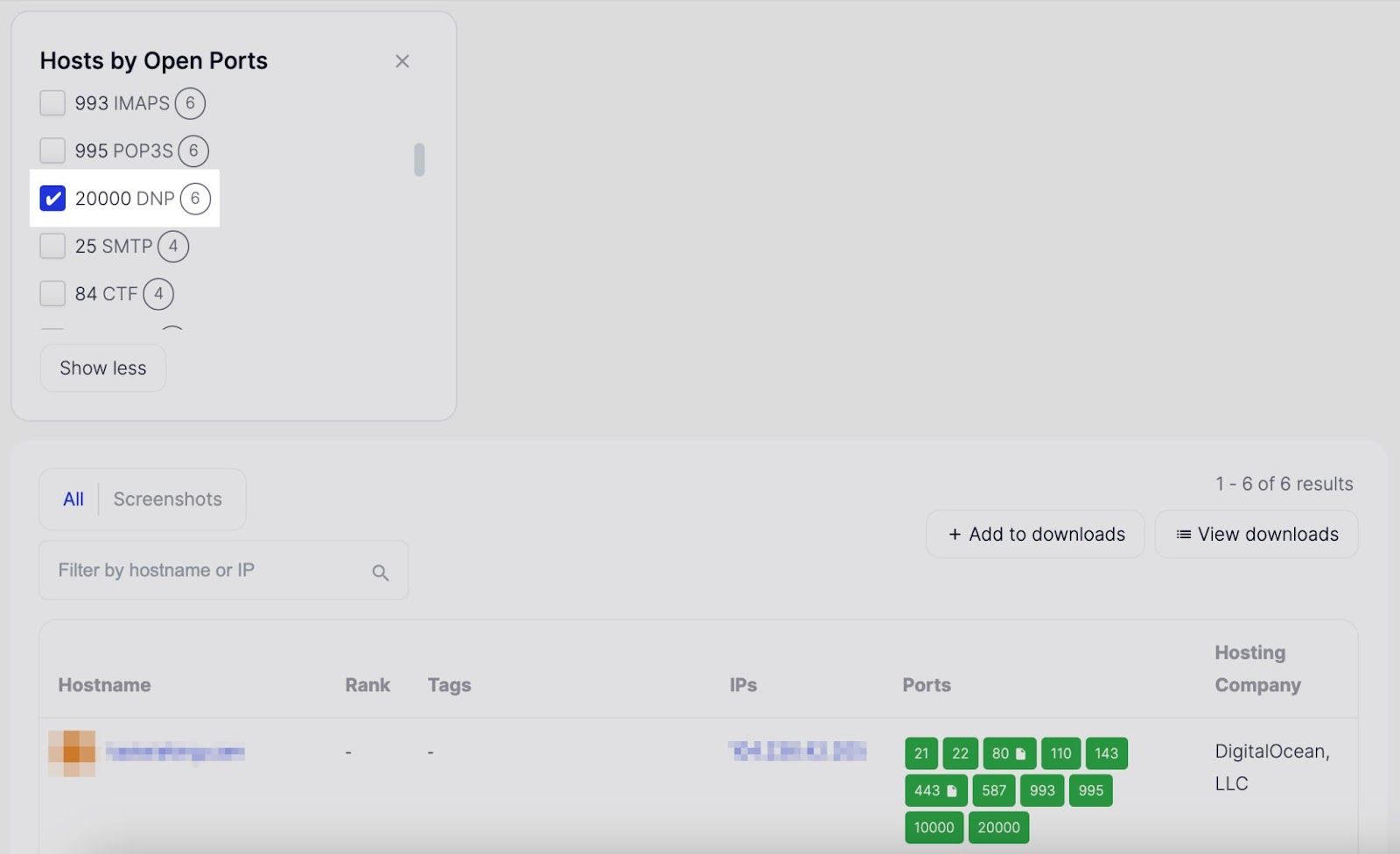 An organization exposing port 20000 (DNP) to the public
An organization exposing port 20000 (DNP) to the public
- Exposed admin panels: Some of the panels we detect are related to software running on factory floors, buildings, plants, and farms—these include:
- Tectuus SCADA Monitor
- SCS Landfill RMC
- Emerson Network Power IntelliSlot Web Card Panel
- Nordex Control - Wind Farm Portal
- PowerLogic ION
- And many others
