5 Ways to Take Your Vulnerability Management Program to the Next Level
If you ask a security practitioner “what is vulnerability intelligence,” the most common answer you’ll receive will be “information to understand if a vulnerability has been exploited in the wild.” And that’s not a bad answer. There were more than 20,000 vulnerabilities disclosed in 2021, but, in reality, only a small percentage will ever be exploited by threat actors in the wild. More than ever, security practitioners need a better way to prioritize what matters most. Using intelligence to identify exploited vulnerabilities is an extremely effective way to create a plan that reduces risk for your organization.
But vulnerability intelligence is significantly more powerful than just finding exploitation; in this blog, we review all of the ways you can use intelligence to supercharge your vulnerability management program.
5 ways to use vulnerability intelligence
Vulnerability research helps you understand the who, what, where, when, and why
When a vulnerability is disclosed, it comes with accompanying details. This helps you understand what the vulnerability does at a high level, what type of system or software it affects, if there is an available patch, and the CVSS rating of that vulnerability. This information is helpful, but it’s often not enough to understand a vulnerability and contextualize it for your business.
Vulnerability research and analysis can prove an invaluable asset for analysts looking to understand a vulnerability on a deeper level. This analysis provides historical context for the vulnerability, technical analysis on how the vulnerability works, requirements to exploit, and analysis of current proof of concept exploit techniques. It also helps organizations understand how easy (or difficult) it might be to apply a patch, as well as their options for mitigation strategies.
