Annual Payment Fraud Intelligence Report: 2022

Editor’s Note: This is an excerpt of a full report. To read the entire analysis with endnotes, click here to download the report as a PDF.
This report provides trends and metrics for the payment card fraud landscape in 2022 and identifies the merchants most frequently compromised or abused as tester merchants. The target audience of this report is fraud and cyber threat intelligence (CTI) teams at financial institutions and merchant services companies.
Executive Summary
2022 was a year of system shocks, and the payment card fraud market did not survive unscathed. Russia’s cybercrime crackdown — followed promptly by its full-scale invasion of Ukraine in February 2022 — spawned lower carding volumes for the remainder of the year. In total, 2022 saw 45.6 million card-not-present (CNP) and 13.8 million card-present (CP) payment card records posted for sale to carding shops on the dark web. These figures were considerably lower than the 60 million CNP and 36 million CP records posted for sale in 2021. Taken together, this decreased supply, demand, and turnover defined the payment card fraud market and threat landscape throughout 2022.
In spite of this, the card fraud market and the threat actors who populate it demonstrated remarkable resilience. Magecart actors launched campaigns that employed fake payment card forms, exploited legitimate merchant web infrastructure to deploy e-skimmers, and used HTTP referer headers to impede remediation by security analysts. One of these campaigns led to the compromise of 2 online ordering platforms, a trending tactic that exposes merchants who use the platforms to the risk of being compromised. Meanwhile, high-profile merchants were increasingly exploited by individual threat actors and checker services on the dark web in order to verify the validity of stolen cards. And finally, as war in Ukraine hampered cybercriminals’ ability to engage in card fraud, one top-tier carding shop exploited the lull in supply by flooding the market with recycled payment card records. Although frustrated by these records’ low quality, resourceful threat actors may nevertheless use them as cheap sources of personally identifiable information (PII) that they can weaponize to carry out targeted account takeover (ATO) attacks against their victims.
By employing proactive anti-fraud strategies that integrate intelligence from throughout the payment fraud life cycle, financial institutions and card issuers can reduce card fraud losses in 2023. The overall level of card fraud activity in 2023 will be highly dependent on whether or not Russia’s war in Ukraine continues; if it does, threat actors’ ability to engage in card fraud will likely remain degraded. But should the war end, a renewal or increase in payment card fraud may follow.
Key Findings
- 45.6 million CNP payment card records were posted across dark web carding shops in 2022, down 24% from 2021. It is highly likely that this year’s relatively low CNP volumes are the result of Russia’s early-2022 cybercrime crackdown and its subsequent full-scale invasion of Ukraine. In 2022, the highest-impact CNP breaches affected online ordering platforms.
- 13.8 million CP payment card records were posted across dark web carding shops in 2022, down 62% from 2021. While it is possible the year’s events contributed to this drop-off, year-by-year CP volumes have also steadily declined due to the rising global adoption of more secure in-person payment methods. In 2022, CP breaches overwhelmingly affected small restaurants and bars.
- The Recorded Future® Magecart Overwatch program discovered 1,520 unique malicious domains involved in the infections of 9,290 unique e-commerce domains at any point in 2022.
- Full primary account numbers (PANs) for at least 20.5 million compromised payment cards were posted as plaintext or images to various resources including dark web forums, pastebins, and social media.
- 21 card checker services monitored by Recorded Future abused 2,953 unique merchants associated with 660 unique merchant identification numbers (MIDs) for illicit card checks.
- Threat actors focused on avoiding or bypassing protections offered by the 3-D Secure (3DS) protocol and increasingly discussed the abuse of customer service call centers as a means of facilitating their attacks. Furthermore, a surge in cheap, reposted payment card records posted throughout 2022 increased the attack surface for ATO attacks.
- The payment fraud life cycle closely resembles a real-world market underpinned by supply chains, coordinated exchange between buyers and sellers, and the provision of services such as checkers. Although this high degree of organization increases the opportunities and impact of card fraud, it also produces a data-rich environment. Therefore, card issuers, acquirers, and merchant service providers should incorporate and integrate intelligence from across the payment fraud life cycle to proactively combat fraud.
Background
Payment card fraud exists as part of a sophisticated underground economy. Production networks, supply chains, and dark web carding shops provide threat actors with the means to market criminal services and wares to their peers or to purvey stolen data to end users who engage in card fraud. Within this shadow economy, payment card fraud conforms to a certain “life cycle”, as seen in Figure 1 below.