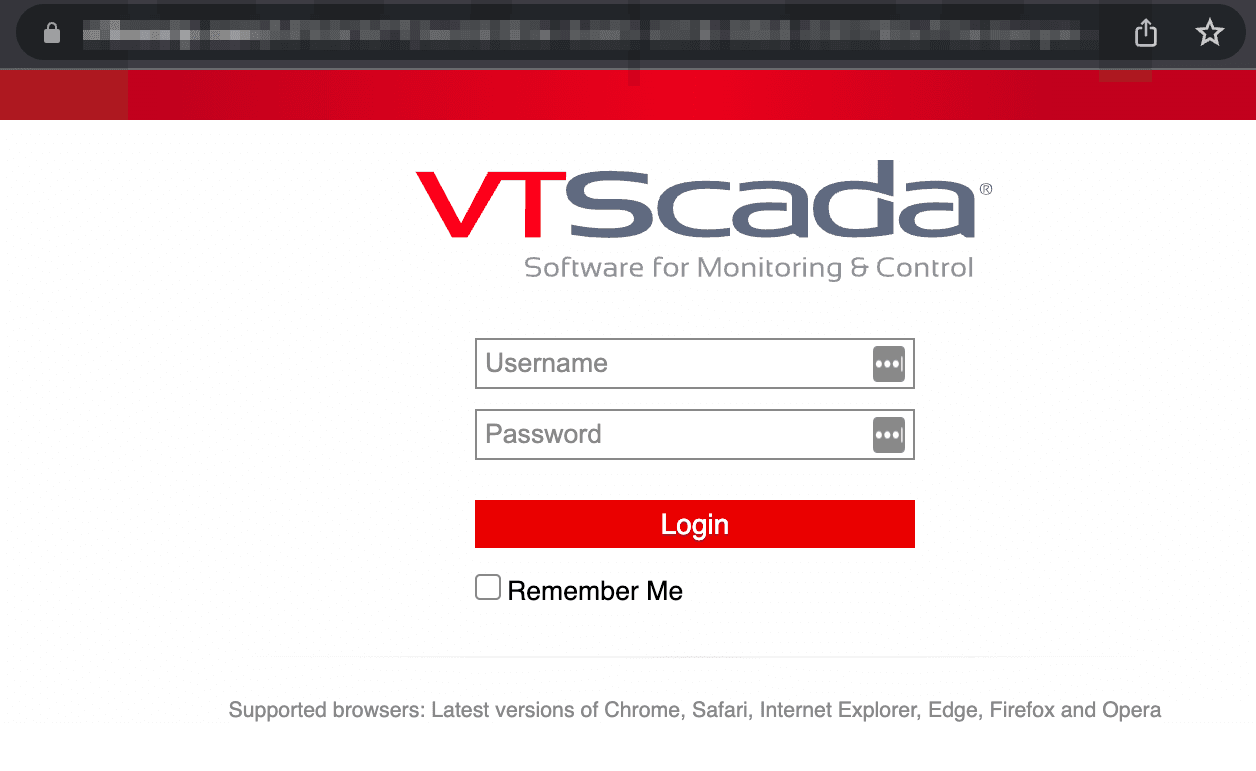 Screenshot of a publicly VT Scada exposed control panel.
Screenshot of a publicly VT Scada exposed control panel.
- Risk detection: Last but far from least, Attack Surface Intelligence can provide you with a comprehensive view of any potential misconfigured hosts, vulnerabilities, and emerging threats related to the larger IT-OT environment, allowing analysts to quickly assess the level of risk involved before cybercriminals find a way to pivot to more critical systems.