This deeper level of research allows an organization to assess how risky a vulnerability is in the context of the wider threat landscape, as it pertains to your business. If, for instance, you know you want to get ahead of a vulnerability if there’s a specific APT known to target your industry and peers that uses that specific vulnerability.
For a direct example of what vulnerability research looks like, see Recorded Future’s analysis of CVE-2022-0847 (Dirty Pipe).
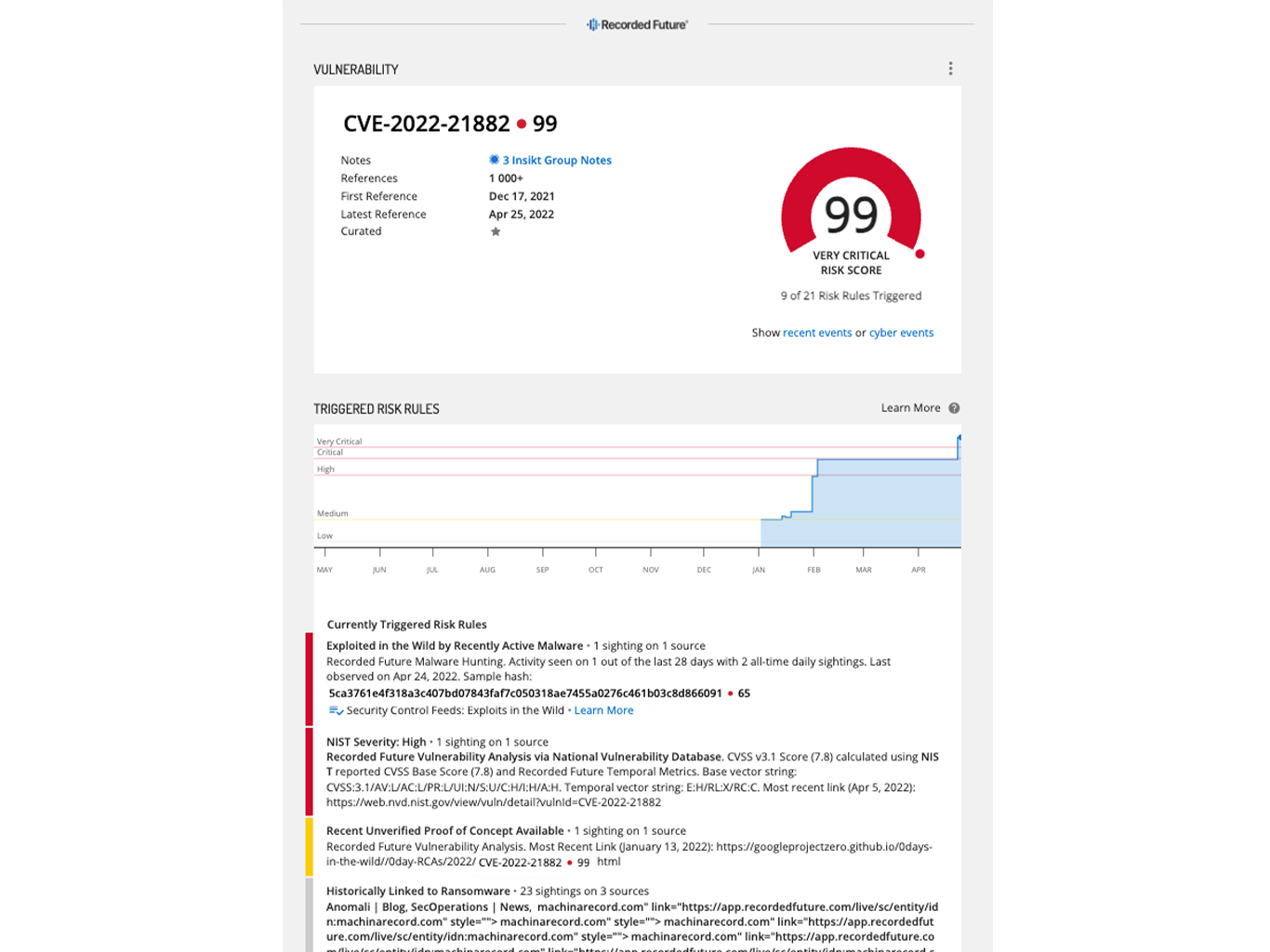
Vulnerability risk scores determine your priority patching list
Vulnerability risk scoring allows organizations to quickly understand a vulnerability’s likelihood of exploitation, based on key measures including observed exploitation in the wild, the existence of proof of concept code, and links to malware such as ransomware. Risk scores are a powerful tool for a vulnerability management analyst that allow them to quickly whittle down a long list of potential patches in order to focus on the essential, high-risk vulnerabilities.
However, risk scores should never be trusted blindly. It is imperative to have the evidence to justify and back up the score provided. Telling your IT counterparts that they need to patch now because a vulnerability has a 99 risk score will never be as impactful as telling IT they need to patch now because a vulnerability was recently exploited in the wild by ransomware actors. Evidence is essential to justify decision-making at the speed your business needs to move.
Attack surface intelligence identifies your organization’s vulnerability exposure
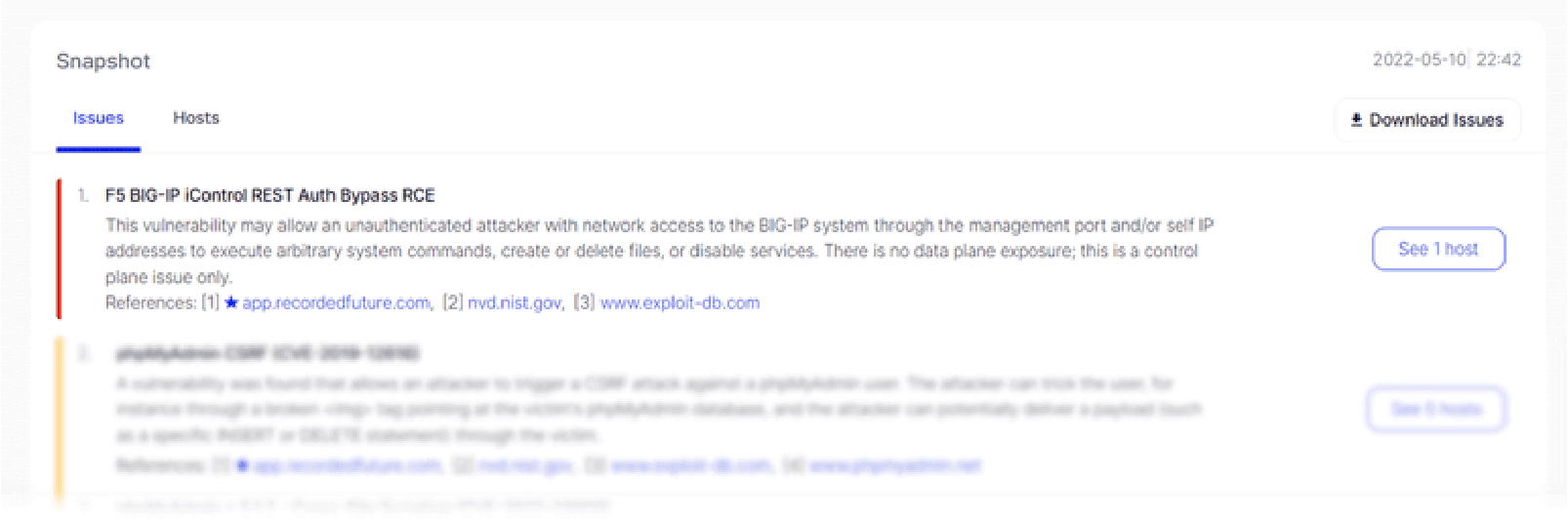
Let’s say you come across a news article (or use vulnerability intelligence) identifying a brand new vulnerability of major concern, such as the recent CVE-2022-1388 that affects F5 BIG-IP systems. The logical next step is to determine your own organization’s exposure to this vulnerability. But that’s much easier said than done.