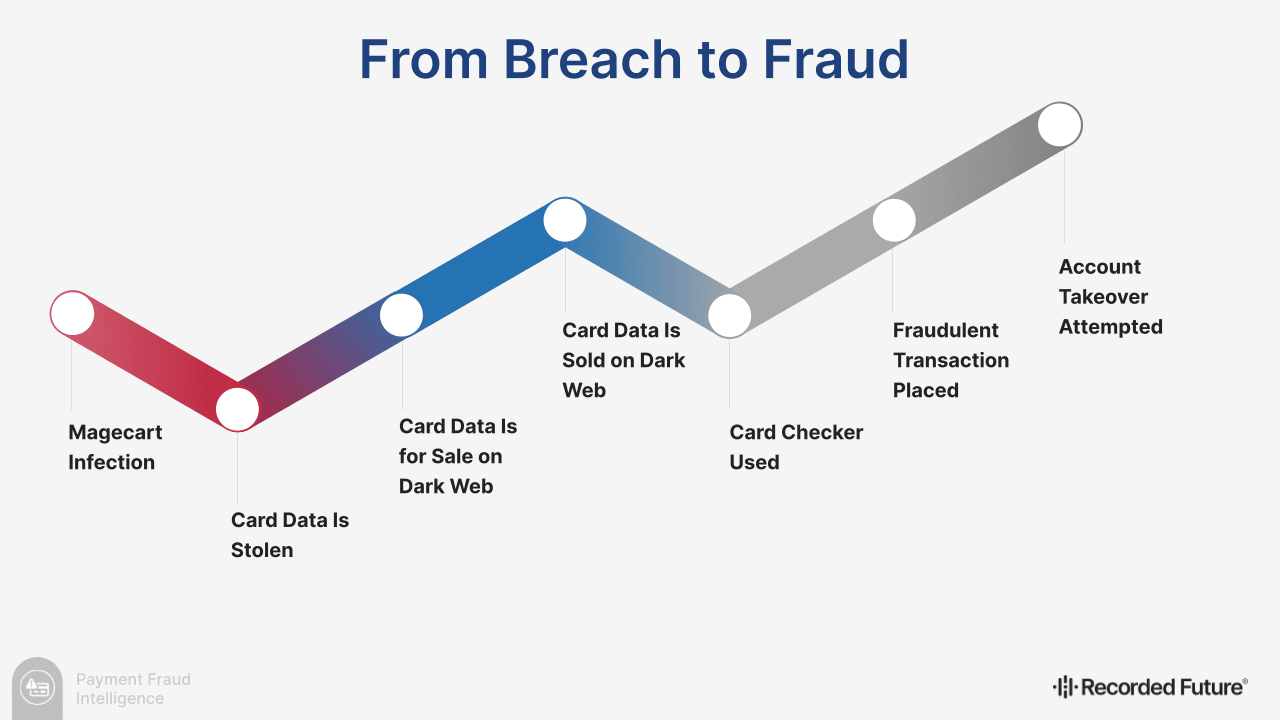 Figure 1: Payment card fraud conforms to a general life cycle (Source: Recorded Future)
Figure 1: Payment card fraud conforms to a general life cycle (Source: Recorded Future)
At the beginning of the life cycle, physical compromises facilitate the theft of payment card data from merchants’ card-present (CP) transactions. Meanwhile, cybercriminals enact digital compromises — often with Magecart e-skimmer infections — to steal card data from online card-not-present (CNP) transactions. These stolen card records are posted for sale to the dark web, where partial payment card data is put on display so criminal buyers can go “window shopping”. Occasionally, carding shops release full stolen payment card data for promotional purposes, which provides one of the many opportunities for criminals to snatch up full primary account numbers (PANs). Before making a sale, carding shops use aptly named checkers to appraise stolen card sets; individual criminals use the same checkers to verify their records’ validity before or after purchase. Once “end user” fraudulent actors acquire their desired payment card data, they monetize it, usually through fraudulent transactions. If actors can acquire enough of a victim’s personally identifiable information (PII), they can even attempt account takeover (ATO) attacks to cash out their victim’s bank account.
Throughout 2022, Recorded Future monitored this shadow economy to empower clients to disrupt fraud at every stage of the payment card fraud life cycle. In the course of our monitoring, we observed both continuing trends from 2021 and novel trends that grew organically from the events of 2022.
Editor’s Note: This is an excerpt of a full report. To read the entire analysis with endnotes, click here to download the report as a PDF.
Related