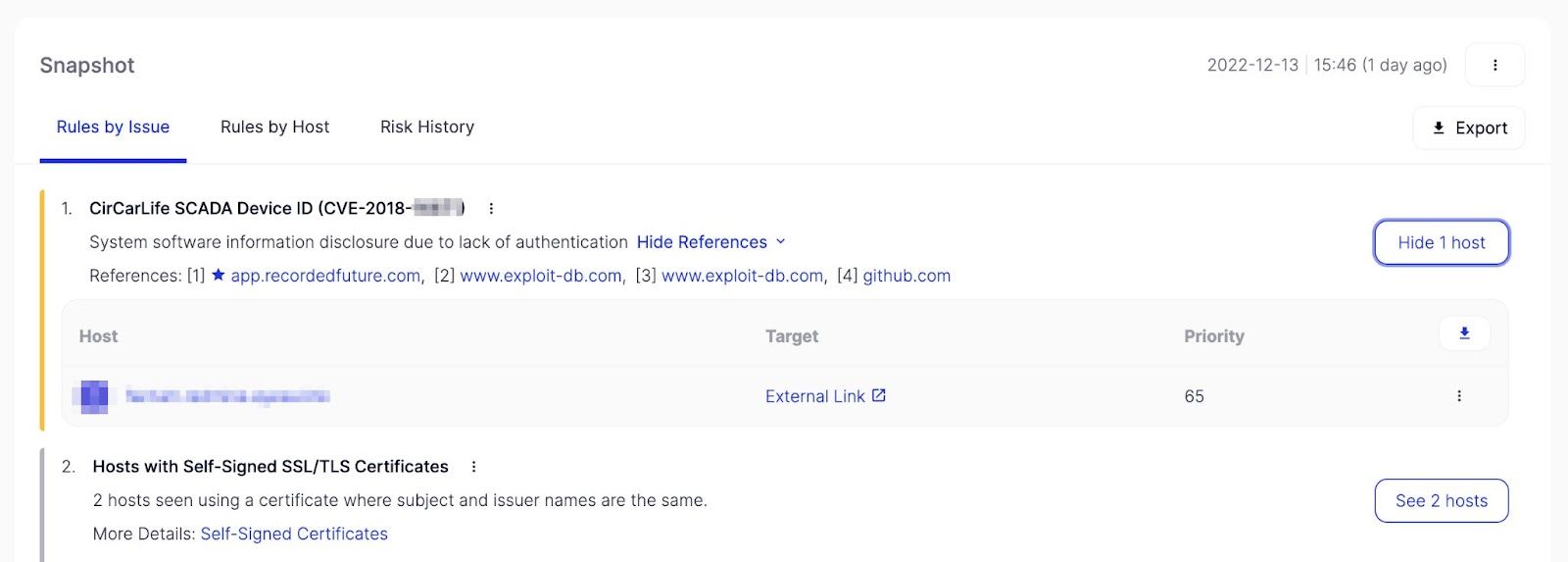 Risk Rules engine showing a CirCarLife SCADA Device CVE detection
Risk Rules engine showing a CirCarLife SCADA Device CVE detection
To recap
In the minds of many, much of the underlying ICS/OT physical controls and protocols remain a relic of the past—arguably, at least, a cacophony of disparate, bespoke technologies in dire need of serious upgrading. In turn, cybersecurity and industry experts worldwide agree that the expectation that ICS/OT will forever remain this fully-isolated, impervious ecosystem is duly unfounded, as these critical systems become increasingly vulnerable to cyberattacks bleeding from the larger (and less secure) IT space.
Despite the ongoing presence of close-knit, proprietary solutions and the perceived notion of a reduced attack surface, ICS/OT inventories everywhere will continue to grow at a pace primarily dictated by the addition of more public-facing endpoints and technologies in support of a growing mobile workforce, to name one factor.
The same conventional wisdom applies to complete asset visibility—the preeminent risk assessment condition signaling strong maturity levels across every industry vertical. Through Attack Surface Intelligence, risk mitigation begins with the passive discovery and detection of any asset at the intersection of the IT-OT boundary, a welcomed advantage to any cyber defense strategy.
Related