You can, and should, use vulnerability scanning to find instances of this vulnerability where possible, but that process on its own might not be enough. Most organizations do not have a strong handle on asset management. In other words, most organizations have assets their vulnerability management teams don’t know about, making it extremely difficult to fully remediate a vulnerability from your organization.
That’s where Attack Surface Intelligence comes into play. Attack Surface Intelligence makes it easy to discover your organization’s assets, as well as how vulnerable those assets might be.
Hunting packages help you find threat actors actively exploiting the vulnerability in your environment
No organization is perfect, and sometimes that means patching high-risk vulnerabilities more slowly than you’d like. If you are concerned that your organization may have already been compromised, now is the best time for threat hunting. Traditionally, proactive threat hunting is done by very large organizations with mature cyber capabilities. However, it doesn’t need to be this way.
Recorded Future’s threat hunting packages provide users with detection mechanisms, including YARA, Snort, and Sigma rules to hunt for adversaries, malware, or traffic of interest. You can even integrate hunting packages directly into your SIEM or SOAR solution, making it easy to automate the detection of vulnerability exploitation in your environment. Recorded Future clients, for example, are able to use hunting packages included with the Dirty Pipe vulnerability report mentioned above to find potential instances of exploitation. This effectively turns your tier 1 analysts into tier 3.
Third-party intelligence identifies your third-party vulnerability exposure
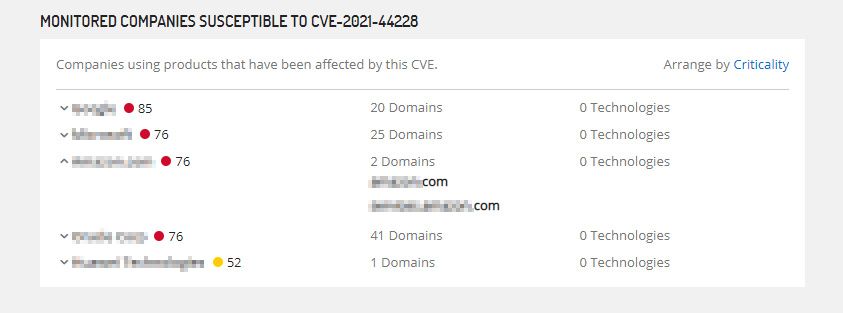
Every once in a while, a mega-vulnerability with potential for mass exploitation is discovered. Log4Shell, for example, affected millions of companies across the globe that utilized the extremely common log4j logging framework. This vulnerability was significant enough that companies concerned about exposure didn’t stop at their own risk, they looked at the risk of their exposure to this vulnerability via their third parties.
Third-Party Intelligence is a powerful tool to identify Internet-facing vulnerabilities that expose your third parties and you to risk. Instead of asking a third party what steps they’ve taken to mitigate vulnerabilities such as Log4Shell, you can verify the information for yourself. You can also use the information discovered to have more effective risk mitigation conversations with your third parties.
Get started with vulnerability intelligence
No matter whether your organization wants to use one or even all five types listed above, vulnerability intelligence can drastically improve the way your organization identifies, prioritizes, and mitigates vulnerability risk. And it’s simple to implement and start realizing immediate value.
If you’d like to learn more about how your team can use vulnerability intelligence to reduce risk, request a demo today.
Related
